Kamerka-GUI
Ultimate Internet of Things/Industrial Control Systems reconnaissance tool
The main purpose of the ICS module of ꓘamerka is to map attack surfaces, in terms of Industrial Control Devices, for any country. Most used products, ports, protocols or cities with the biggest amount of exposed devices are part of the attack surface. It’s really important to understand what the device is used for and where it is located. (I will show how to geolocate some devices a bit later)
Full list of supported devices with corresponding queries
Install
git clone https://github.com/woj-ciech/Kamerka-GUI.git
cd Kamerka-GUI
pip3 install -r requirements.txt
Run
python3 manage.py makemigrations
python3 manage.py migrate
python3 manage.py runserver
In a new window (in the main directory) run celery worker celery -A kamerka –loglevel=info
In a new window fire up redis redis-server
And the server should be available on https://localhost:8000/
Search
Search for Industrial Control Devices in a specific country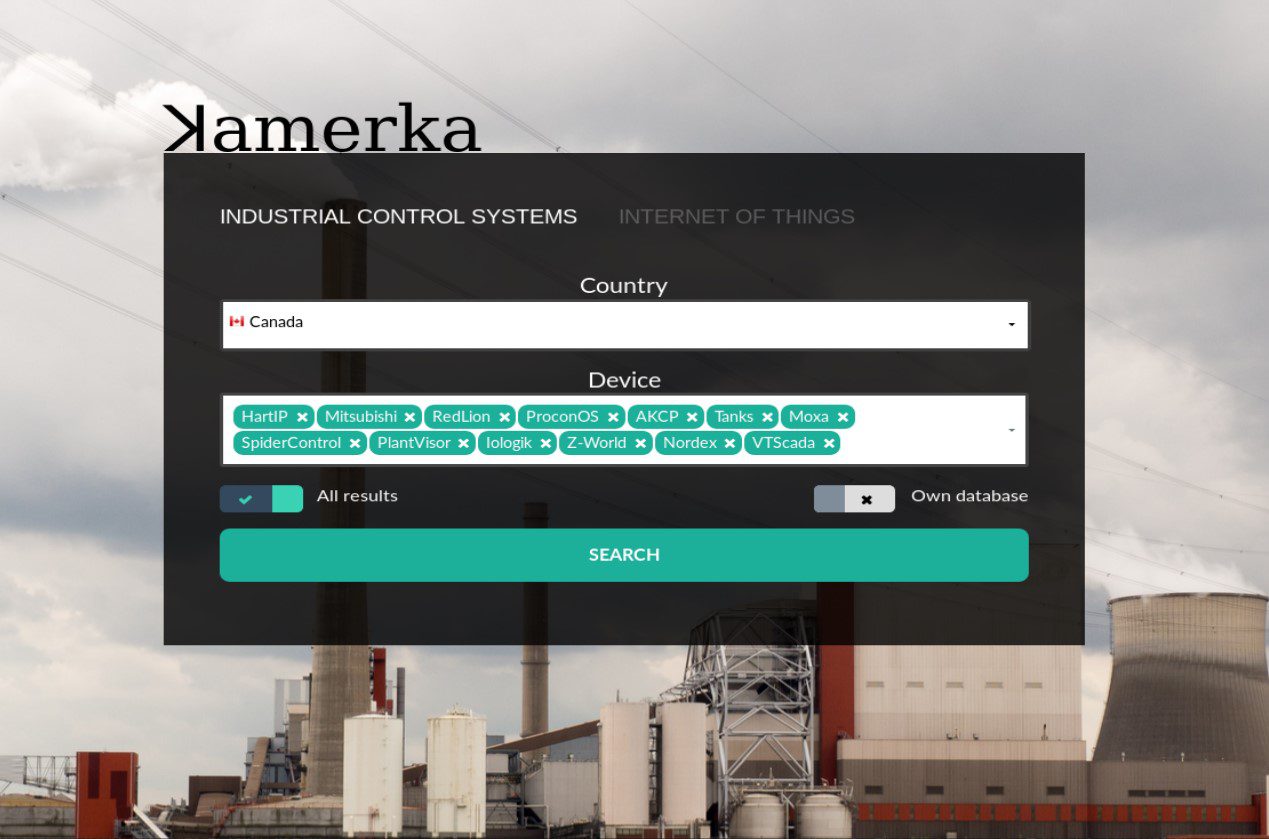
- “All results” checkbox means to get all results from Shodan if it’s turned off – only first page (100) results will be downloaded.
- “Own database” checkbox does not work but shows that is possible to integrate your own geolocation database. Let me know if you have access to better than Shodan’s default one.
