ipa-medit
Ipa-medit is a memory search and patch tool for resigned ipa without jailbreak. It was created for mobile game security testing.
Motivation
Memory modification is the easiest way to cheat in games, it is one of the items to be checked in the security test. There are also cheat tools that can be used casually like GameGem and iGameGuardian. However, there were no tools available for un-jailbroken devices and CUI. So I made it as a security testing tool. Android version is aktsk/apk-medit.
Changelog v0.2.3
Installation
Requirements
- macOS
- You need to have a valid iOS Development certificate installed
- Xcode
- libimobiledevice/libimobiledevice
- libimobiledevice/ideviceinstaller
$ brew install –HEAD libplist
$ brew install –HEAD usbmuxd
$ brew install –HEAD libimobiledevice
$ brew install –HEAD ideviceinstaller
Install
Binary
Download the binary from GitHub Releases and drop it in your $PATH.
Manually Build
You need a Go compiler.
$ go install github.com/aktsk/ipa-medit@latest
Use
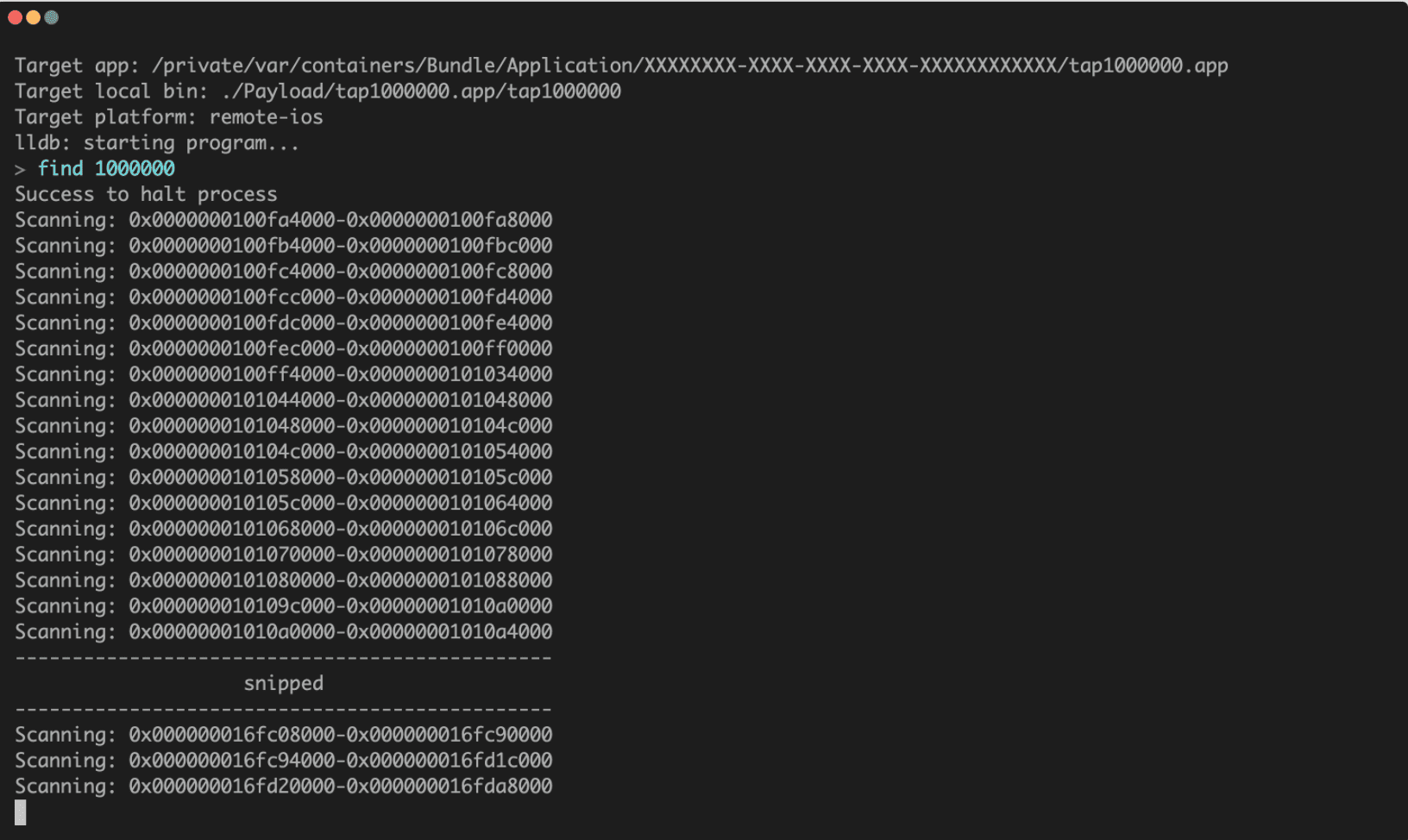
To launch it, specify the executable file path contained in the .ipa file for -bin and the bundle id for -id.
$ unzip tap1000000.ipa
$ ipa-medit -bin=”./Payload/tap1000000.app/tap1000000″ -id=”jp.hoge.tap1000000″
The target .ipa file must be signed with a certificate installed on your computer. If you want to perform memory tampering on third-party applications, please use a tool such as ipautil to perform the resigning.
$ ipautil decode tap1000000.ipa # unzip
$ ipautil build Payload # resign and generate .ipa file
Tutorial
Copyright (C) 2021 Akatsuki Inc.