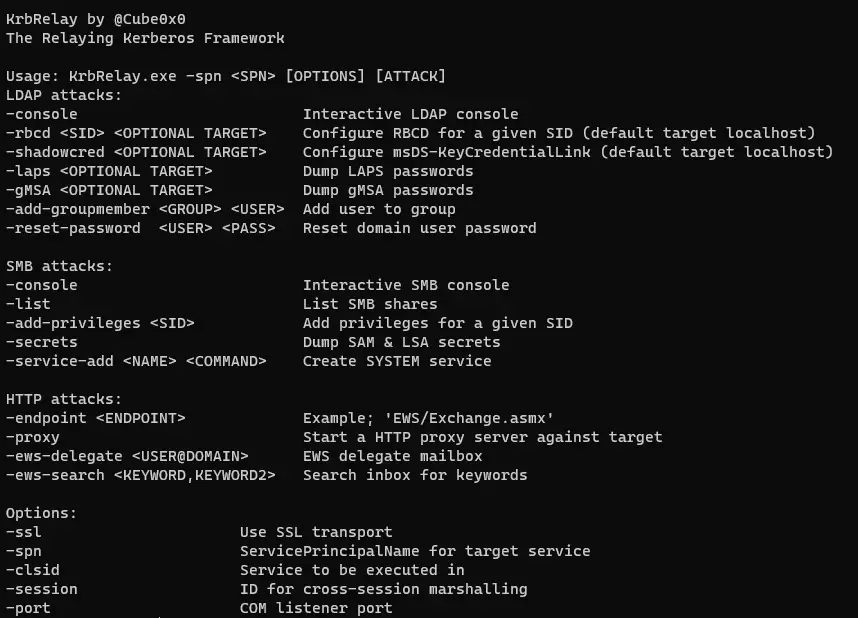
KrbRelay
the only public tool for relaying Kerberos tickets and the only relaying framework written in C#.
More details at https://googleprojectzero.blogspot.com/2021/10/windows-exploitation-tricks-relaying.html and https://googleprojectzero.blogspot.com/2021/10/using-kerberos-for-authentication-relay.html
This should be working on most fully patched Windows systems. There may be difficulties with Server OS in lab environments because of the firewall blocking the OXID resolver however, this will most likely not be an issue during real-life engagements, same goes for CLSIDs.

Supported Protocols and Features
Some protocols are more completed than others, PR’s are welcomed.
- LDAP/LDAPS
- HTTP
- EWS
- SMBv2
- RPC over SMB
- MS-SAMR
- MS-SCMR
- MS-RPRN
- MS-RRP
- MS-LSAT/MS-LSAD
CLSIDs
We’ll need to unmarshal our OBJREF inside of a process that would allow authentications over the network, this can be verified by looking at the Impersonation Level
- RPC_C_IMP_LEVEL_DEFAULT # Will not work
- RPC_C_IMP_LEVEL_ANONYMOUS # Will not work
- RPC_C_IMP_LEVEL_IDENTIFY # Works for LDAP
- RPC_C_IMP_LEVEL_IMPERSONATE # Required for SMB
- RPC_C_IMP_LEVEL_DELEGATE
When relaying to LDAP or any other service that has signing enabled but not enforced we would also need to verify that the Authentication Level of the process is set to RPC_C_AUTHN_LEVEL_CONNECT.
Processes running under NT Authority\Network service will use the SYSTEM account when authenticating over the network.