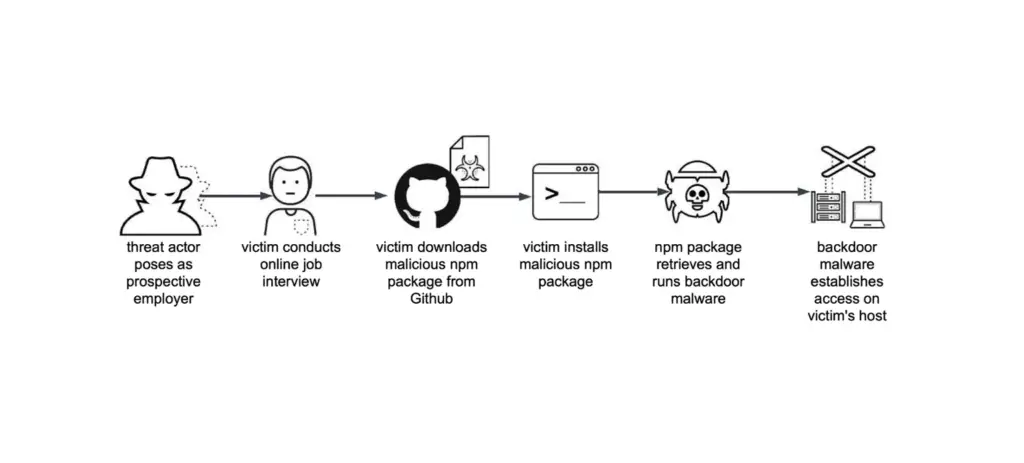
Contagious Interview campaign (Source: Unit42)
North Korea’s infamous Lazarus Group is back in the spotlight, this time deploying a sophisticated infostealer malware campaign aimed at software developers and IT professionals. According to a recent report by Threat Intelligence Researcher Rayssa Cardoso, the attackers are leveraging malicious Python scripts, fake job interviews, and social engineering tricks to steal sensitive data and gain persistent access to compromised systems.
The infostealer malware, linked to Lazarus Group, employs a series of sophisticated evasion techniques. Cardoso’s research uncovered malicious Python code that executes through multiple layers of encoding before revealing its actual payload. The script:
- Decodes itself using Base64.
- Decompresses its contents with ZLIB.
- Executes the final malicious payload using Python’s exec() function.
“The code was designed to execute multiple repetition processes, where each obfuscation stage pointed to the previous one until the loop was completed, ultimately decrypting and revealing the actual malware code,” the report states.
Once fully deobfuscated, the malware is capable of:
- Fingerprinting victims’ systems, collecting OS type, device names, active user profiles, and geolocation data.
- Intercepting clipboard and keystroke data.
- Deploying a backdoor, enabling remote control over infected machines
Lazarus is taking social engineering to the next level by impersonating recruiters and targeting developers on platforms like LinkedIn, GitHub, and Discord. This tactic, labeled “Contagious Interview”, involves fake job offers where victims are tricked into executing malicious code under the guise of meeting hiring requirements.
“Fake recruiter profiles approach developers, inviting them to participate in an online interview,” Cardoso writes. “They are given a well-crafted questionnaire, and at the final stage, they are asked to run a script or install an NPM package, which contains an infostealer malware and a backdoor.”
Another key technique used in Lazarus’ recent campaign is “ClickFix”, a deceptive social engineering attack where victims are instructed to click a button to “fix” a fake error message. This attack has been seen in multiple variants:
- A HTML document disguised as a Microsoft Word file.
- A deceptive PowerShell command that clears system logs before executing the malware.
- A malicious NPM package that installs an infostealer and SSH backdoor.
“The attack begins with users being lured into visiting seemingly legitimate but compromised websites,” the report explains. “ClickFix is a highly sophisticated social engineering attack, leveraging an authentic appearance to manipulate users into executing malicious scripts.”
The infostealer malware found in this campaign ultimately deploys Tsunami, a multi-platform RAT (Remote Access Trojan) that enables full control over the infected system. The malware structure includes:
- sysinfo folder – Gathers system information and C2 connectivity.
- n2 folder – Stores stolen data, checks Python registry keys, and installs necessary dependencies.
- pay file – Executes system fingerprinting, keylogging, and clipboard data collection.
- Backdoor functionality – Establishes an SSH connection for remote command execution.
“A connection will open to try to connect to the remote server and send data. After completing this step, the logs related to the connection are destroyed so as not to leave any traces on the network,” the researcher explains.
“It is noticeable that all the campaigns mentioned here follow the same attack pattern using social engineering,” Cardoso warns.
Related Posts:
- Temptation from Money: Lazarus APT extended to cryptocurrencies
- LummaC2 Infostealer Malware Spreads via Crack Programs and Phishing
- New Skuld Infostealer Campaign Unveiled in npm Ecosystem
- Infostealers Overcome Chrome’s App-Bound Encryption, Threatening User Data Security
- Lazarus Group Deploys Electron-Based Malware to Target Cryptocurrency Enthusiasts