exitmap v2020.11.23 releases: A fast and modular scanner for Tor exit relays
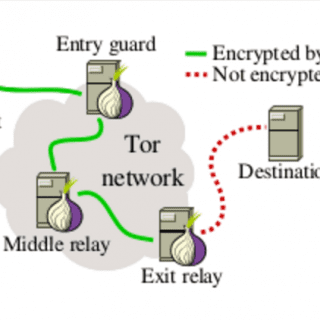
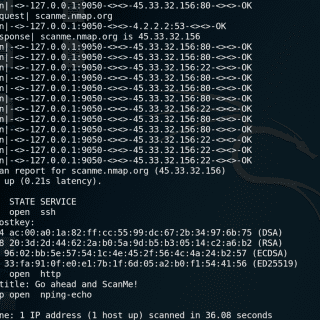
Overview Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you have a background in functional...