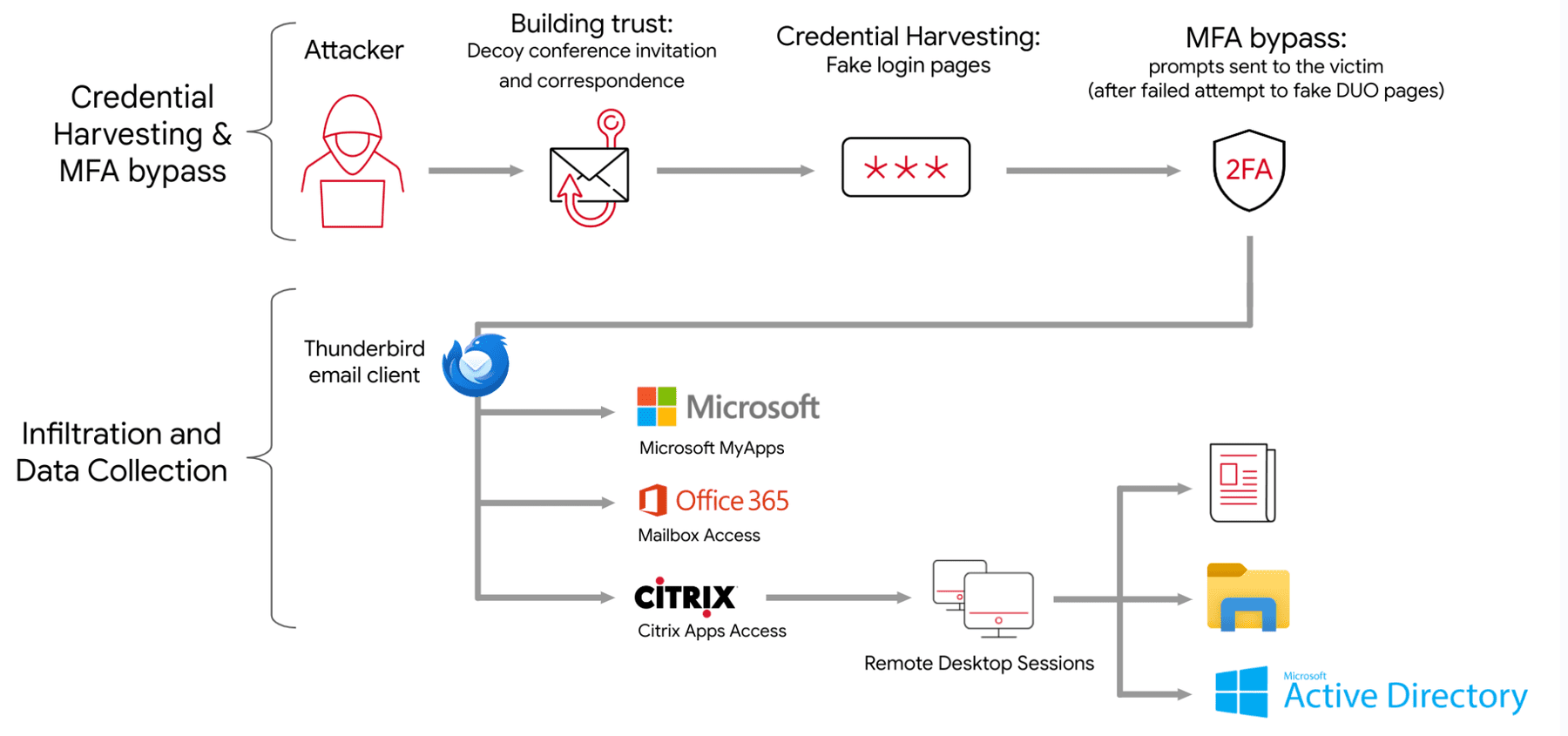
APT42 cloud operations flow of attack
A new report by cybersecurity firm Mandiant has revealed the inner workings of APT42, an Iranian state-sponsored actor believed to be operating under the aegis of the Islamic Revolutionary Guard Corps Intelligence Organization (IRGC-IO). This group has intensified its cyber espionage campaigns by leveraging advanced social engineering tactics to infiltrate networks of Western and Middle Eastern NGOs, media entities, academia, legal services, and activists.
APT42’s Arsenal: Social Engineering, Credential Harvesting, Custom Malware
The group’s success hinges on a combination of sophisticated social engineering, credential theft, and customized malware. APT42 operatives often impersonate journalists, conference organizers, or figures from well-known international organizations, carefully building trust with their targets over extended periods. They then deliver malicious links disguised as invitations to legitimate events or use decoy documents tailored to the victim’s interests. These links typically redirect to credential harvesting sites masquerading as popular services like Microsoft, Google, and Yahoo, where unsuspecting users unwittingly surrender their login information.
Utilizing both built-in features and open-source tools to fly under the radar, APT42 conducts its surveillance discreetly. This subtlety in execution allows the group to maintain a presence within compromised environments without detection. The report details recent malware-based operations involving two custom backdoors named NICECURL and TAMECAT. These tools, delivered through spear-phishing, not only facilitate initial access but also serve as potential launchpads for further malicious activities within the network.
