
The notorious North Korean APT group Kimsuky has continued its cyber espionage operations, leveraging spear-phishing attacks and remote access tools to infiltrate targeted systems, according to a new report by the AhnLab Security Intelligence Center (ASEC). This latest analysis highlights the group’s increased reliance on a custom-built RDP Wrapper to maintain persistent access, alongside the use of keyloggers, proxy tools, and information-stealing malware.
Kimsuky’s attack strategy begins with a well-crafted spear-phishing campaign distributing malicious shortcut files (.LNK) disguised as legitimate documents. The attackers have carefully selected filenames containing company names and personal details, indicating a high level of reconnaissance.
“The shortcut malware is disguised as a document file with an Office document icon such as PDF, Excel, or Word,” states ASEC. Once executed, these LNK files launch PowerShell or Mshta scripts, which then download and install additional malware components, including PebbleDash and the custom RDP Wrapper.
RDP Wrapper is an open-source utility designed to enable Remote Desktop Protocol (RDP) functionality on Windows editions that do not support RDP by default. However, Kimsuky has developed its own custom version of RDP Wrapper to facilitate stealthy remote access.
“The threat actor is using RDP Wrapper that they created themselves. It is suspected that they are creating Export functions in various ways to bypass file detection,” ASEC reports. By modifying export functions, Kimsuky avoids detection by security tools, ensuring that their backdoor remains operational.
Additionally, Kimsuky deploys proxy malware to bypass network restrictions that would normally block external access to compromised machines. These proxies act as an intermediary, allowing the attackers to connect to infected systems even if they are located within a private network.
Beyond remote access, Kimsuky utilizes a range of tools to exfiltrate sensitive information, including:
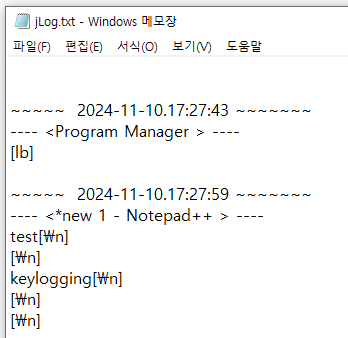
- Keyloggers: Capturing user keystrokes and saving them in files such as joeLog.txt and jLog.txt.
- Web Credential Theft (forceCopy): Extracting encrypted browser credentials by copying key configuration files rather than directly stealing stored passwords.
- Injectors and Loaders: Deploying malicious payloads into system memory using open-source tools like Invoke-ReflectivePEInjection.ps1.
The group’s evolving approach suggests a shift away from traditional backdoors toward a stealthier and more resilient method of system control.
Related Posts:
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
- North Korean APT Group Kimsuky Targets Japanese Organizations with Stealthy Malware Campaign
- QiAnXin Uncovers New Kimsuky Malware Campaign
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger