JAW
An open-source, prototype implementation of property graphs for JavaScript based on the esprima parser, and the EsTree SpiderMonkey Spec. JAW can be used for analyzing the client side of web applications and JavaScript-based programs.
Features:
- Chromium-based crawler(s) enhanced with DevTools Protocol and Browser Extensions APIs
- Can collect webpages, scripts, events, DOM snapshots, network messages, web storage values, and cookies
- Implementation of hybrid Code Property Graphs (HPGs) for JavaScript
- Interactive detection or automatic exploration of vulnerable program behaviors
- Declarative Cypher queries
- ORM support with Python
- Self-contained, built-in queries to detect client-side CSRF and DOM Clobbering vulnerabilities.
- Design and perform custom security-related program analyses:
- Data flow analysis between pre-defined JavaScript sources and sinks
- Control flow and reachability analysis
- Resolution of DOM query selectors leveraging DOM snapshots
- Pattern matching via the abstract syntax tree
Overview of JAW
The architecture of the JAW is shown below.
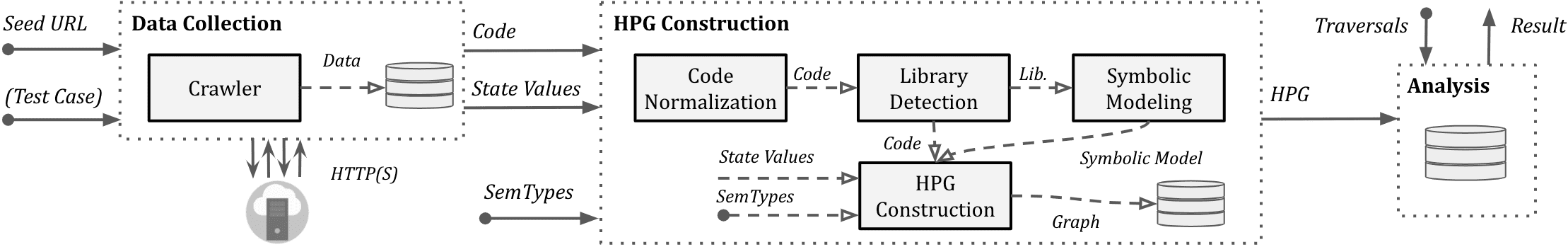
Inputs and Data Collection
JAW can be used in two distinct ways:
Option 1. Modeling and analyzing an arbitrary JavaScript program using JAW.
In this case, the only input to the tool is the path of the target JavaScript program in the file system.
Option 2. Analyzing a web application given a single seed URL.
JAW has a stand-alone, JavaScript-enabled web crawler (based on chromium) that can collect the application web resources, and use them for analysis.
Test Case Scripts. Optionally, a so-called test case script or a state script can be provided together with the seed URL of the application in order for the crawler to reach a certain, pre-defined state (e.g., logged in state) before the crawling session starts. For more information about how to create such state script, see here.
Crawler Output. The crawler outputs the JavaScript code as well as the State Values for each web page found.
JavaScript Code: for each web page found, JAW creates a single JavaScript file preseving the execution order of the program.State Values: state values are a collection of concrete values observed during the execution of a web page. These include the snapshot of the initial and rendered HTML page, fired events, HTTP requests and responses, and cookies. Optionally, the crawler can collect any JavaScript property accessible within the web page.
HPG Construction
JavaScript code and state values collected are next used to build a HPG. The built graph is imported into a Neo4j database.
Alternatively, the graph is built for the (arbitrary) JavaScript program given as the input by the tester
Optional Input: the HPG construction module can optionally be provided with a mapping of semantic types to arbitrary, tester-defined JavaScript language tokens. For example, a semantic type REQ can be assigned to all low-level, JavaScript functions that send an HTTP request (e.g., the Fetch API, or XMLHttpRequest).
Analysis and Outputs
Finally, the constructed Neo4j graph database can be queried for analysis. JAW provides a series of utility traversals for data flow analysis, control flow, and reachability analysis, or pattern matching, which can be leveraged for writing custom traversals for security analyses. Also, JAW includes traversals to detect client-side CSRF and DOM Clobbering vulnerabilities.
Install & Use
Copyright (C) 2023 Soheil Khodayari