Once credentials are compromised, APT42 focuses on infiltrating cloud environments, particularly Microsoft 365. The actors have demonstrated adeptness at bypassing conventional multi-factor authentication (MFA) defenses by exploiting push notification fatigue or using stolen credentials to create “app passwords” that effectively disable MFA. Inside the cloud environment, APT42 operators carefully search for and exfiltrate sensitive documents, emails, and other data of strategic interest to Iran, including information related to foreign policy and the Persian Gulf region.

Mandiant’s findings also highlight the broader implications of APT42’s activities, noting overlaps with other cyber actors like CALANQUE, Charming Kitten, and Yellow Garuda, among others. This not only underscores the interconnected nature of cyber threats emanating from Iran but also reflects a coordinated approach to cyber espionage that is deeply embedded in the nation’s intelligence operations.
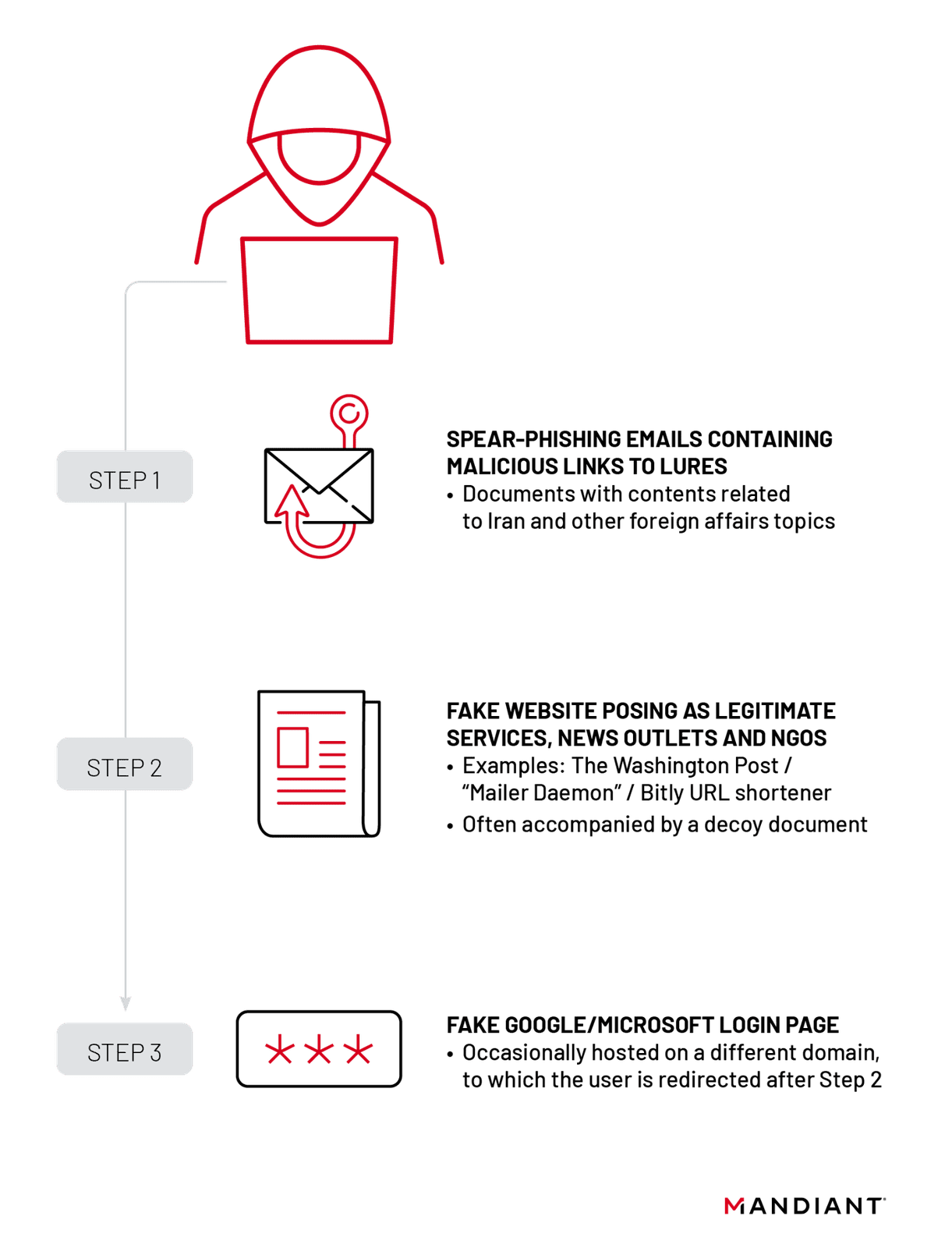
In a detailed analysis of APT42’s credential harvesting techniques, Mandiant outlines a three-step process predominantly targeting individuals and entities in policy, government, and media sectors. The group employs sophisticated spear-phishing emails from domains that cunningly masquerade as reputable news outlets and NGOs. These emails contain malicious links that redirect unsuspecting users to fake login pages, effectively capturing their credentials.
To counter the threats posed by APT42, we recommend several protective measures. These include the elimination of weak passwords, vigilant monitoring of system accesses, use of secure protocols like TLS/SSL, routine checks for suspicious files, and regular updates of device firmware. Additionally, restricting remote access to management interfaces and replacing devices after their support period ends are advised to enhance security postures.