KubiScan
A tool for scanning the Kubernetes cluster for risky permissions in Kubernetes’s Role-based access control (RBAC) authorization model. The tool was published as part of the “Securing Kubernetes Clusters by Eliminating Risky Permissions” research.
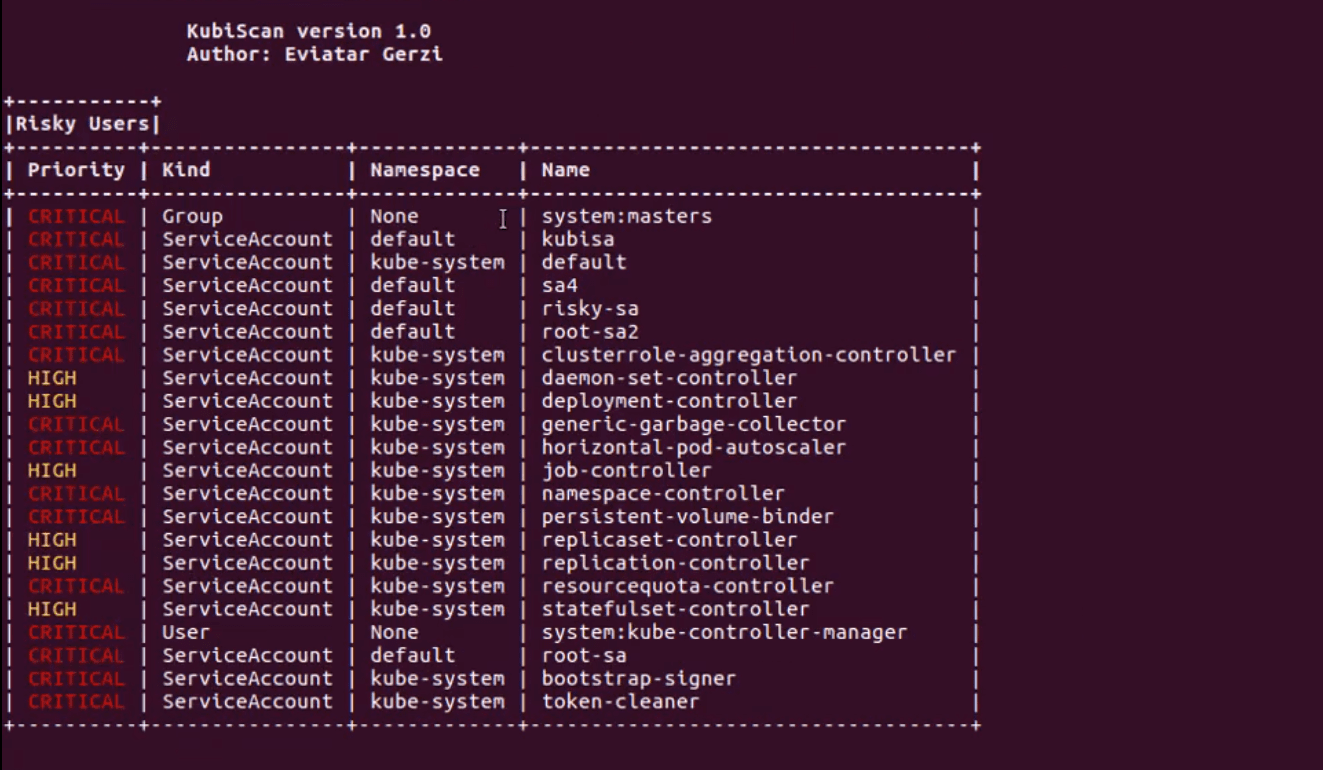
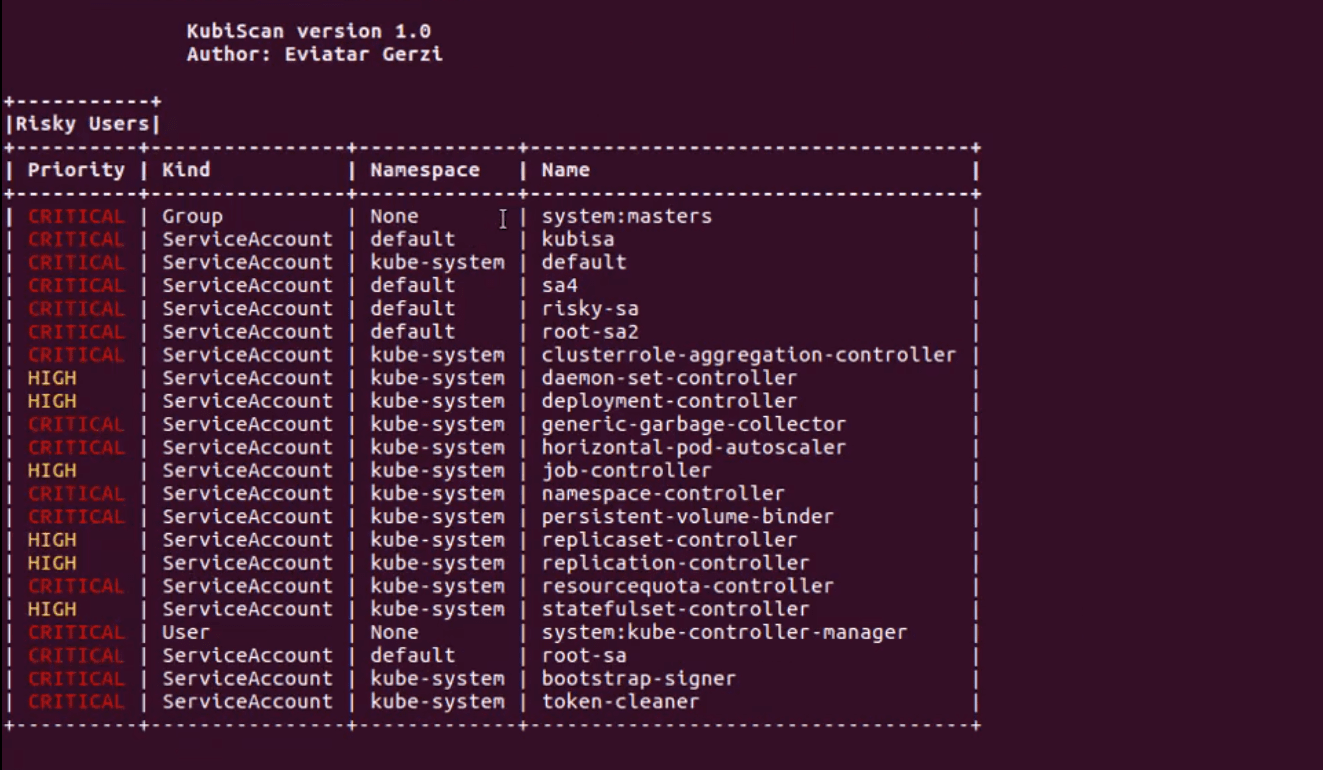
KubiScan helps cluster administrators identify permissions that attackers could potentially exploit to compromise the clusters. This can be especially helpful in large environments where there are lots of permissions that can be challenging to track. KubiScan gathers information about risky roles\clusterroles, rolebindings\clusterrolebindings, users, and pods, automating traditionally manual processes and giving administrators the visibility they need to reduce risk.
What can it do?
- Identify risky Roles\ClusterRoles
- Identify risky RoleBindings\ClusterRoleBindings
- Identify risky Subjects (Users, Groups, and ServiceAccounts)
- Identify risky Pods\Containers
- Dump tokens from pods (all or by namespace)
- Get associated RoleBindings\ClusterRoleBindings to Role, ClusterRole or Subject (user, group or service account)
- List Subjects with specific kind (‘User’, ‘Group’ or ‘ServiceAccount’)
- List rules of RoleBinding or ClusterRoleBinding
- Show Pods that have access to secret data through a volume or environment variables
- Get bootstrap tokens for the cluster
Changelog v1.6
- Replaced Added support to match case match case with if else to support Python versions below 3.10 (#69 by @kamal2222ahmed)
