Hot Potato – Windows 7,8,10, Server 2008, Server 2012 Privilege Escalation in Metasploit & PowerShell

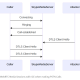
How Potato works
Hot Potato (aka: Potato) takes advantage of known issues in Windows to gain local privilege escalation in default configurations, namely NTLM relay (specifically HTTP->SMB relay) and NBNS spoofing.
If this sounds vaguely familiar, it’s because a similar technique was disclosed by the guys at Google Project Zero – https://code.google.com/p/google-security-research/issues/detail?id=222 . In fact, some of our code was shamelessly borrowed from their PoC and expanded upon.
Using this technique, we can elevate our privilege on a Windows workstation from the lowest levels to “NT AUTHORITY\SYSTEM” – the highest level of privilege available on a Windows machine.
More info, please visit here.
Potato in command line
Stephen Breen has developed an executable file that can automate these attacks and can execute any commands on the target system.
Potato is associated with a DLL. Once the DLL is running by the system, the potato can run under system commands and then perform the following operations to enable NBNS spoofing locally (127.0.0.1).
At this time the http communication is sent through the configuration of the browser (such as the use of the company’s proxy settings), we can see from the following figure we will complete the attack, and can be higher authority to execute system commands.
User has been added to the Administrators group, which means that our attack has been successful.
Potato in metasploit
Of course, you can use the MSF to attack, and then get a system with the authority of the meterpreter session, not just in the management group to add a user. Of course, you need to put Hot Potato’s exp and msf generated back doors on your target machine.
Before we get started, we get a shell with a low privilege in another window, run pentestlab3.exe, and use the handler module in msf to accept the connection in the window just now.
Be sure to open the second shell because it is used for Hot Potato in the HTTP communication process to avoid waiting time, and open the browser to communicate.
In the first shell, we execute Potato’s exp, slightly modify its execution command, let him run our backdoor “pentestlab3.exe”:
Open the ie browser in the second shell so that the first shell can catch http traffic.
This will cause Hot Potato to create a system service through a different protocol (HTTP to SMB)
The 3rd Msf handler should be used to listen for system privileges to return the meterpreter shell.
Potato in Powershell
There is an alternative option that simulates the Hot Potato vulnerability in PowerShell, called Tater. The script is included in Empire, p0wnedShell and PS> Attack.
The script has been tested in the Windows 2008 Server R2 environment.
Reference
https://github.com/foxglovesec/Potato
Hot Potato – Windows Privilege Escalation
https://github.com/Kevin-Robertson/Tater