Search for the Internet of things in specific coordinates
Type your coordinates in the format “lat,lon”, hardcoded radius is 20km.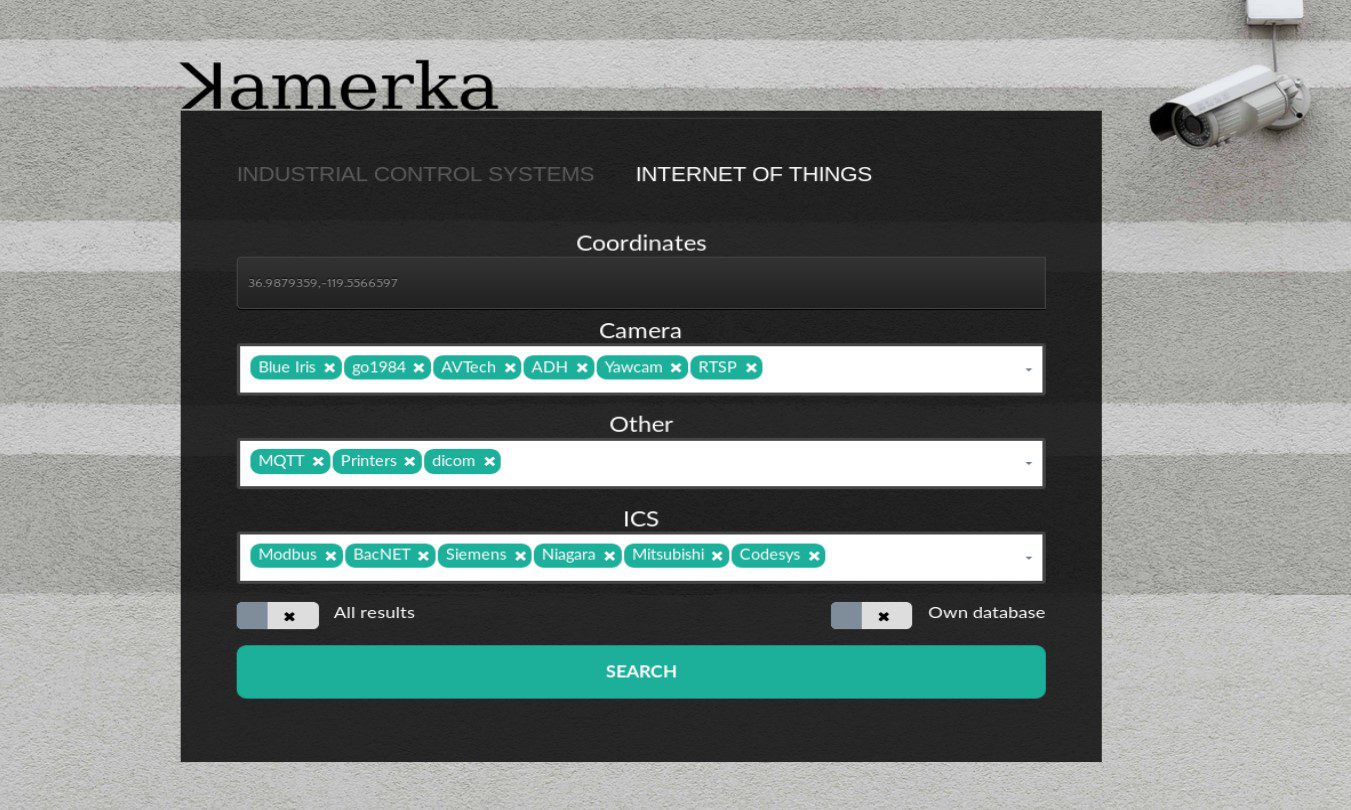
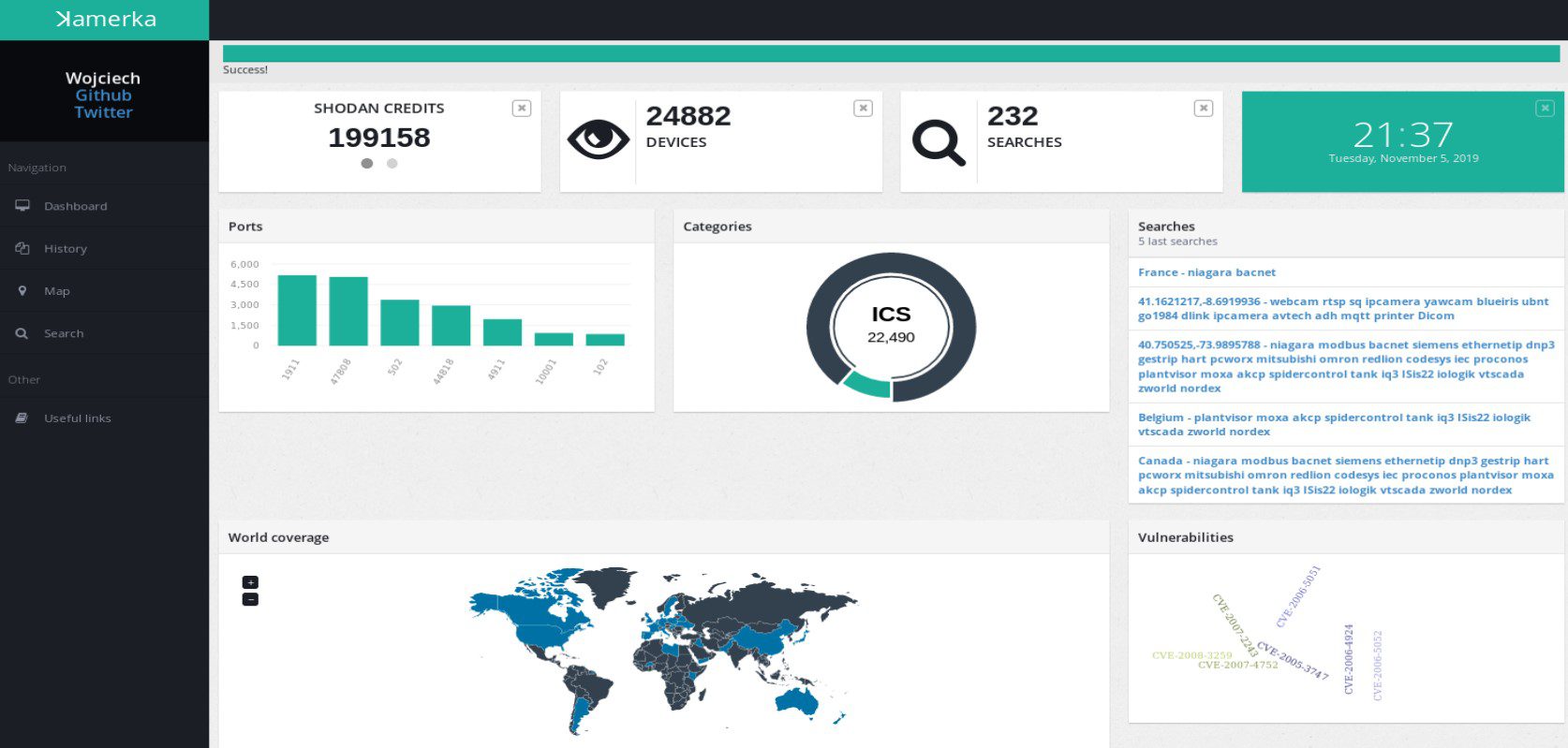
Dashboard
