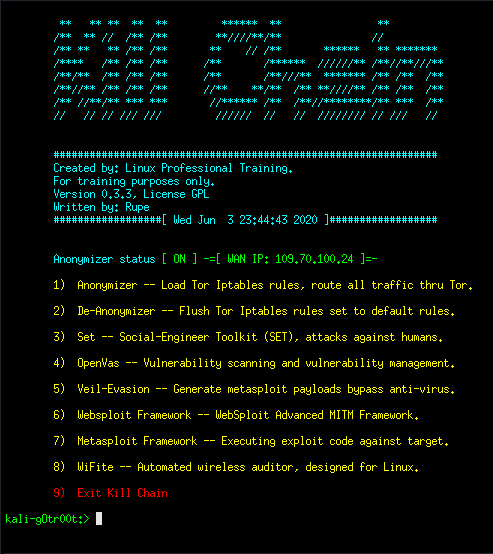
killchain
“Kill Chain” is a unified console with an anonymizer that will perform these stages of attacks:
• Reconnaissance – Uses social engineering to find weaknesses in the target’s security posture.
• Weaponization – Crafting attack tools for the target system.
• Delivery – Delivering the attack tools to the target system.
• Exploit – The malicious file intended for an application target system or the operating system vulnerabilities control objectives is opened by the victim on the target system.
• Installation – Remote control program installed on the target system.
• Command & Control – Successfully compromised hosts will create a C2 channel on the Internet to establish a connection with the C2 server.
• Actions – After the preceding process, the attacker will continue to steal information about the target system, undermine the integrity and availability of information, and further to control the machine to jump to attack other machines, to expand the sphere of influence.
Dependent toolsets are:
- Tor — For the console build-in anonymizer.
- Set — Social-Engineer Toolkit (SET), attacks against humans.
- OpenVas — vulnerability scanning and vulnerability management.
- Veil-Evasion — Generate Metasploit payloads bypass anti-virus.
- Websploit — WebSploit Advanced MITM Framework.
- Metasploit — Executing exploit code against a target.
- WiFite — Automated wireless auditor, designed for Linux.