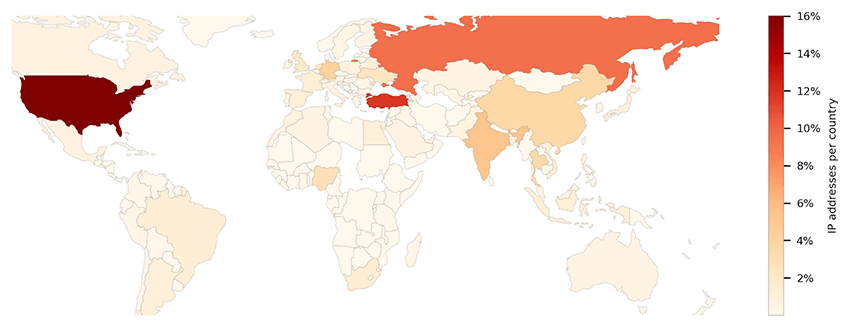
World distribution of systems infected with telegram-based infostealers | Image: Bitsight
Cybercriminals are increasingly leveraging Telegram as a platform not only for communication but also as a server for exfiltrating sensitive data stolen by infostealer malware. According to a recent report from André Tavares, a Threat Researcher at Bitsight Security Research, this alarming trend has significant implications for businesses and individuals alike, with Telegram playing a pivotal role in enabling cybercriminals to quickly and efficiently steal data and sell credentials on underground markets.
Telegram’s appeal among cybercriminals is driven by its simplicity, encryption features, and ease of use. Tavares explains that “Telegram has become a popular platform among cybercriminals, not only for messaging but for a wide range of illicit activities, including serving as a data exfiltration server for infostealer malware“. Telegram bots, in particular, have emerged as an effective tool for automatically uploading stolen data from infected systems, further streamlining the attack process.
Infostealer malware is designed to harvest all types of sensitive information from compromised systems. This includes credentials for VPNs, RDP, business services, banking, and social media, as well as passwords and cookies stored in browsers like Chrome and Firefox. “These logs are then fed into autoshop marketplaces, some of them known as ‘clouds of logs,'” the report notes. Even outdated credentials can be valuable in attacks such as credential stuffing, where attackers exploit password reuse to gain unauthorized access to systems.
Tavares highlights that between October 2024 and now, the team observed 5 million logs containing stolen credentials from 1,800 Telegram bots. These logs include victim IP addresses, domain names, and other sensitive data. “The most infected countries are the USA, Turkey, and Russia, followed by India and Germany“.
The report outlines the structure of the infostealer ecosystem, where different types of threat actors exploit stolen data. At the lower end of the spectrum are script-kiddies, often inexperienced hackers looking to make quick money or cause chaos. At the other end are Initial Access Brokers (IABs), who use stolen credentials to gain footholds in corporate environments before selling access to other cybercriminal groups, such as ransomware operators.
Some infostealer families, such as SnakeKeylogger and AgentTesla, dominate the malware landscape. Tavares notes that “SnakeKeylogger has now clearly taken the lead” in terms of the volume of logs collected, with AgentTesla declining after losing access to its servers. The stolen data, often exfiltrated via Telegram, can include critical information, such as corporate employee credentials, making it easier for attackers to bypass traditional security measures and initiate more sophisticated attacks.
Given the growing threat, Tavares recommends that organizations take proactive steps to mitigate risks. One simple but effective measure is to block access to the Telegram API in corporate environments that have no business use for the platform. This would prevent malware from using Telegram as a means to exfiltrate data. “This single action can prevent Telegram based infostealers from exfiltrating data,” Tavares writes.
Additionally, organizations should prioritize multi-factor authentication (MFA) across all user accounts to add a critical layer of security. Regular monitoring for compromised credentials is also essential, as it enables swift responses to potential breaches before attackers can exploit the stolen data.
The use of Telegram bots for data exfiltration by infostealers represents a growing and dangerous trend in cybercrime. As these malware families continue to evolve and capitalize on platforms like Telegram, businesses must remain vigilant and enhance their cybersecurity strategies. “Cybercriminals in general, and the infostealer ecosystem in particular, are increasingly taking advantage of legitimate services,” the report concludes, emphasizing the importance of adapting defenses to protect against these emerging threats.
Related Posts:
- Crafty Infostealer Campaign Leverages Fake Adobe Reader Installer, Advanced Tricks to Evade Detection
- Inside a Python Infostealer: How Attackers Abuse Legitimate Platforms for Credential Theft