kaboom v1.0 releases: automates the penetration test
Kaboom is a bash script that automates the first two phases of a penetration test. All information collected is saved into a directory hierarchy very simple to the browser (also in the case of multiple targets).
Kaboom performs several tasks:
- Information Gathering
- Port scan (Nmap)
- Web resources enumeration (Dirb)
- Vulnerability assessment
- Web vulnerability assessment (Nikto – Dirb)
- Vulnerability assessment (Nmap – Metasploit)
- Automatic Vulnerabilities research (Searchsploit – Metasploit)
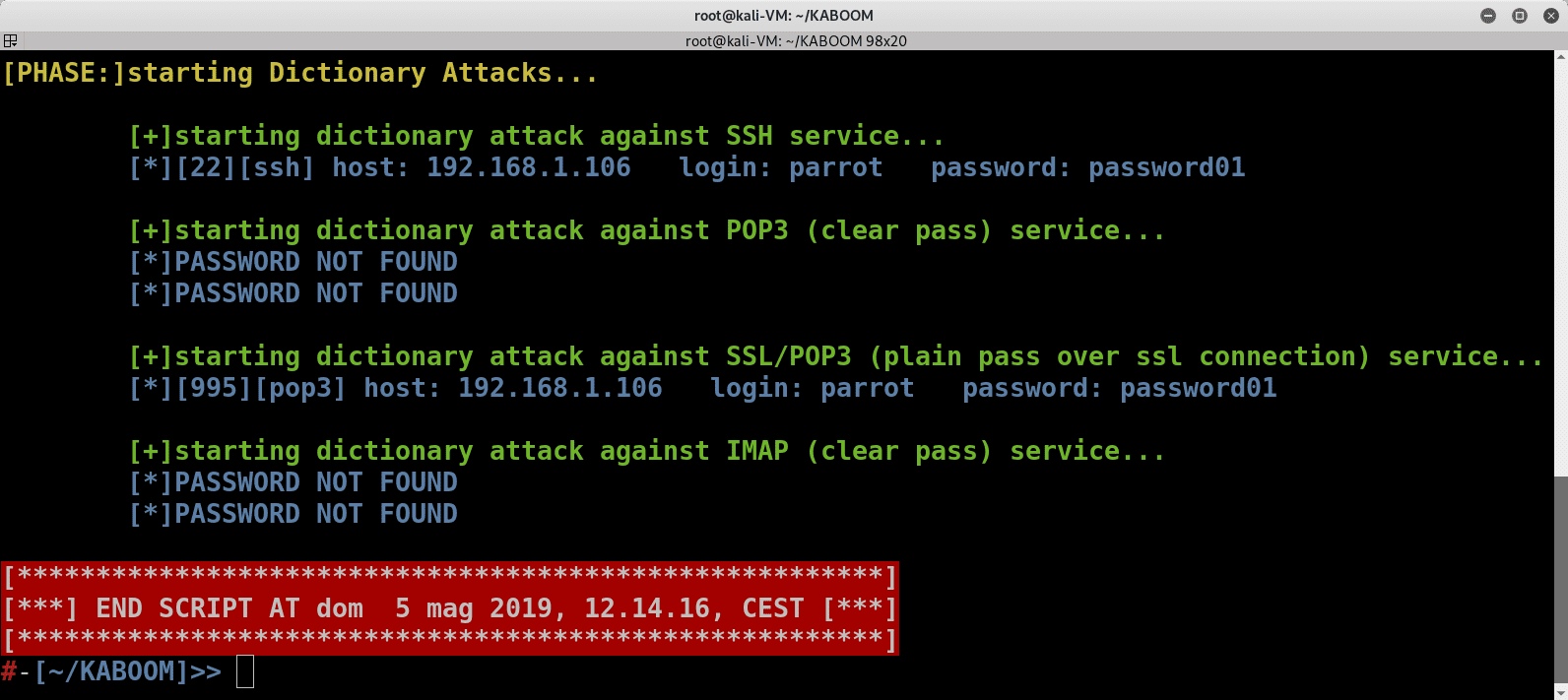
