LDAPWordlistHarvester
A tool to generate a wordlist from the information present in LDAP, in order to crack non-random passwords of domain accounts.
Features
The bigger the domain is, the better the wordlist will be.
- Creates a wordlist based on the following information found in the LDAP:
- User: name and sAMAccountName
- Computer: name and sAMAccountName
- Groups: name
- Organizational Units: name
- Active Directory Sites: name and descriptions
- All LDAP objects: descriptions
- Choose a wordlist output file name with an option –outputfile
Install
git clone https://github.com/p0dalirius/LDAPWordlistHarvester.git
cd LDAPWordlistHarvester
pip install -r requirements.txt
Use
Demonstration
To generate a wordlist from the LDAP of the domain domain.local you can use this command:
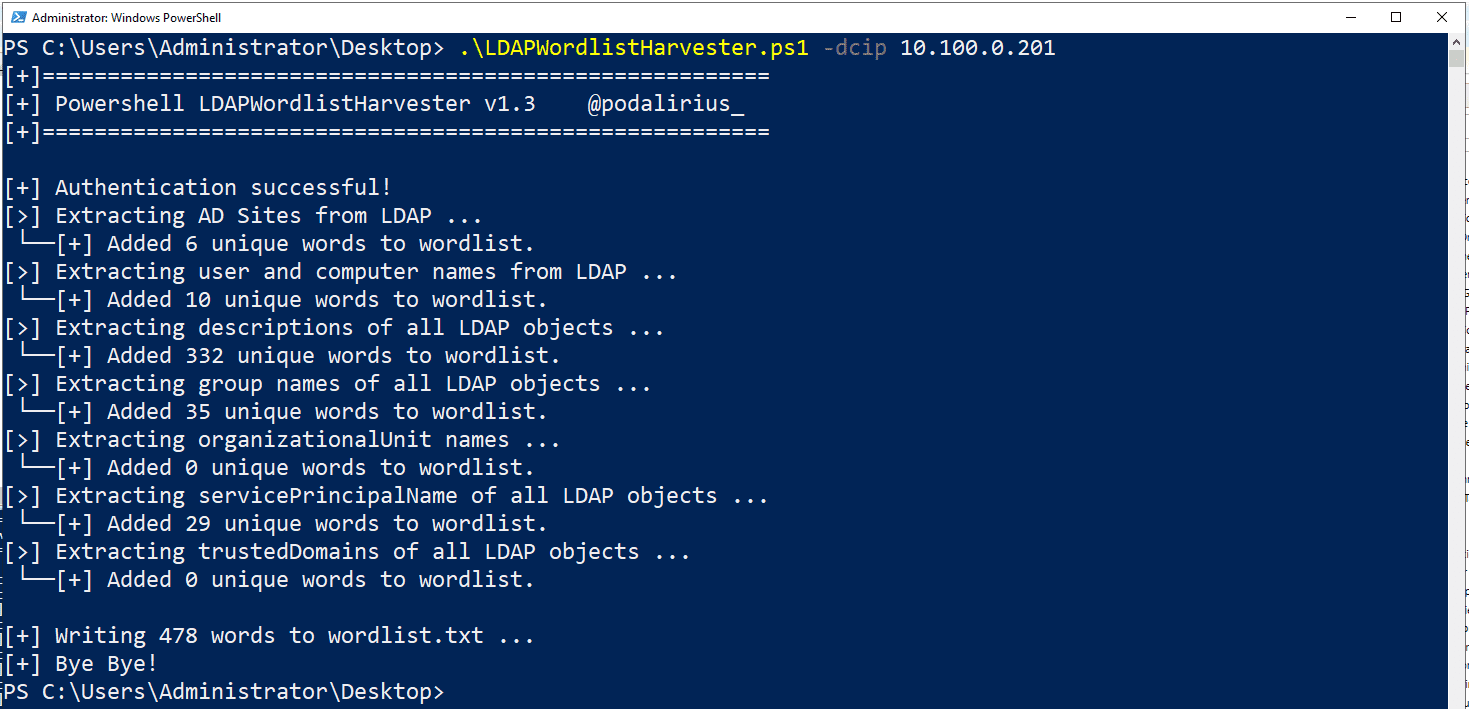
./LDAPWordlistHarvester.py -d ‘domain.local’ -u ‘Administrator’ -p ‘P@ssw0rd123!’ –dc-ip 192.168.1.101
You will get the following output if using the Python version:
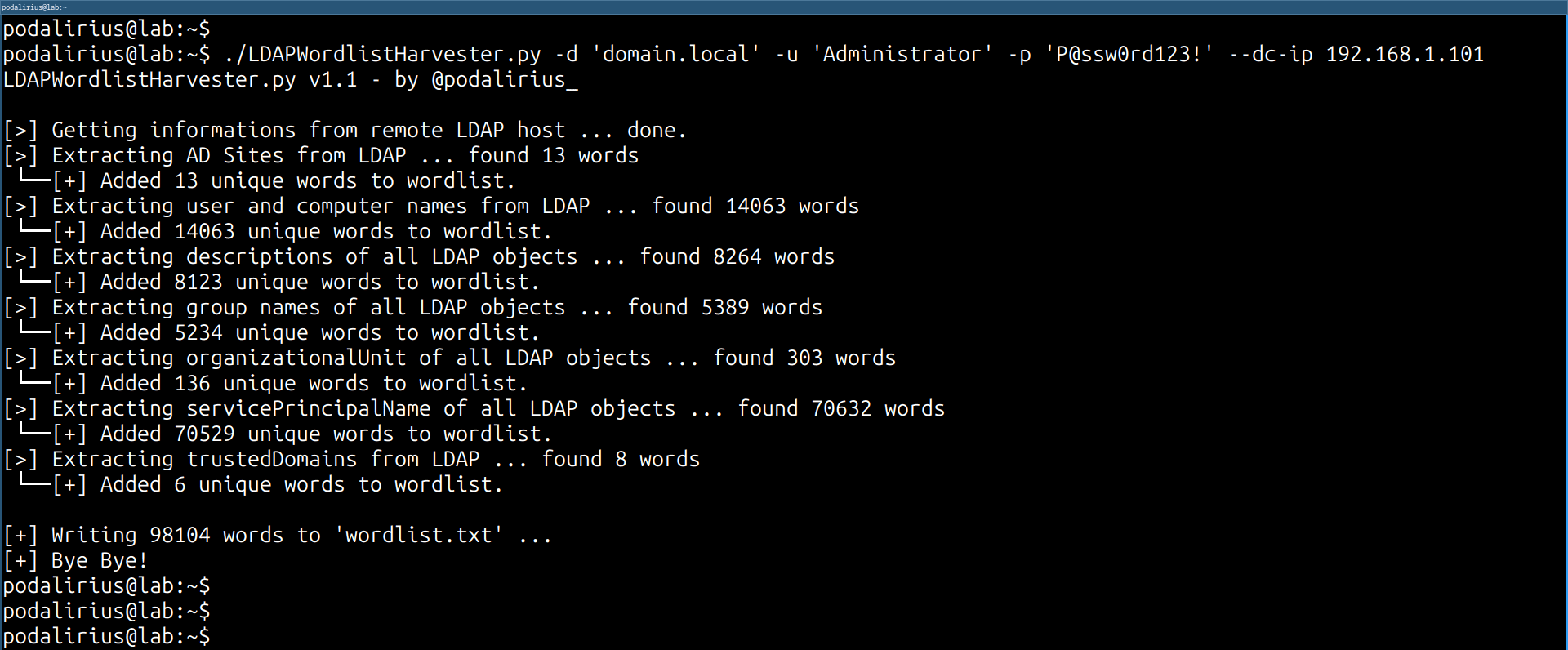
You will get the following output if using the Powershell version:

Cracking passwords
Once you have this wordlist, you should crack your NTDS using hashcat, –loopback, and the rule clem9669_large.rule.
./hashcat –hash-type 1000 –potfile-path ./client.potfile ./client.ntds ./wordlist.txt –rules ./clem9669_large.rule –loopback
Source: https://github.com/p0dalirius/