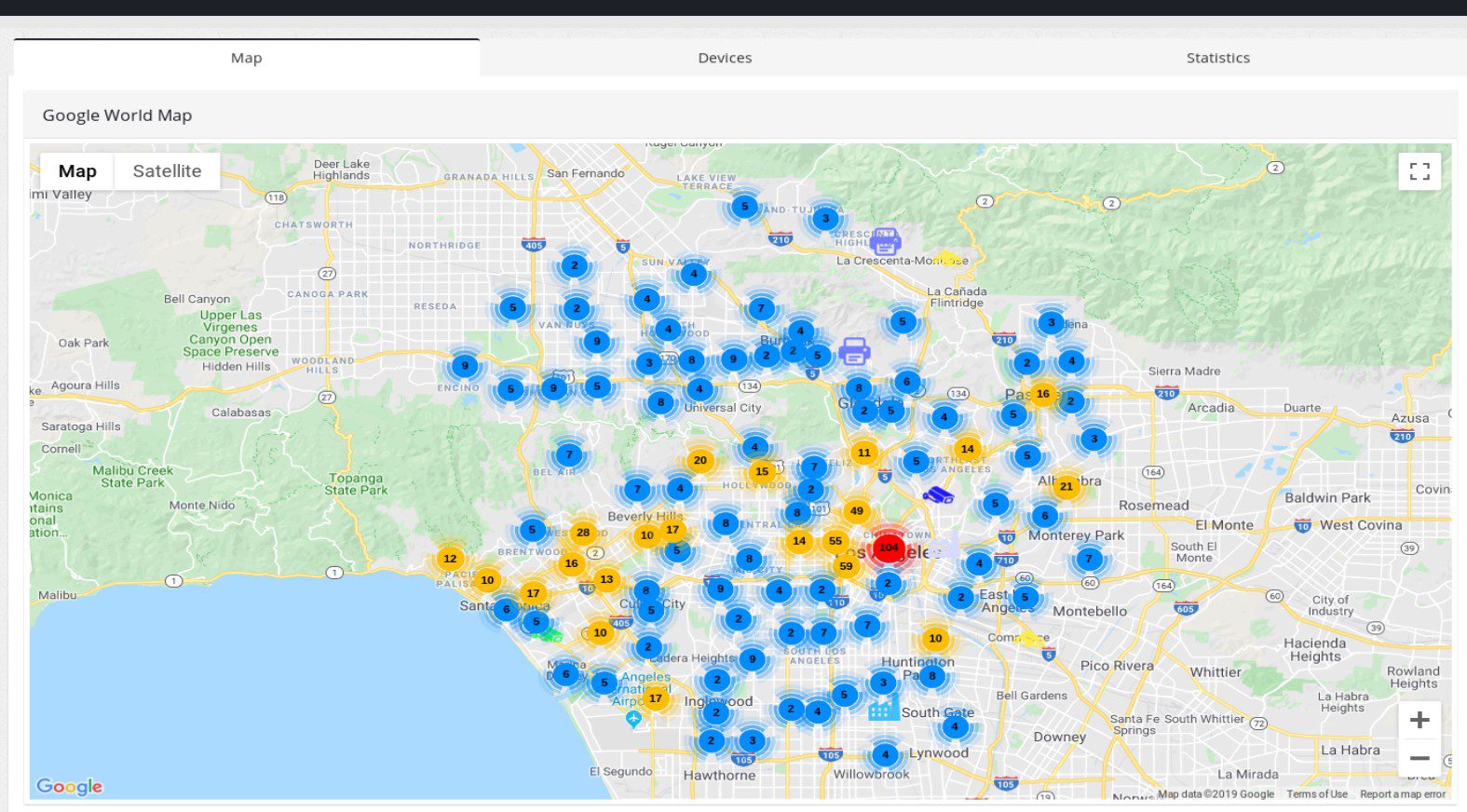
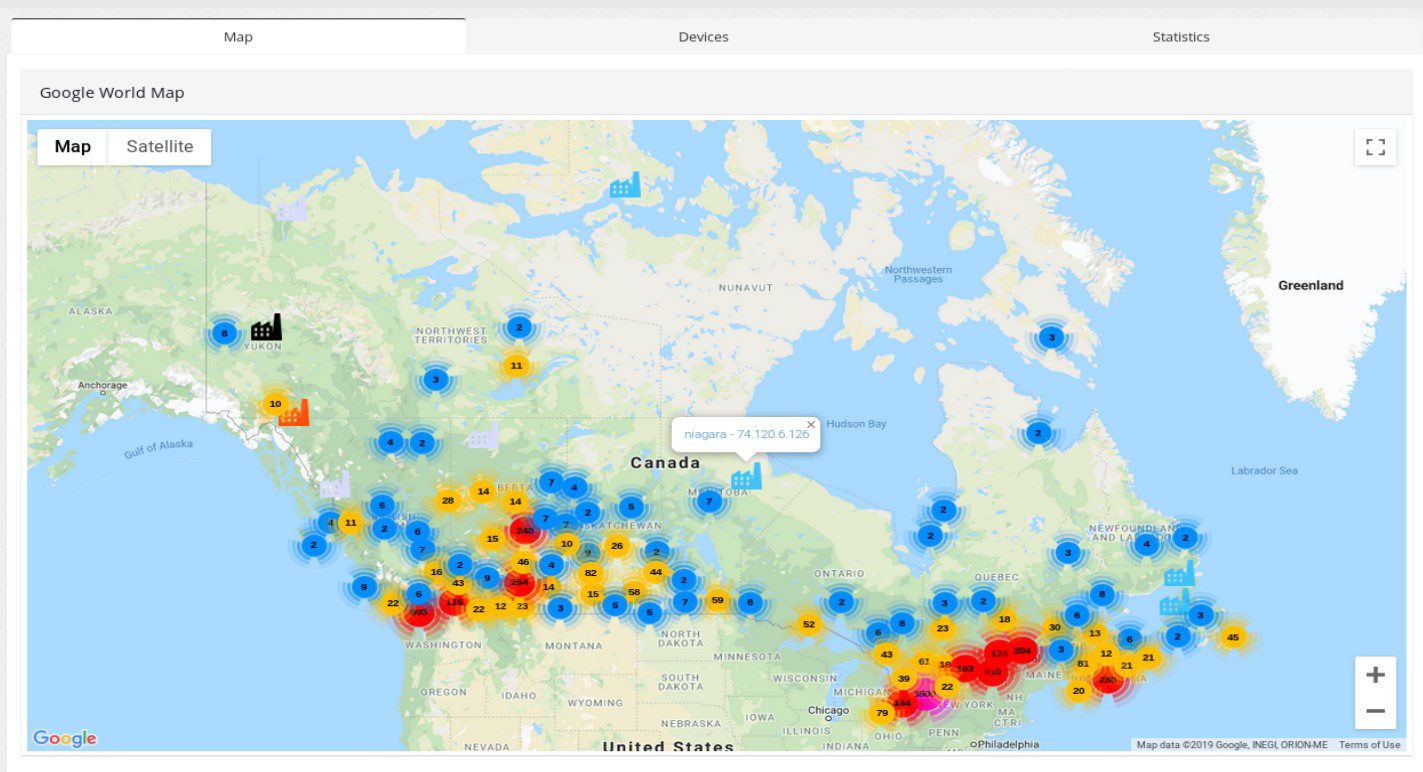
Maps
Los Angeles map
Industrial Control Systems in Canada
