Image: ClearSky
ClearSky Cyber Security has recently uncovered a new Iranian campaign targeting the aerospace industry with a deceitful “dream job” scheme. This campaign, dubbed the Iranian “Dream Job” campaign, involves the distribution of the SnailResin malware through enticing job offers aimed at professionals in the aerospace, aviation, and defense sectors.
This isn’t the first time a “dream job” scheme has been used for malicious purposes. ClearSky had previously uncovered a similar campaign in August 2020, orchestrated by the North Korean Lazarus Group. However, this time, the culprit is identified as TA455, a subgroup of the notorious Iranian threat actor known as “Charming Kitten.”
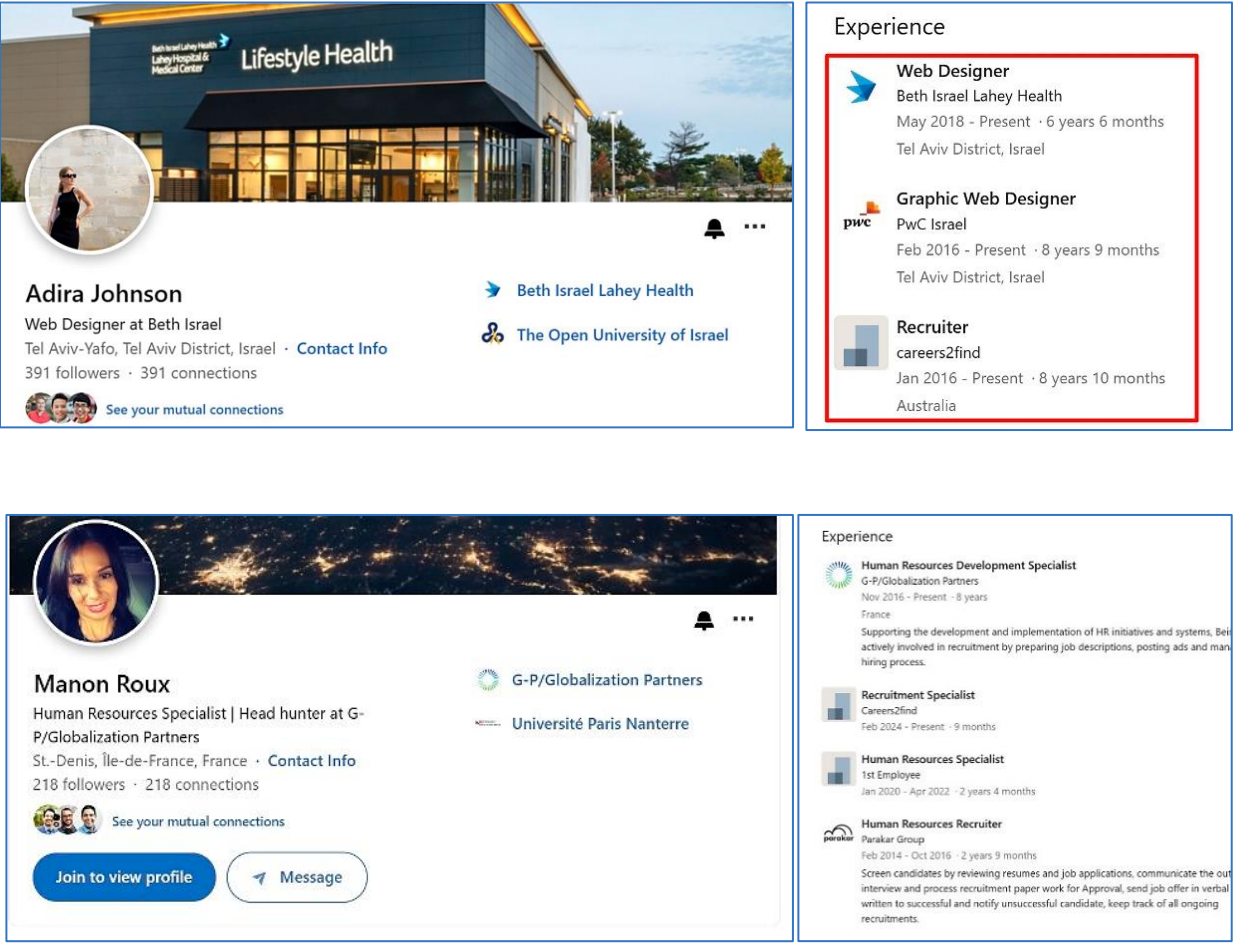
The attackers employ a sophisticated strategy, impersonating recruiters and leveraging legitimate platforms like LinkedIn to approach their targets. They create a seemingly trustworthy front, offering lucrative job opportunities to unsuspecting professionals. Once the target takes the bait, they are led to a malicious website disguised as a job recruiting portal. This website is used to deliver the SnailResin malware, which allows the attackers to gain access to sensitive information and potentially disrupt operations within targeted organizations.
ClearSky’s investigation has revealed intriguing connections between this campaign and previous attacks. The same LinkedIn profiles used by the attackers in earlier campaigns have resurfaced, further solidifying their association with TA455. To further evade detection, TA455 employs a blend of techniques, such as DLL side-loading, advanced obfuscation, and the use of GitHub to host encoded command-and-control (C2) instructions. By embedding C2 communication within seemingly benign GitHub files, TA455 manages to “blend in with legitimate traffic” and minimize detection.
Additionally, there are similarities between the tactics and tools used in this campaign and those employed by the North Korean Lazarus APT Group. This has led ClearSky to speculate that Charming Kitten may be intentionally mimicking the Lazarus group to conceal their activities or that there might be a concerning collaboration between these two threat actors.
This campaign has been ongoing since at least September 2023 and reflects Iran’s evolving cyber capabilities, especially in targeting sectors critical to national security. With persistent adaptation of tactics, TA455’s activities underscore the importance of vigilance in the aerospace, aviation, and defense industries, as adversaries continue to target sensitive information and infrastructure on a global scale.
Related Posts:
- Iranian APT hacker organisation falsifies Israeli security companies official website to implement phishing activities
- LockBit Ransomware Gang Exposes Boeing’s Data in Public Leak
- State-backed Curious Serpens Hackers Evolve with FalseFont Backdoor
- Chinese Engineer Indicted for Alleged Cyber Espionage Campaign Against US Aerospace Industry