LARRYCHATTER
Introduction:
Introducing a super-stealthy extra sneaky Python-based C2 Framework that uses Twitter & Dropbox as a C2 Server. This project has been inspired by the Russian threat-group APT-29’s own malware HAMMERTOSS tDiscoverer variant. In fact, LARRYCHATTER is HAMMERTOSS Revenant. A Reincarnation. In pure Python. It’s a lot of similiar except that it’s better.
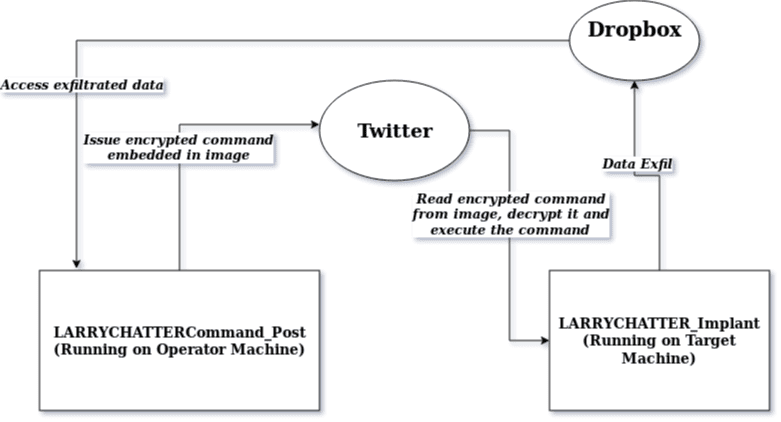
A Simplified Block Diagram First:
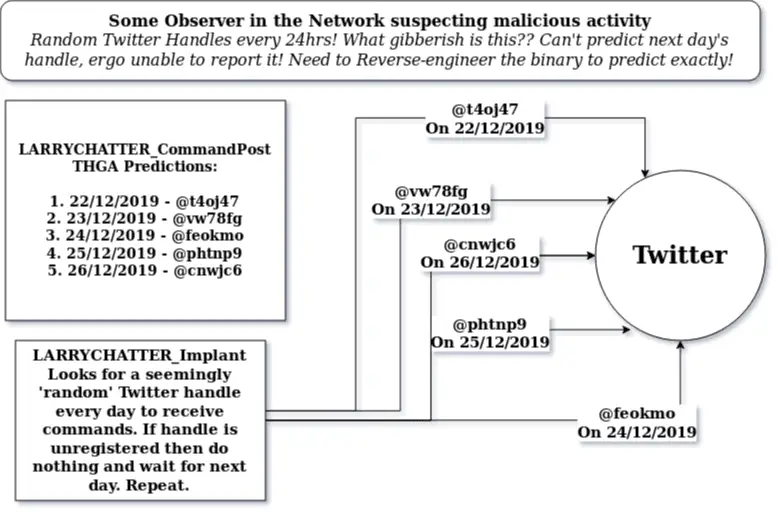
Another One Of Twitter Handle Generation Algorithm:
So What Is LARRYCHATTER Exactly?
LARRYCHATTER is a cross-platform C2 Framework. Much like Merlin, Sliver, Faction C2, yada yada yada. The only difference is that it uses covert channels over social media for command and control instead of standard communication over HTTP/HTTPS to attacker-controlled domains which can be detected very easily and also taken down in a jiffy. Its purpose is to make the life of Blue-teamers a lot-less easy! It is primarily aimed at professional red-teamers for red-team engagements. Modules can be written in Python and integrated at the click of a finger. The prototype version of LARRYCHATTER comes with two modules – a ‘recon’ module and a ‘kill’ module in-built which is albeit very crude and doesn’t do much. My main goal was to show everyone how easily social-media and public platforms can be exploited by malware to communicate with its operators. Additional modules and advancement of existing ones coming soon, so stay tuned mates 😉
Terminology:
LARRYCHATTER Framework consists of:
- CommandPost – The software which is used to issue commands to the Implant run by the operator.
- Implant – The main malware which is run on the target machine.
This repository contains three source files:
- LARRYCHATTER_CommandPost.py which is the source code of the LARRYCHATTER Command Post(CP)?
- LARRYCHATTERImplant.py which is the source code of the LARRYCHATTER Implant?
- decrypter.py to decrypt the Intel collected by the Implant from the target machine and uploaded to Dropbox.
Features:
- No suspicious internet traffic to external unknown domains for C&C – Only traffic observed is Twitter and Dropbox! (Say buh-bye to those pesky firewalls/IDSs). Basically designed to mimic human behavior so as to bypass network security products.
- ‘kill’ module – Terminates the Implant on the target machine.
- ‘recon’ module – Performs initial recon on the target system like basic system details, patches installed, takes screenshots on a random interval for ‘x’ minutes and searches for all types of juicy file-types for exfiltration later and encrypts all the collected Intel and zips it into a single file. Windows-support only. Very crude. No AV-Evasion subroutines. But fully functional and uploads collected Intel on a Dropbox account for retrieval by the operator later.
- Basic Steganography integrated.
- Hardcoded symmetric encryption support in-built with 128-bit AES in CBC Mode.
- Coded in Python 3.
- Single Implant support only by CommandPost since this is only the prototype.
Install && Use
Copyright (c) 2019 Upayan Saha