
Google’s Threat Analysis Group (TAG) has issued a warning about APT42, an Iranian government-backed threat actor, and their escalating phishing campaigns aimed at high-profile individuals and organizations in Israel and the United States. These targeted attacks, particularly those directed at individuals associated with the U.S. presidential election, underscore the group’s sophisticated tactics and ability to adapt quickly to Iran’s political and military priorities.
APT42 has a long history of targeting influential figures and institutions, focusing on individuals with connections to government, military, and policy-making circles. Over the past six months, approximately 60% of APT42’s known activity has been concentrated in Israel and the U.S. Their targets include current and former government officials, political campaigns, diplomats, and prominent members of NGOs and academic institutions.
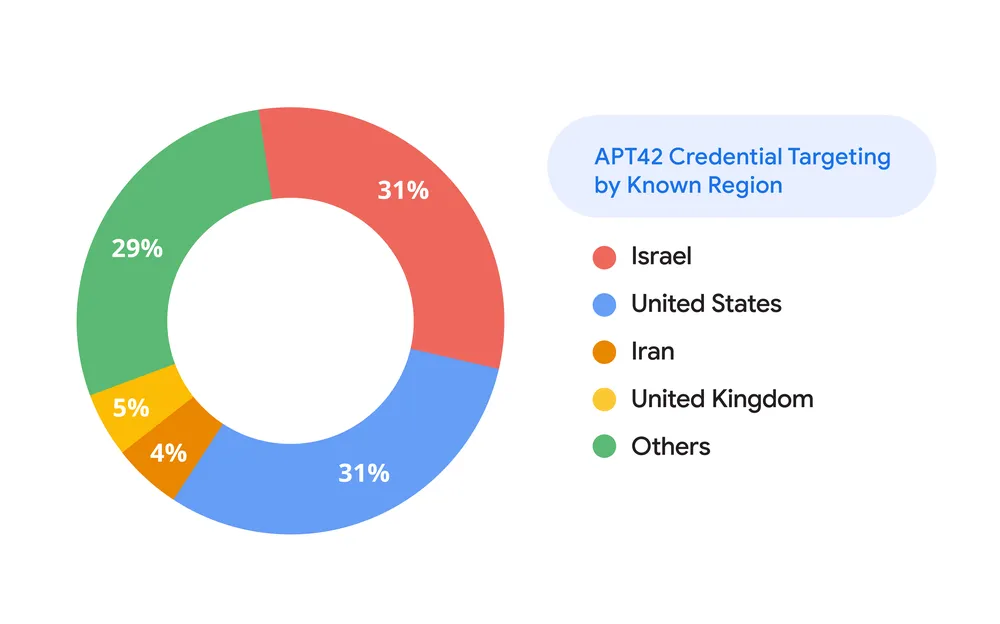
In April 2024, APT42 significantly escalated its efforts against Israeli targets. The group specifically sought out individuals connected to the Israeli military, defense sector, and diplomatic circles. Their tactics included using social engineering emails to masquerade as journalists seeking commentary on sensitive topics, aiming to engage their targets before launching more direct phishing attempts.
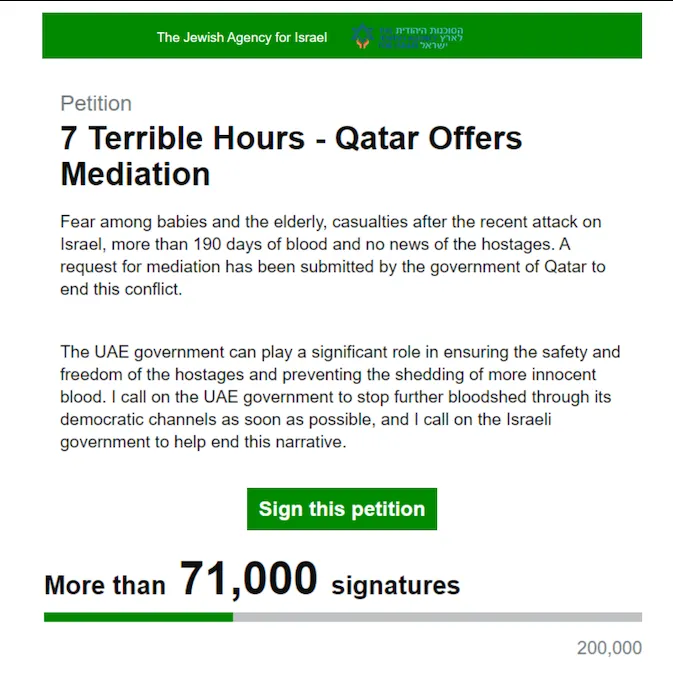
One notable campaign involved APT42 creating a fake Google Sites page, which appeared to be a petition from the Jewish Agency for Israel. The page, which was a phishing trap, used image files to embed the text and included a redirect URL that led to a phishing site. Google has since dismantled this infrastructure and added the malicious domains to its Safe Browsing blocklist.
APT42’s phishing campaigns have also extended to the U.S., with a particular focus on individuals affiliated with the 2024 presidential election. TAG detected a series of attempts in May and June 2024 to compromise the personal email accounts of individuals linked to both President Biden and former President Trump. Despite the group’s persistence, Google successfully blocked these attempts and secured the compromised accounts.
APT42’s tactics often involve the use of fake domains and email addresses that closely resemble legitimate organizations, a technique known as typosquatting. For instance, the group registered domains like “understandingthewar[.]org” and “brookings[.]email” to impersonate respected institutions and trick their targets into divulging credentials.
APT42 is known for its use of advanced phishing kits, such as the GCollection, which targets credentials from Google, Hotmail, and Yahoo accounts. This kit supports multi-factor authentication and has been consistently updated since its first appearance in January 2023. Another tool in their arsenal is the DWP phishing kit, a browser-in-the-browser technique often deployed through shortened URLs.
The group’s phishing efforts are supported by extensive reconnaissance, utilizing open-source tools to identify potential targets and tailor their attacks. They even go as far as researching the security settings of their targets’ email providers, allowing them to craft highly convincing phishing attempts that mimic the user’s geographic location and security behaviors.
In response to the increased threat from APT42, Google has taken multiple steps to disrupt the group’s operations. This includes resetting compromised accounts, suspending phishing domains, and enhancing detection mechanisms to prevent future attacks. Google has also referred APT42’s activities to law enforcement and continues to work closely with U.S. and Israeli authorities to mitigate the impact of these campaigns.
Related Posts:
- Iran’s APT42 Spies Target NGOs, Clouds in Espionage Campaign
- TikTok Hit by Zero-Day Attack: High-Profile Accounts Compromised
- Israel announces to investigate Facebook over Cambridge Analytica data breach
- 2024 US Election Faces Escalating Iranian Cyber Influence, MTAC Warns