Source: Artem Baranov
Security researcher Artem Baranov has detailed a sophisticated malware campaign targeting the Ukrainian military through a backdoor leveraging SSH over TOR. The campaign exploits the digital infrastructure of “Army+,” a platform developed for Ukrainian military personnel.
The attackers created fake websites mimicking the official “Army+” platform, distributing a malicious installer named ArmyPlusInstaller-v.0.10.23722.exe. At first glance, the executable appeared legitimate, including files like a main application, uninstaller, and license text. However, as Baranov observed: “One unusual detail stands out: the presence of another archive containing the Tor browser.”
The installer also ran a decoy application, ArmyPlus.exe, which displayed an error message suggesting incompatibility with the victim’s system, further masking malicious activity.
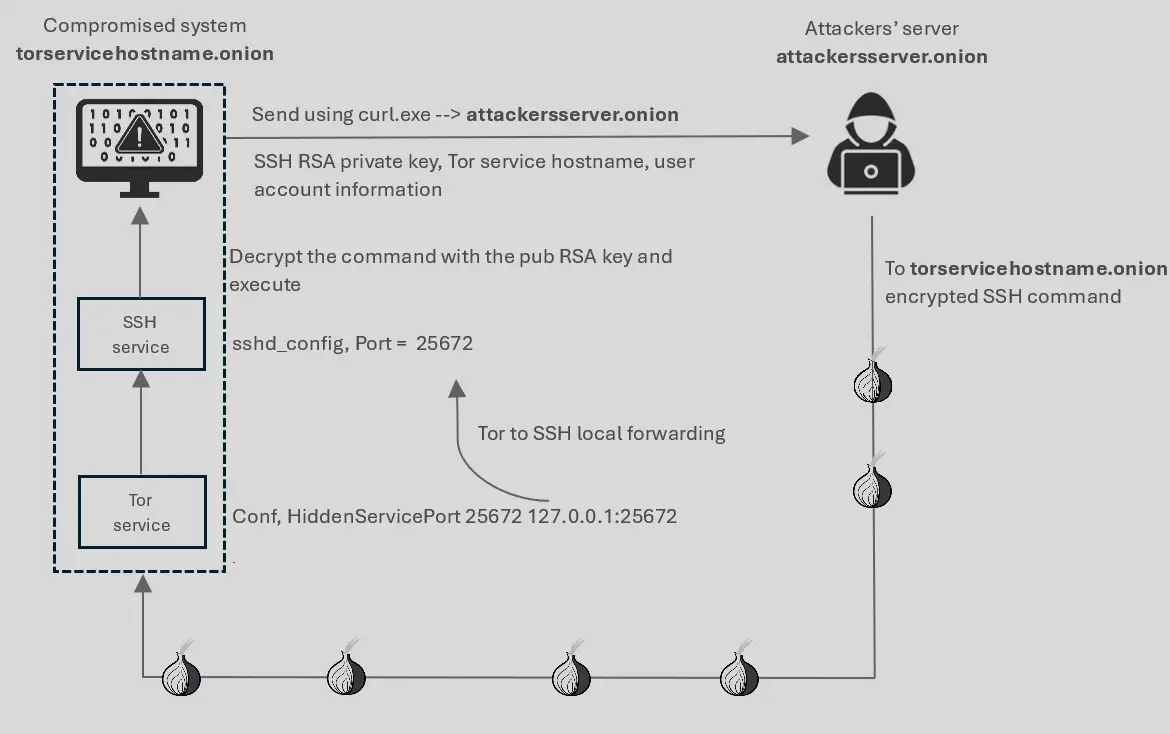
The attack leveraged the PowerShell script init.ps1, which executed malicious commands under the radar. By disabling PowerShell’s execution policy, the malware bypassed security checks, extracted files to concealed directories, and initiated TOR-based communication. Baranov noted: “The malware drops its files into three different folders with inconspicuous names.”
Among the dropped files were TOR and OpenSSH components, used to establish an anonymous and secure backdoor communication channel.
How the Backdoor Operates
- TOR Integration: The script deployed TOR to create an onion service, storing the address in the hostname file for secure communication.
- SSH Key Generation: Using the built-in ssh-keygen tool, it created RSA key pairs for encrypted command execution.
- OpenSSH Setup: The backdoor installed and configured OpenSSH as a Windows service, granting attackers high-privilege access to the compromised system.
The malware then sent system information, RSA keys, and the onion address to the attacker’s server via TOR, establishing a functional backdoor ready to execute remote commands.
One of the most striking aspects of the campaign was its reliance on legitimate software. All executables involved, such as curl.exe and ssh-keygen, were signed and native to Windows systems. “The attackers opted not to use malicious Windows executables that can be easily detected by anti-malware software,” Baranov explained. This strategy allowed the malware to evade traditional antivirus detection effectively.
Baranov emphasized the importance of robust endpoint protection and regular monitoring of system behaviors to detect anomalies. He also suggested using YARA rules like armyplus_script to identify malicious scripts based on the identified patterns.
Related Posts:
- Three Ukrainian hackers arrested for stealing 15 million credit card records in the US
- Tor Network Thwarts IP Spoofing Attack
- Google’s TAG Disrupts Russian Cyber Campaigns Targeting Ukraine
- S. aid to Ukraine’s cybersecurity to $10 million