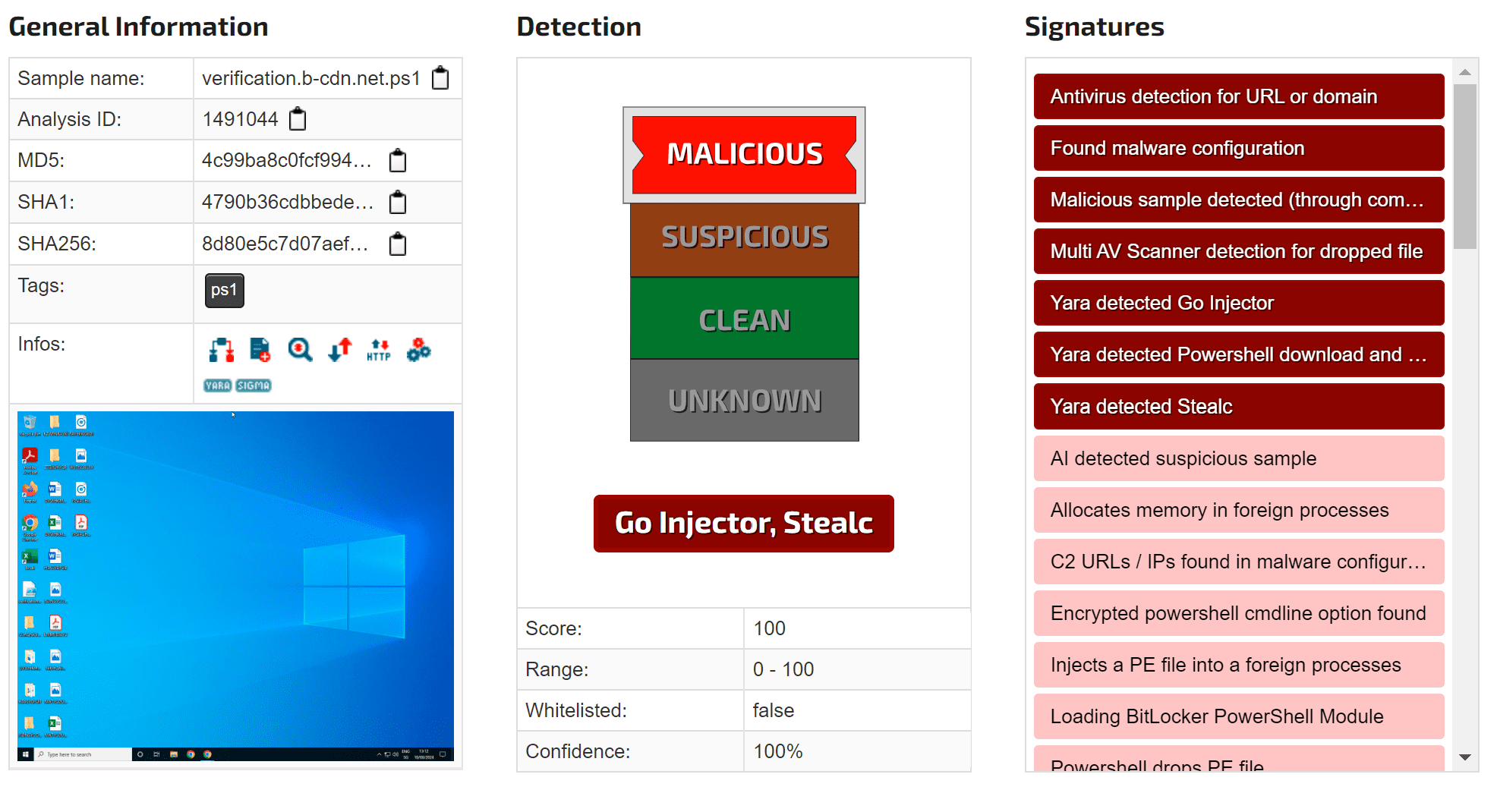
Image: Joesandbox
Recently, the eSentire Threat Response Unit (TRU) discovered a concerning new malware delivery chain involving a Go-based Injector that ultimately led to the execution of Lumma Stealer, a well-known information-stealing malware.
Lumma Stealer, first detected in August 2022, operates as a Malware-as-a-Service (MaaS) on Russian-speaking forums. Written in C, this stealer is designed to exfiltrate sensitive information from victims’ systems, including cryptocurrency wallets, 2FA browser extension data, and other critical credentials. Its broad capabilities and customizable nature have made it an attractive tool for cybercriminals looking to quickly gain access to valuable assets.
