LDAP_Search
LDAP_Search can be used to enumerate Users, Groups, Computers, Domain Policies, and Domain Trusts within a Windows environment. Authentication can be performed using traditional username and password, or NTLM hash. In addition, this tool has been modified to allow brute force/password-spraying via LDAP.
Ldap_Search is compatible with Python 2.7 / 3.6+ and makes use of the Impacket library to perform the main operations.

Installation
git clone --recursive https://github.com/m8r0wn/ldap_search cd ldap_search sudo chmod +x setup.sh sudo ./setup.sh
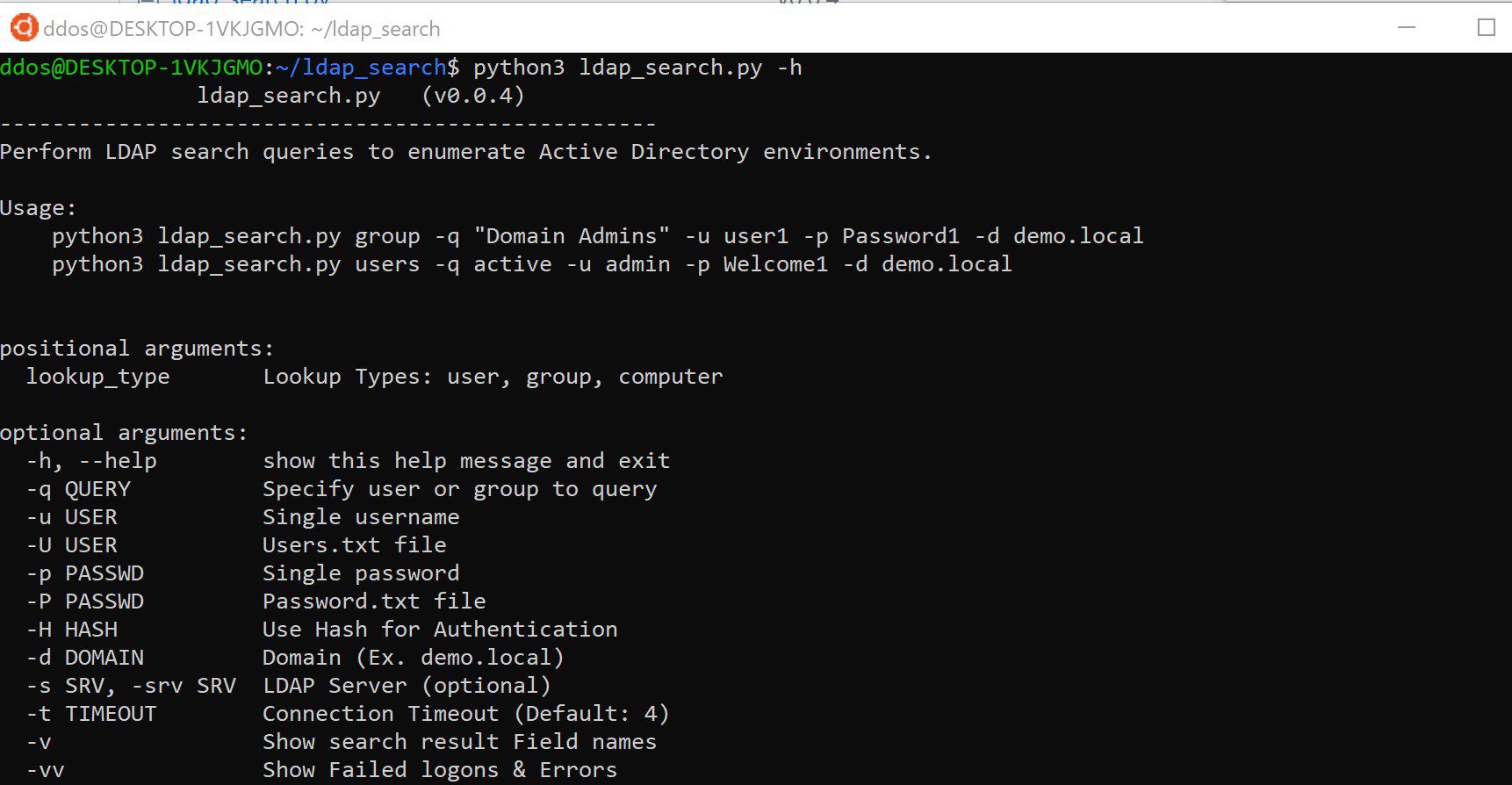
Usage
Enumerate all active users on a domain:
python3 ldap_search.py users -u user1 -p Password1 -d demo.local
Lookup a single user and display field headings:
python3 ldap_search.py users -q AdminUser -u user1 -p Password1 -d demo.local
Enumerate all computers on a domain:
python3 ldap_search.py computers -u user1 -p Password1 -d demo.local
Search for an end of life systems on the domain:
python3 ldap_search.py computers -q eol -u user1 -p Password1 -d demo.local -s DC01.demo.local
Enumerate all groups on the domain:
python3 ldap_search.py groups -u user1 -p Password1 -d demo.local -s 192.168.1.1
Query group members:
python3 ldap_search.py groups -q "Domain Admins" -u user1 -p Password1 -d demo.local
Queries
Below are the query options that can be specified using the “-q” argument:
Copyright (C) 2018 m8r0wn
Source: https://github.com/m8r0wn/