- Dictionary Attacks (Hydra)
- SSH
- POP3
- IMAP
- RDP
Feature
- Customization (see above)
- Multi-target specification
- You can specify up to 254 hosts (C-class network)
- New CLI interface
- More powerful Nmap scan
- Better directory hierarchy
- Automatic research of Metasploit module associated with CVE code found
- Recognition of services exposed on not canonical ports (ex: http on 7000)
- Print out and save credentials found
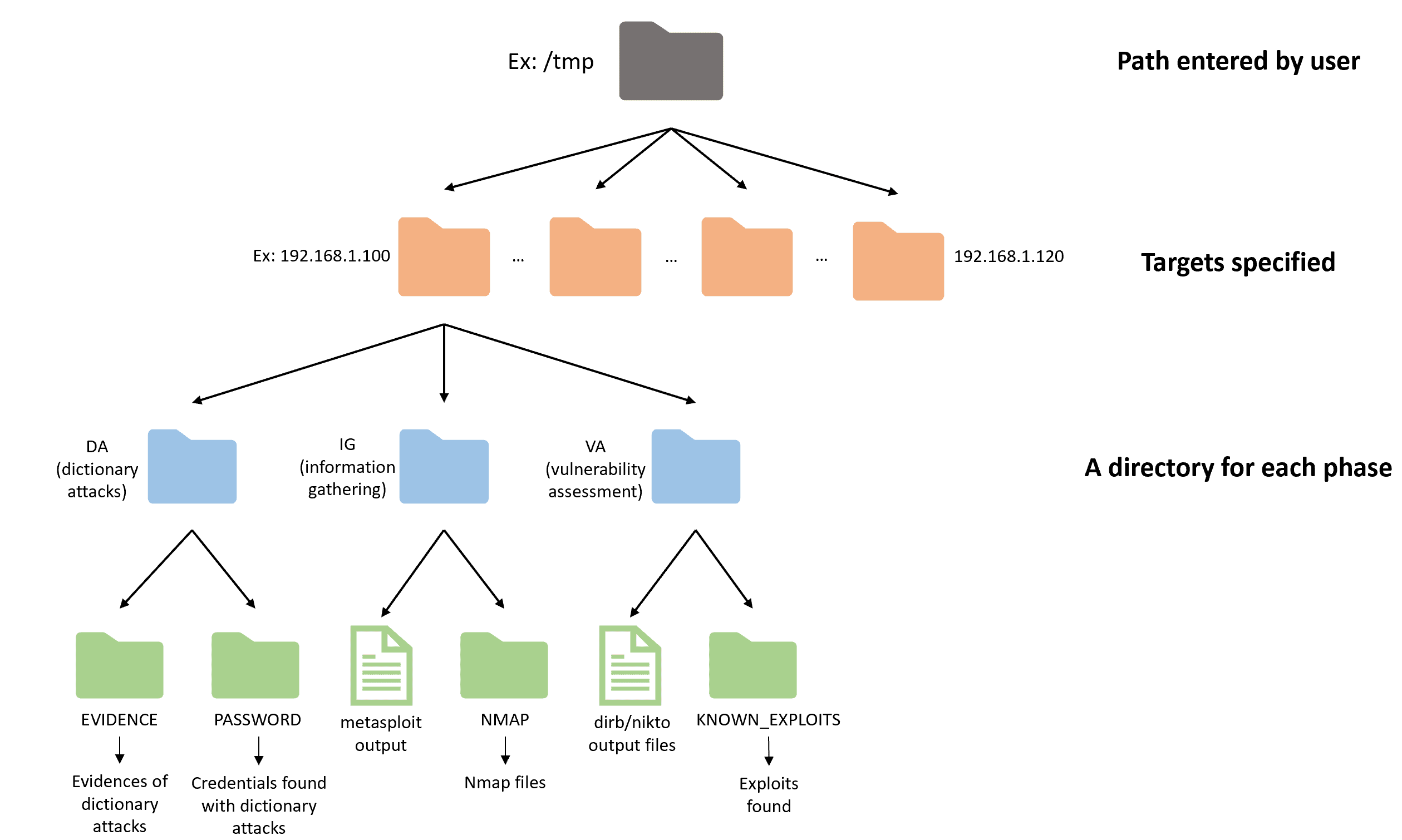
Directory Hierarchy
It saves the results of commands in this way:
Changelog v1.0
- Most bugs have been fixed. Now, it’s stable and versatile.
