Image: Malwarebytes Labs
In the ever-evolving landscape of cyber threats, a new malevolent force emerged in 2022, known as MetaStealer. This potent malware, built on the foundational code of RedLine, quickly became a coveted tool in the criminal underworld, sparking rivalry among various groups. MetaStealer found its way into systems primarily through malspam and cracked software distributed via hijacked YouTube accounts. However, its deployment through a malvertising campaign marked a new and alarming tactic.
Recently, Malwarebytes Labs unearthed malicious ads that weren’t disseminating the typical FakeBat or PikaBot but were instead deploying MetaStealer. In an intriguing turn of events, the malware authors behind MetaStealer divulged in an early December interview their plans to unleash a new, enhanced version of their nefarious tool.

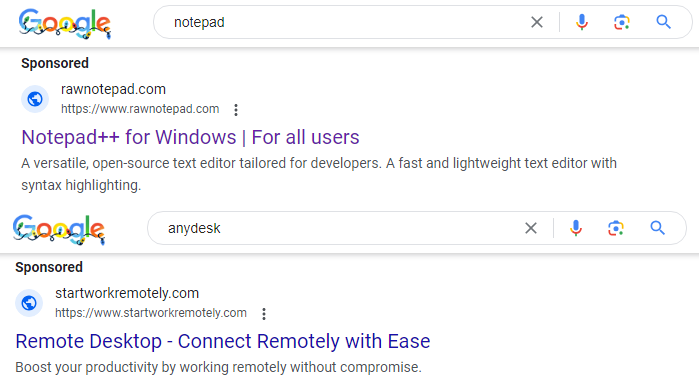
This campaign’s sophistication is evident in its distribution method. Malwarebytes Labs intercepted deceptive ads for Notepad++ and AnyDesk that appeared in Google searches. Ingeniously, the perpetrators set up domains that served dual purposes: as decoy and landing pages. To the unsuspecting eye, these sites mimicked automatically generated content. However, users lured by the ads and meeting certain criteria were redirected to malicious landing pages, where a perilous download awaited.
MetaStealer’s payload evolved over time. The November variant utilized a PowerShell shortcut with a hardcoded path, limiting its efficacy to specific conditions. By December, the campaign evolved, dispensing with PowerShell and recompiling the malicious DLL.
In-depth analysis revealed that these payloads remained true to the MetaStealer’s 3.x branch lineage. The developers of MetaStealer are not only refining their product but are also expanding its distribution channels. As a result, stealers serve multiple insidious purposes, coveting items like crypto wallets and credentials for various online services. They also act as gateways for initial access brokers, setting the stage for ransomware attacks.
Malwarebytes Labs has responded by reporting these malicious ads to Google and blocking the infrastructure supporting these campaigns. As the threat landscape continues to morph, the vigilance and proactive measures of cybersecurity entities remain our primary shield against these hidden dangers.