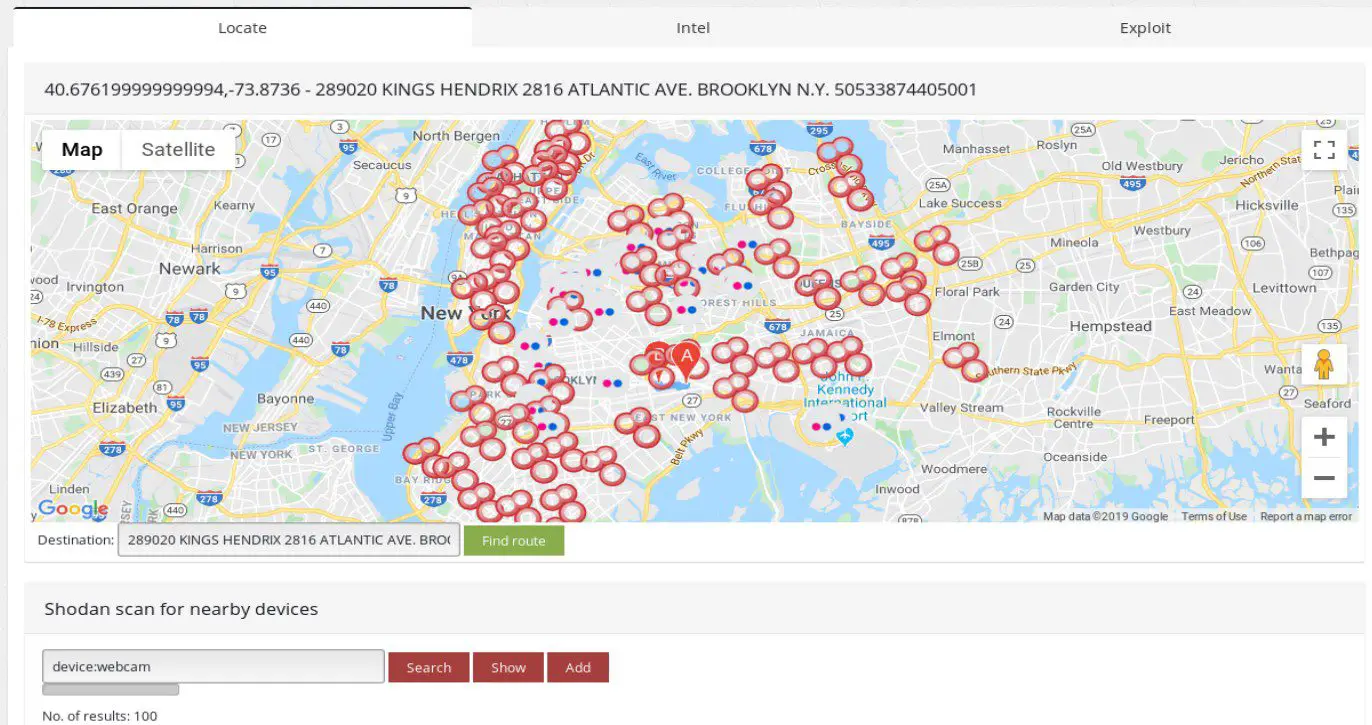
Device map & details
Read the writeup here.
Source: https://github.com/woj-ciech/