jwtXploiter
A tool to test the security of JSON Web Tokens. Test a JWT against all known CVEs;
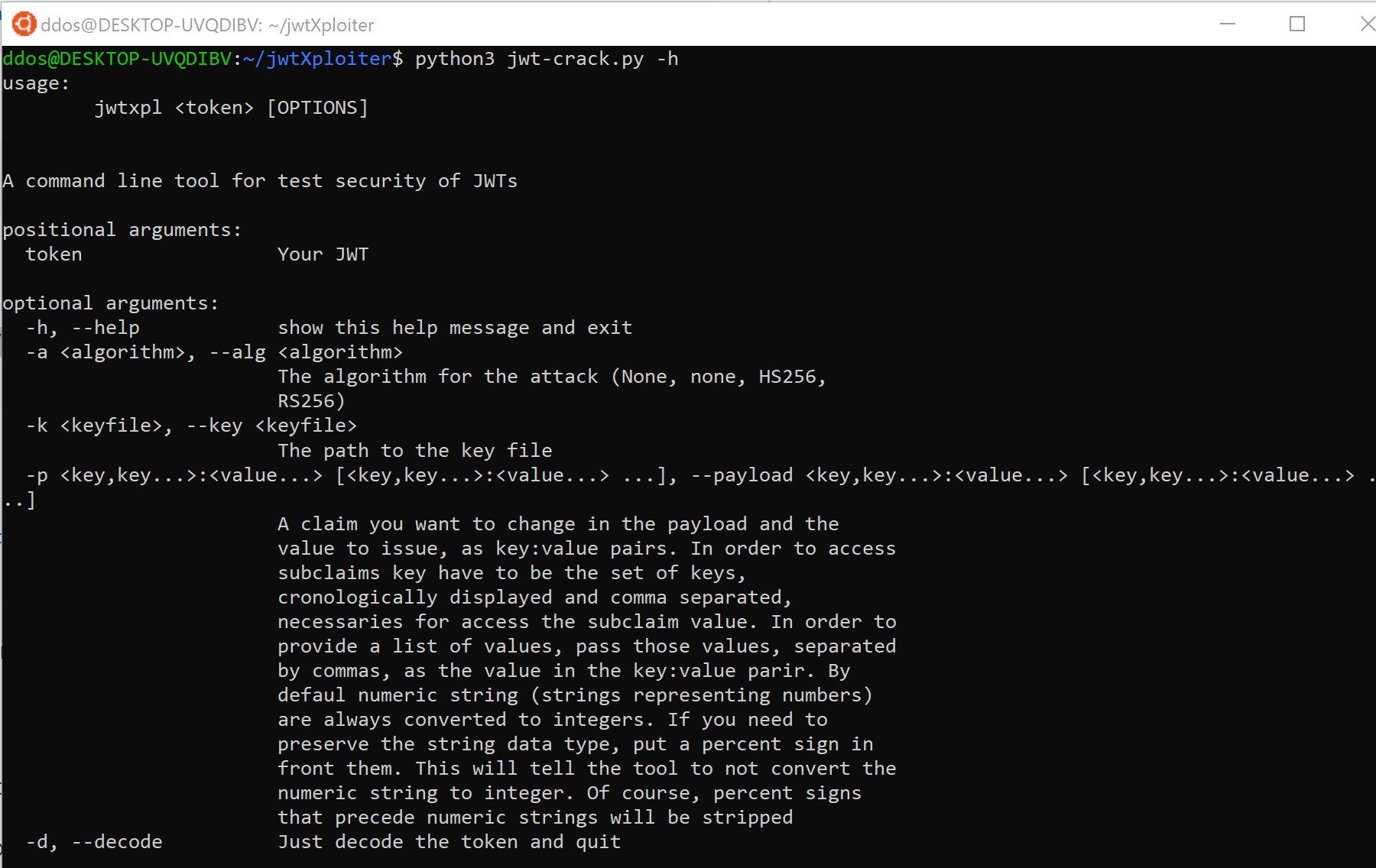
- Tamper with the token payload: changes claims and subclaims values.
- Exploit known vulnerable header claims (kid, jku, x5u)
- Verify a token
- Retrieve the public key of your target’s ssl connection and try to use it in a key confusion attack with one option only
- All JWAs supported
- Generates a JWK and insert it in the token header
- And much, much more!

Who this tool is written for?
- Web Application Penetration Tester / Bug Bounty Hunters
- This tool has been written with the aim of becoming a key part of pentesters toolkit.
- Devs who need to test the security of JWTs used in their applications
- CTF Players
- Not For Students
- Since this tool automates a lot of stuff, without forcing the user to know what’s happening under the hood, it won’t help you to understand the vulnerabilities it exploits.
To Know
- For attacks that generate a jwks file, you could find it in the current working directory. Remember to deletes such files in order to avoid conflicts.
- For the jku/x5u injection that needs to merge two urls (the server vulnerable url and your one), the HERE keyword is required.
- For redirect attacks, the keyword should replace the redirect url, e.g.
- http://app.com/foo?redirect=bar&some=thing –> http://app.com/foo?redirect=HERE&some=thing
- For jku/x5u injections via HTTP header injection attacks, the HERE keyword should be appended to the vulnerable parameter, without replacing its value, e.g.
- http://app.com/foo?param=value –> http://app.com/foo?param=valueHERE
- Also, in such cases, be sure to pass the server url and your one as comma-separated values.
- ‘/.well-known/jwks.json’ is automatically appended to your url in jku/x5u attacks. So make sure to place the jwks file under this path on your server.
- If you don’t want that to happen, use the –manual option, but this option is compatible only with –jku-basic and –x5u-basic so, you will need to manually craft the url and pass it to those options, even for attacks that exploit Open Redirect or HTTP header injection.
- Look at the wiki for detailed documentation.
Changelog v1.2.1 releases
FIXED
- FileNotFoundError when passing non existing key file to -k/–key #10
ADDED
- Quiet option to suppress warnings and colored output, keeping only the crafted token
ENANCHEMENT
- Added methods to spped up format conversions (der, pem, int)
- Algorithm now is not required anymore for verifying operations
Install & Use jwtXploiter
Copyright (C) 2021 DontPanicO