Download
git clone https://github.com/Leviathan36/kaboom.git
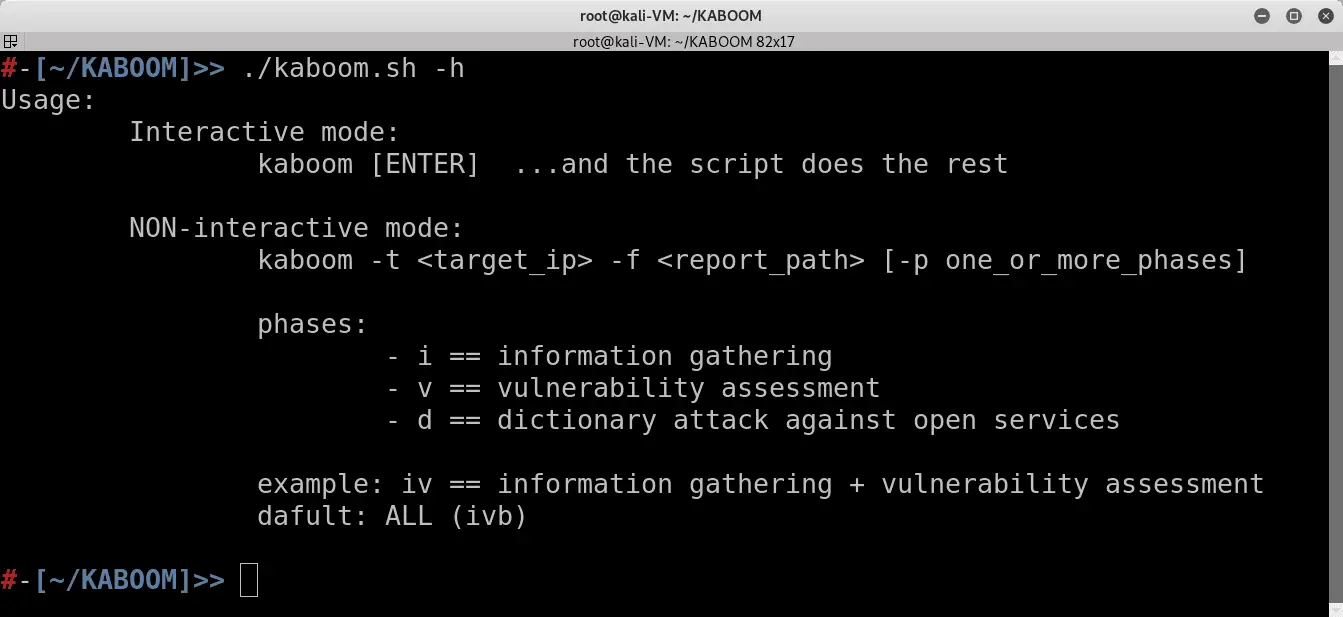
Usage
Kaboom can be used in two ways:
- Interactive mode:
kaboom [ENTER], and the script does the rest
- NON-interactive mode:
kaboom -t <target_ip> -f <report_path> [-p one_or_more_phases]
If you want to see the help:
Copyright (C) 2018 Leviathan36
Source: https://github.com/Leviathan36/