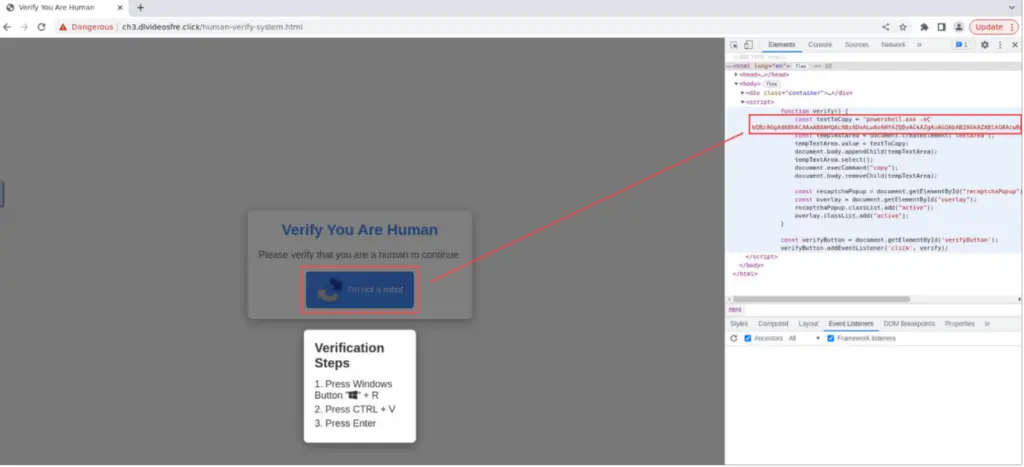
The attack observed by eSentire begins with users unknowingly navigating to a malicious website that presents a fake CAPTCHA page. This page copies a Base64 encoded PowerShell command to the user’s clipboard and instructs the victim to execute it via the Windows Run shortcut as part of a supposed verification step. This deceptive approach is designed to trick users into executing malicious commands under the guise of legitimate activity.
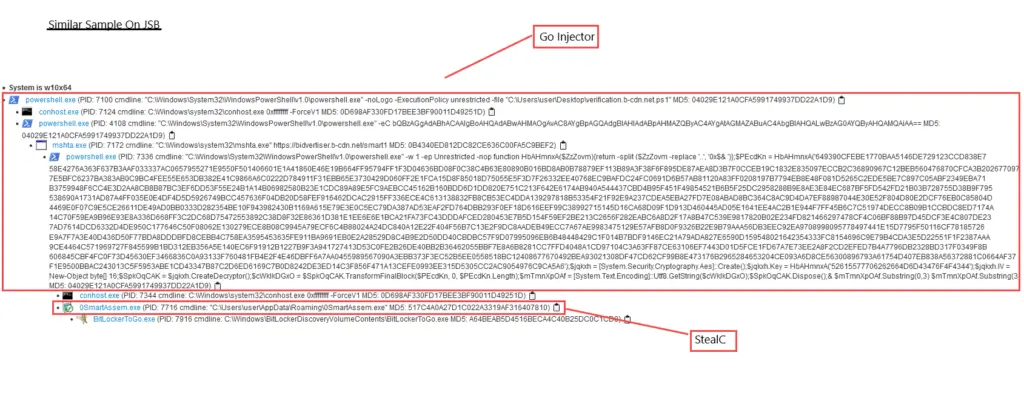
Once executed, the PowerShell command retrieves and runs a file named smart1.exe, which acts as a decoy but secretly executes the Go Injector payload. This injector, known as 0klevgrand.exe, is hidden within a seemingly harmless archive, smart1.zip, which contains legitimate DLL files to avoid raising suspicion.
Upon execution, the Go Injector performs several key actions to execute its malicious payload. It begins by collecting initial data about the host system, such as the hostname, username, and directory locations. From there, the injector employs a three-step process to deploy Lumma Stealer:
- CreateProcess: The Go Injector creates a new process, typically using BitLockerToGo.exe, in suspended mode.
- WriteProcessMemory: The injector writes the Lumma Stealer module into the memory space of the suspended process.
- ResumeThread: Finally, the process is resumed, but it now contains the malicious Lumma Stealer code, allowing the attacker to gain control over the victim’s system.
The entire injection process is designed to bypass detection, with encrypted payloads and the use of legitimate processes helping to evade traditional endpoint security solutions.
Once Lumma Stealer is executed, it targets a wide range of sensitive data on the victim’s system. The decrypted PE data shows typical Lumma Stealer behavior, including strings encoded in Base64, which it uses to communicate with its command-and-control (C2) servers. eSentire’s analysis was able to decrypt these strings, identifying several new C2 domains, allowing the team to track and investigate ongoing Lumma Stealer operations.
This malware is particularly dangerous due to its focus on stealing cryptocurrency and 2FA credentials, making it a significant threat to both individual users and organizations. The financial loss potential is high, and the use of Lumma Stealer in combination with Pay-Per-Install (PPI) services suggests that cybercriminals are increasingly using scalable, automated methods to distribute this malware to as many victims as possible.
During the investigation, eSentire’s team identified that the Go Injector had also been linked to other malware, including StealC, another data-stealing program.
Related Posts:
- LUMMA Malware: Cybercriminals Elevate Tactics with Fake Invoice Campaign
- Cybercriminals Turn Discord into Malware Playground with Lumma Stealer
- Cyber Alert: FortiGuard Labs Spot Lumma Stealer on YouTube
- Beware of Fake Browser Updates: BitRAT and Lumma Stealer on the Rise
- GoGra: New Go-Based Backdoor Targets South Asian Media