Image: Intrinsec
A recent report from Intrinsec, titled “China: Vulnerabilities as a Strategic Resource,” details how China systematically utilizes cybersecurity vulnerabilities as part of a broader national strategy. Through a dense legal framework and a national vulnerability management system, China appears to leverage vulnerabilities not only to safeguard its digital infrastructure but also to enhance its cyber capabilities on the global stage.
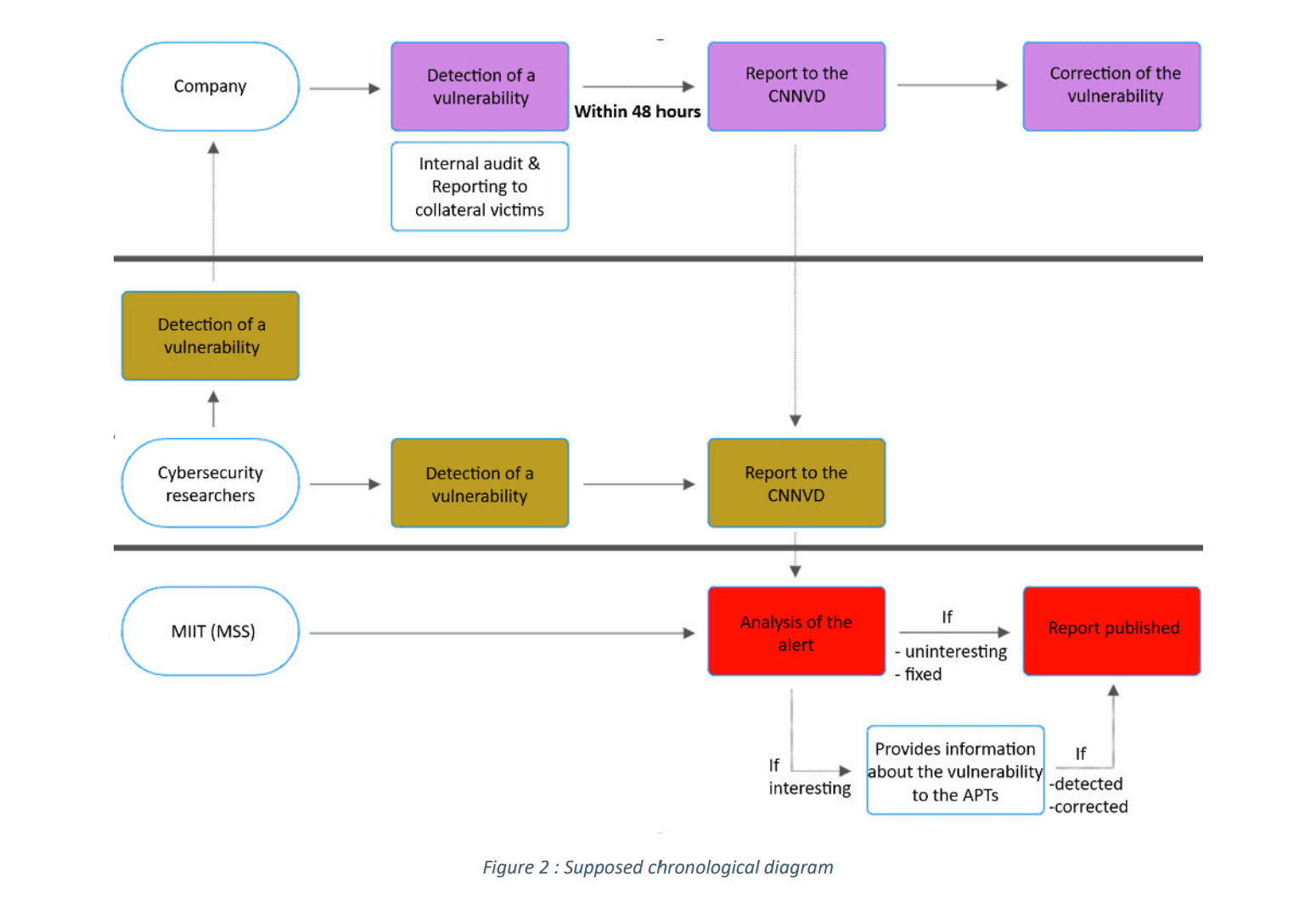
At the core of China’s vulnerability strategy is the Regulation on the Management of Network Product Security Vulnerabilities (RMSV). This regulation builds on the 2017 Cybersecurity Law, imposing strict requirements on organizations operating within China. According to Intrinsec, the RMSV “prohibits the illegal collection, sale or disclosure of vulnerability information that may endanger the security of information systems,” effectively centralizing control over vulnerability disclosure.
To comply, companies must notify Chinese authorities of any discovered vulnerabilities within 48 hours and maintain records for six months. The RMSV also requires organizations to “correct any vulnerabilities discovered within 48 hours,” a demand that surpasses typical global standards and highlights China’s desire to secure its digital ecosystem rapidly.
China’s RMSV mandates that cybersecurity researchers submit vulnerabilities to one of two national databases: the China National Vulnerability Database (CNVD) or the China National Vulnerability Database of Information Security (CNNVD). The report notes that CNNVD, managed by a government entity, has often been suspected of exploiting vulnerabilities for state purposes. Intrinsec’s report indicates that “the CNNVD encourages the submission of a POC that could lead to an ‘easy reproduction’ of the vulnerability,” with rewards granted based on the quality of the submission.
This database structure enables China to retain undisclosed vulnerabilities for potential use in cyber-operations, a strategy that aligns with the government’s focus on protecting its population and territory against cyber threats, while paradoxically being linked to numerous state-backed intrusion campaigns.
The RMSV’s extensive reach impacts foreign organizations, too. China’s regulations on vulnerability disclosure are so stringent that, according to Intrinsec, they have created a “compliance headache for businesses,” especially those required to disclose vulnerabilities while minimizing their global exposure. Compliance is enforced with severe penalties, ensuring that the RMSV remains a tool for both domestic control and international leverage.
With events such as the Matrix Cup hacking contest, China fosters an environment that encourages vulnerability discovery while restricting researchers’ participation in international forums. By nurturing in-country expertise and minimizing the outflow of technical knowledge, China appears to be building an internal cybersecurity talent pool that directly feeds into its national objectives.
Intrinsec’s report suggests that China’s cybersecurity approach may serve both defensive and offensive purposes. This legal infrastructure allows China not only to protect its citizens from external threats but also to potentially exploit vulnerabilities in foreign systems. Through tactics like “legal and technical measures” and controlling the narrative around cyber threats, China positions itself as both a defender of national stability and a potential wielder of cyber power.
As Intrinsec concludes, China’s use of vulnerabilities as a strategic asset underscores the complex interplay of security and statecraft in the digital age. By leveraging cyber laws as tools of sovereignty and influence, China continues to reshape the global cybersecurity landscape to align with its national priorities.
Related Posts:
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- Inside China’s State-Sponsored Hacking Competitions: Talent Spotting and Global Outreach
- South Korea set up research center dedicated to the application of artificial intelligence to national defense projects
- Chinese hackers attack Australian national universities, threatening national security
- China Targets U.S. Tech Startups through Investments, NCSC Reveals