- Failed chmod when not specifying AWS info (#66 & #67 by @elreydetoda)
- Adding support to AKS and options to CVE scan (#65 by @2niknatan)
- Adding CVE scan and unittest (#64 by @2niknatan)
- Adding flags (
-o,-q,-jand-nc) to enhance the output (#63 by @2niknatan) - Changing the risky pods function (#62 by @2niknatan)
- Adding unit tests (#55 by @2niknatan)
- Supporting eks in docker container (#54 by @2niknatan)
- Printing error message when no kind was entered to ‘-aars’ flag (#53 by @2niknatan)
- Fixing duplicates in ‘-rp’ flag (#52 & #50)
- Fix typo in api_client.py (#51 by @AlonBenHorin)
- Fixing ‘-rp’ flag by adding logic so it can print several Service Accounts (#49 by @2niknatan)
- Adding secret creation to support version +1.24
- Fixing hang in some environments (#47 by @2niknatan)
- Fixing the path to ‘/opt/kubiscan/config_bak’ like in the Dockerfile (#46 by @2niknatan)
- Adding an environment variable to docker file, fixing -td flag and catching exceptions and adding tag to docker image (#45 by @2niknatan)
- Update docker_run.sh
- Adding catch exception and fix non existing key bug (#41 by @AlonBenHorin)
- Fixing pull request #18 and adding bash script to run a container (#40 by @AlonBenHorin)
- Minor change in the check for running inside a container
- Added support to kubeconfig in the API client (by @g3rzi)
- Simplify dockerfile + Parameterize paths (#18 by @vidbina)
Install && Use
Copyright (C) 2018