MC Extractor is a tool which parses Intel, AMD, VIA, and Freescale processor microcode binaries. It can be used by end-users who are looking for all relevant microcode information such as CPUID, Platform, Version, Date, Release, Size, Checksum, etc. It is capable of converting Intel microcode containers (dat, inc, h, txt) to binary images for BIOS integration, detecting new/unknown microcodes, checking microcode health, Updated/Outdated status, and more. MC Extractor can be also used as a research analysis tool with multiple structures which allow, among others, full parsing & information display of all documented or not microcode Headers. Moreover, with the help of its extensive database, MC Extractor is capable of uniquely categorizing all supported microcodes as well as check for any microcodes which have not been stored at the Microcode Repositories yet.

A1. MC Extractor Features
- Supports all current & legacy Microcodes from 1995 and onward
- Scans for all Intel, AMD, VIA & Freescale microcodes in one run
- Verifies all extracted microcode integrity via Checksums
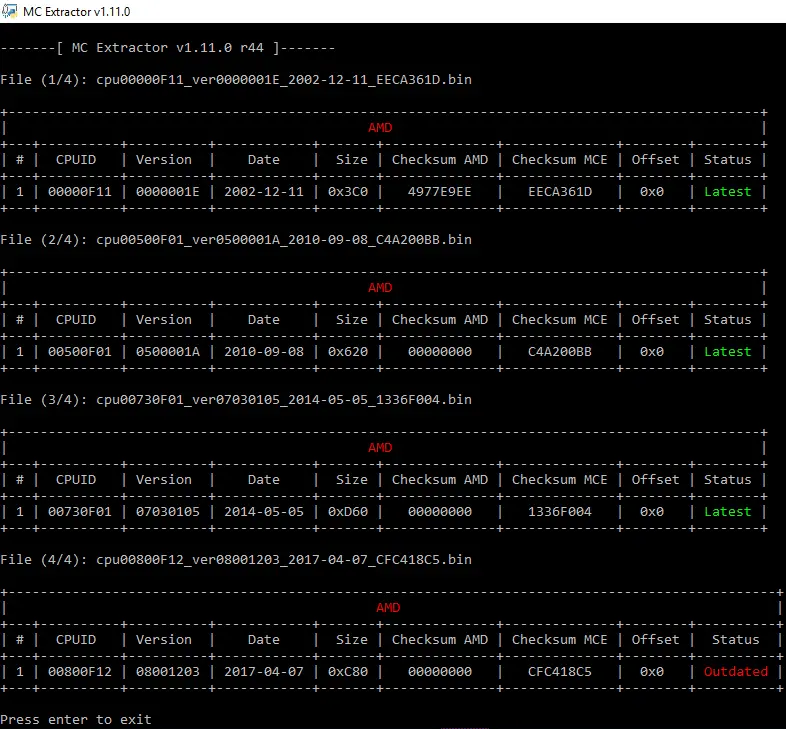
- Checks if all Intel, AMD & VIA microcodes are Latest or Outdated
- Converts Intel containers (dat,inc,txt,h) to binary images
- Searches on demand for all microcodes based on CPUID
- Shows microcode Header structures and details on demand
- Ignores most false positives based on sanity checks
- Supports known special, fixed or modded microcodes
- Ability to quickly add new microcode entries to the database
- Ability to detect Intel Production/Pre-Production Release tag
- Ability to analyze multiple files by drag & drop or by input path
- Ability to ignore extracted duplicates based on name and contents
- Reports all microcodes which are not found at the Microcode Repositories
- Features command line parameters to enhance functionality & assist research
- Features user-friendly messages & proper handling of unexpected code errors
- Shows results in nice tables with colored text to signify emphasis
- Open Source project licensed under GNU GPL v3, comment assisted code
A2. Microcode Repository Database
MC Extractor allows end-users and/or researchers to quickly extract, view, convert & report new microcode versions without the use of special tools or Hex Editors. To do that effectively, a database had to be built. The Intel, AMD & VIA CPU Microcode Repositories is a collection of every Intel, AMD & VIA CPU Microcodes we have found. Its existence is very important for MC Extractor as it allows us to continue doing research, find new types of microcode, compare releases for similarities, check for updated binaries etc. Bundled with MC Extractor is a file called MCE.db which is required for the program to run. It includes entries for all Microcode binaries that are available to us. This accommodates primarily two actions: a) Check whether the imported microcode is up to date and b) Help find new Microcode releases sooner by reporting them at the Intel, AMD & VIA CPU Microcode Repositories Discussion thread.
A3. Sources and Inspiration
MC Extractor was initially based on a fraction of Lordkag’s UEFIStrip tool so, first and foremost, I thank him for all his work which inspired this project. Among others, great places to learn about microcodes are Intel’s own download site and official documentation, Intel Microcode Patch Authentication, Coreboot (a,b,c), Microparse by Dominic Chen, Ben Hawkes’s Notes and Research, Richard A Burton’s Microdecode, AIDA64 CPUID dumps, Sandpile CPUID, Free Electrons (a, b), Freescale and many more which I may have forgotten but would have been here otherwise.
Changelog
v1.98.0
Improved handling of a known modded Intel microcode
r292
Intel cpu806F8_plat10_ver2C000360_2024-01-03_PRD_B1AC7CE2
Intel cpu806F6_plat10_ver2C000360_2024-01-03_PRD_B1AC7CE4
Intel cpu806F5_plat10_ver2C000360_2024-01-03_PRD_B1AC7CE5
Intel cpu806F4_plat10_ver2C000360_2024-01-03_PRD_B1AC7CE6
Intel cpuB06E0_plat11_ver00000017_2023-12-07_PRD_40C9284F
Intel cpu906A4_plat80_ver00000433_2023-12-05_PRD_37DB5D1E
Intel cpu906A3_plat80_ver00000433_2023-12-05_PRD_37DB5D1F
AMD cpu00A70F80_ver0A708006_2024-01-12_AD8FB607
AMD cpu00A70F52_ver0A705205_2024-01-12_753FB641
Anti-Virus False Positives
Some Anti-Virus software may claim that the built/frozen/compiled MCE executable contains viruses. Any such detections are false positives, usually of PyInstaller. You can switch to a better Anti-Virus software, report the false positive to their support, add the MCE executable to the exclusions, build/freeze/compile MCE yourself or use the Python script directly.
Copyright (C) 2016 platomav