Kaspersky Lab’s security experts recently found a virus called Calisto malware, the guy who was the predecessor of the notorious Proton virus on macOS. Kaspersky wrote in the analysis that the virus was uploaded to VirusTotal after it created in 2016. Now, Calisto is still bypassing almost of anti-virus solutions, only recently have someone valued this issue.

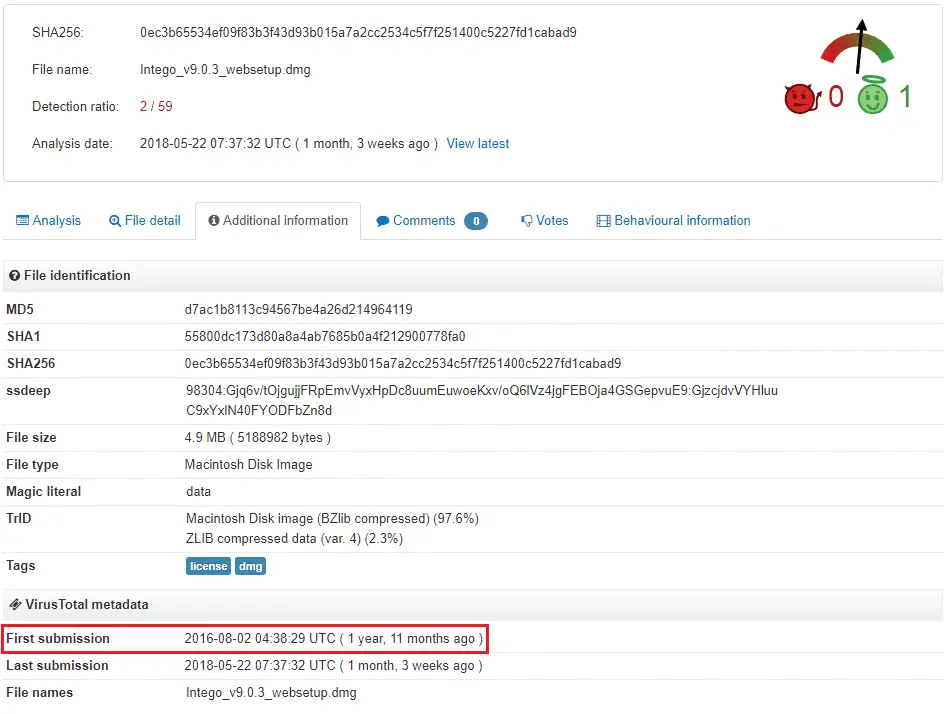
“We recently came across one such sample: a macOS backdoor that we named Calisto.The malware was uploaded to VirusTotal way back in 2016, most likely the same year it was created. But for two whole years, until May 2018, Calisto remained off the radar of antivirus solutions, with the first detections on VT appearing only recently.”
“Conceptually, the Calisto backdoor resembles a member of the Backdoor.OSX.Proton family.”
According to Kaspersky, Calisto’s installation file is an unsigned DMG image, but it is camouflaged with the Intego security solution (Mac version). At the same time, Kaspersky also noted that although the same roots as Proton, some features of Proton did not appear in Calisto.
Proton’s real face was only revealed in March last year, and the hacker created the virus in the underground hacking forum. The price of the whole project ranged from $1200-830.000.
A few weeks later, Proton was involved in the hacking for the first time, and the criminals blacked out the HandBrake app’s website and implanted the virus into the app. In October 2017, Proton RAT embedded into legitimate applications such as Elmedia Player and download manager Folx. Both Proton RAT and Calisto are remote access Trojan horses (RATs), and once infected, hackers gain control of the system.
If the Mac infected with Calisto, the hacker could quickly implement the following features remotely:
- Enables remote login
- Enables screen sharing
- Configures remote login permissions for the user
- Allows remote login to all
- Enables a hidden “root” account in macOS and sets the password specified in the Trojan code
After static analysis by experts, several other unfinished functions have been discovered, such as:
- Loading/unloading of kernel extensions for handling USB devices
- Data theft from user directories
- Self-destruction together with the OS
Security experts pointed out that Calisto developed before Apple introduced the SIP (System Integrity Protection) security mechanism, so it could not bypass SIP.
“Calisto’s activity on a computer with SIP (System Integrity Protection) enabled is rather limited. Announced by Apple back in 2015 alongside the release of OSX El Capitan, SIP is designed to protect critical system files from being modified — even by a user with root permissions. Calisto was developed in 2016 or earlier, and it seems that its creators simply didn’t take into account the then-new technology.”
Kaspersky issues the suggestion to protect against Calisto, Proton
- Always update to the current version of the OS
- Never disable SIP
- Run only signed software downloaded from trusted sources, such as the App Store
- Use antivirus software
Source, Image: securelist