
Rapid7, a leading cybersecurity firm, has released a comprehensive report detailing the evolving tactics, techniques, and procedures (TTPs) of the Kimsuky advanced persistent threat (APT) group. Kimsuky, a North Korean state-sponsored actor, has been actively targeting government, research, and think tank organizations worldwide.
Kimsuky operates under the direction of North Korea’s Reconnaissance General Bureau (RGB). Despite only moderate technical prowess, Kimsuky is highly adept at social engineering, frequently developing intricate personas and cover identities to facilitate phishing attacks. Their primary objectives are credential theft and mailbox access, often utilizing a range of unsophisticated malware to support these goals.
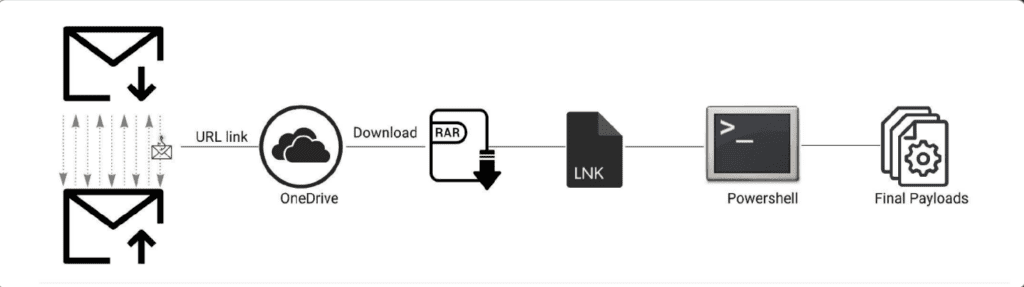
Rapid7’s research identifies email as Kimsuky’s primary delivery method, with the group known for its advanced social engineering tactics. A hallmark of Kimsuky’s strategy involves constructing detailed backstories during phishing activities. By engaging in multiple email exchanges and mimicking routine correspondence, they build trust before attempting to phish the target. This method has recently been extended to platforms like Facebook, demonstrating the effectiveness of their trust-building approach.
Kimsuky exploits permissive DMARC policies to spoof emails, bypassing security checks by modifying email headers to appear as legitimate organizations. This technique has been particularly successful due to many targeted organizations either not enabling or enforcing DMARC policies.
Kimsuky’s payloads are typically delivered through LNK or CHM files. Rapid7 observed several LNK file variants, often downloading subsequent stages via public applications like Dropbox API. The LNK files are meticulously crafted, with unique characteristics such as multiline descriptions and leading spaces in arguments to bypass analysis tools.
Additionally, Kimsuky has been noted for using Compiled HTML Help (CHM) files, exploiting their capability to contain and execute HTML and JavaScript code. Another emerging tactic involves the use of .msc files associated with Microsoft Management Console, masquerading as documents to socially engineer users into executing them.
Kimsuky has focused on government, research, and think tanks related to nuclear policy or geopolitics connected to North Korean interests. Their targets span South Korea, the United States, Japan, and various European countries. The group’s lures often revolve around themes such as payments, crypto regulations, and trusted installers with signed binaries.
Rapid7’s tracking of Kimsuky infrastructure reveals the group’s prolific activity, leveraging numerous hosting providers and ASNs worldwide. They frequently reuse IP addresses and employ similar domain names as their targets, using free certificate services to enhance their phishing sites’ legitimacy.
Kimsuky relies on valid credentials for mailbox access but also uses common persistence techniques during malware installation. These include run keys, services, scheduled tasks, and system binary proxy execution, often with obfuscated PowerShell scripts.
Despite their moderate technical capabilities, Kimsuky’s expertise in social engineering and persistent tactics make them a formidable adversary. For more detailed information and to access the full report, visit Rapid7’s website.
Related Posts:
- North Korean APT Group Kimsuky Targets Japanese Organizations with Stealthy Malware Campaign
- QiAnXin Uncovers New Kimsuky Malware Campaign
- Kimsuky – North Korea’s Cyber Threat
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger
- AppleSeed Malware: The Evolving Threat of the Kimsuky Group