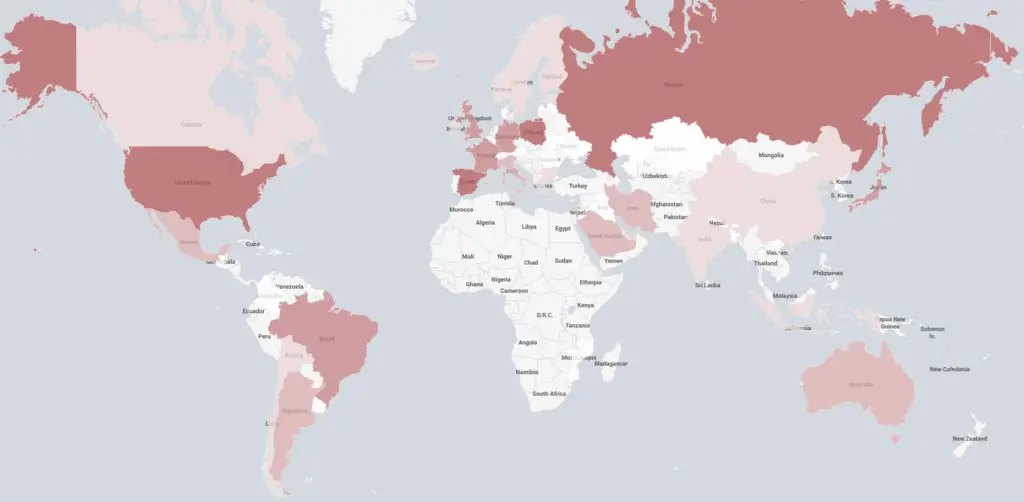
The target IP location mapping results | Source: Trend Micro
A newly discovered IoT botnet has been linked to a series of large-scale distributed denial-of-service (DDoS) attacks targeting organizations worldwide, including major Japanese corporations and financial institutions, according to a report by Trend Micro Research. This botnet, leveraging malware derived from Mirai and Bashlite, exploits remote code execution vulnerabilities and weak device passwords to infect IoT devices and orchestrate its attacks.
Trend Micro observed the botnet’s command-and-control (C&C) server directing DDoS commands targeting entities across Asia, North America, and Europe. This botnet has been “continuously observed launching DDoS attack commands since late 2024,” the report states, adding that attacks caused temporary connection disruptions for several targeted organizations.
The malware propagates through vulnerable IoT devices, such as wireless routers and IP cameras. Once infected, devices execute payloads that connect to the botnet’s C&C server to await attack commands. Notably, the malware disables watchdog timers to ensure uninterrupted operations during resource-intensive DDoS attacks.
The botnet supports a variety of DDoS techniques, as detailed in the report:
- SYN Floods: Overwhelming target servers with TCP SYN packets.
- ACK Floods: Sending massive ACK packets to disrupt server responses.
- Stomp Attacks: Using Simple Text Oriented Messaging Protocol with randomized payloads.
- GRE Attacks: Exploiting the General Router Encapsulation protocol.
Between December 2024 and January 2025, the botnet targeted organizations across multiple sectors, with notable differences in attack methods between Japanese and international targets. For instance, stomp commands accounted for 21% of attacks in Japan, compared to 7% for international targets. Conversely, GRE-based attacks were more common internationally.
The primary victims included industries in information technology, finance, and transportation. International targets were predominantly within the information and communication sector, accounting for 34% of attacks.
The botnet’s composition reflects a troubling trend of insecure IoT devices. Wireless routers made up 80% of infected devices, with TP-Link and Zyxel routers comprising the majority. IP cameras, such as those from Hikvision, accounted for 15%. India and South Africa were the top countries hosting infected devices, at 57% and 17%, respectively.
Trend Micro identifies key vulnerabilities contributing to the botnet’s growth:
- Default Settings: Unchanged default passwords make devices easy targets.
- Outdated Firmware: Legacy software with known vulnerabilities is routinely exploited.
- Insufficient Security Features: Many IoT devices lack adequate security measures.
Strengthening IoT device security is critical to combating the growing threat posed by botnets.
Related Posts:
- Attacker use DDoS attack to hit three major Dutch banks
- 35 Million Devices Vulnerable: Matrix DDoS Campaign Highlights Growing IoT Threat