meterpeter: C2 Powershell Command & Control Framework
meterpeter
meterpeter – This PS1 starts a listener Server on a Windows|Linux attacker machine and generates oneliner PS reverse shell payloads obfuscated in ANCII|BXOR with a random secret key and another layer of Characters/Variables Obfuscation to be executed on the victim machine (The payload will also execute AMSI reflection bypass in the current session to evade AMSI detection while working). You can also receive the generated oneliner reverse shell connection via netcat. (in this case, you will lose the C2 functionalities like a screenshot, upload, download files, Keylogger, AdvInfo, PostExploitation, etc)
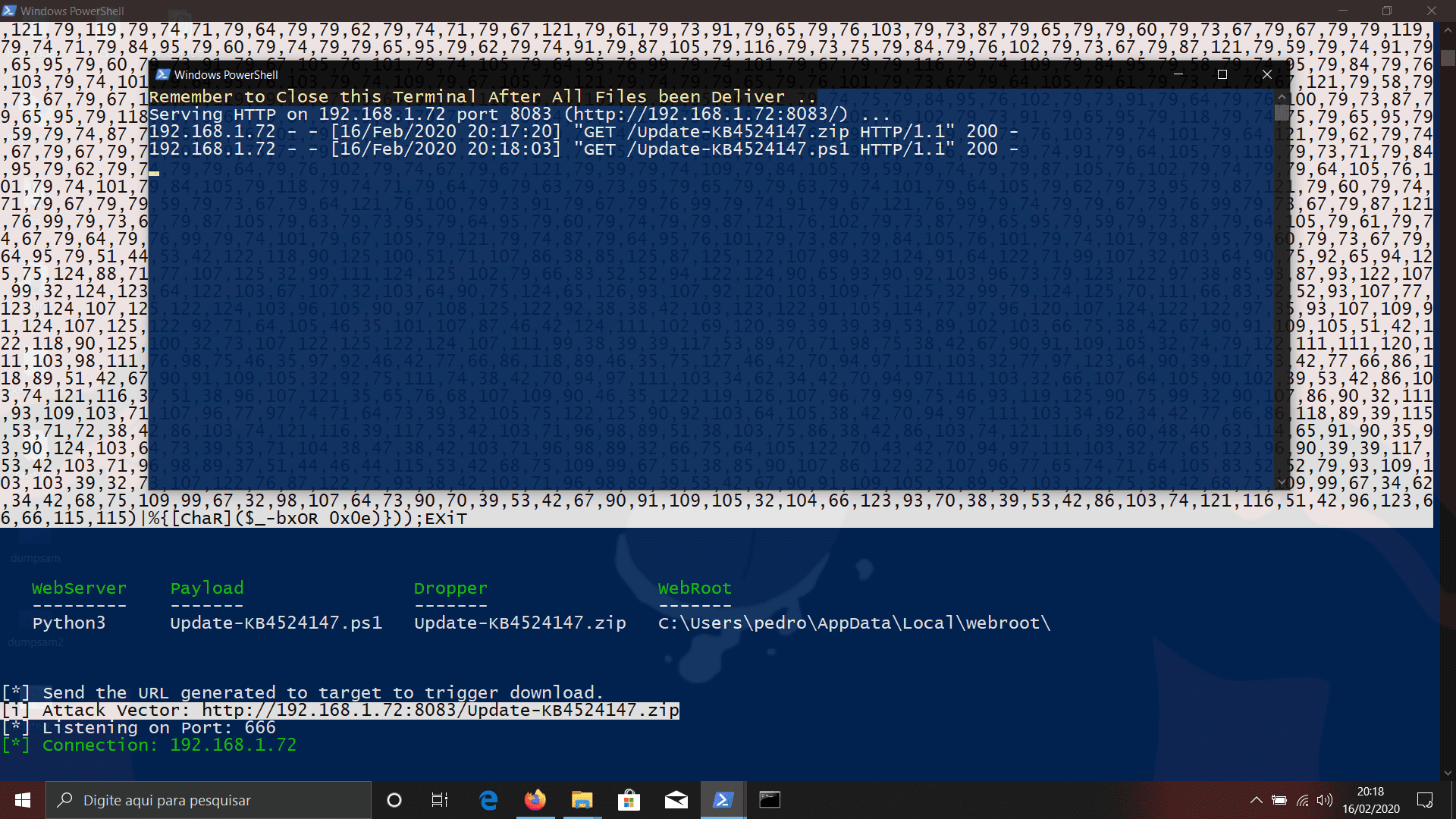
meterpeter payloads/droppers can be executed using User or Administrator Privileges depending on the scenario (executing the Client as Administrator will unlock ALL Server Modules, amsi bypasses, etc.). Droppers will mimic a Fake KB Security Update while in background Downloads and execute our Client in $env:tmp trusted location, with the intent of evading Windows Defender Exploit Guard. meterpeter payloads|droppers are FUD (dont test samples on VirusTotal).
This Project allows Attackers to execute ‘meterpeter.ps1’ under ‘Linux’ or ‘Windows’ distributions. Under Linux, distros users are required to install powershell and apache2 webserver, Under Windows it’s optional to install python3 http.server to deliver payloads under LAN networks. If these requirements are NOT met, then Client will be written in meterpeter working directory for manual deliver <- On this occasion execute your Client.ps1 in $env:tmp (‘recommended).
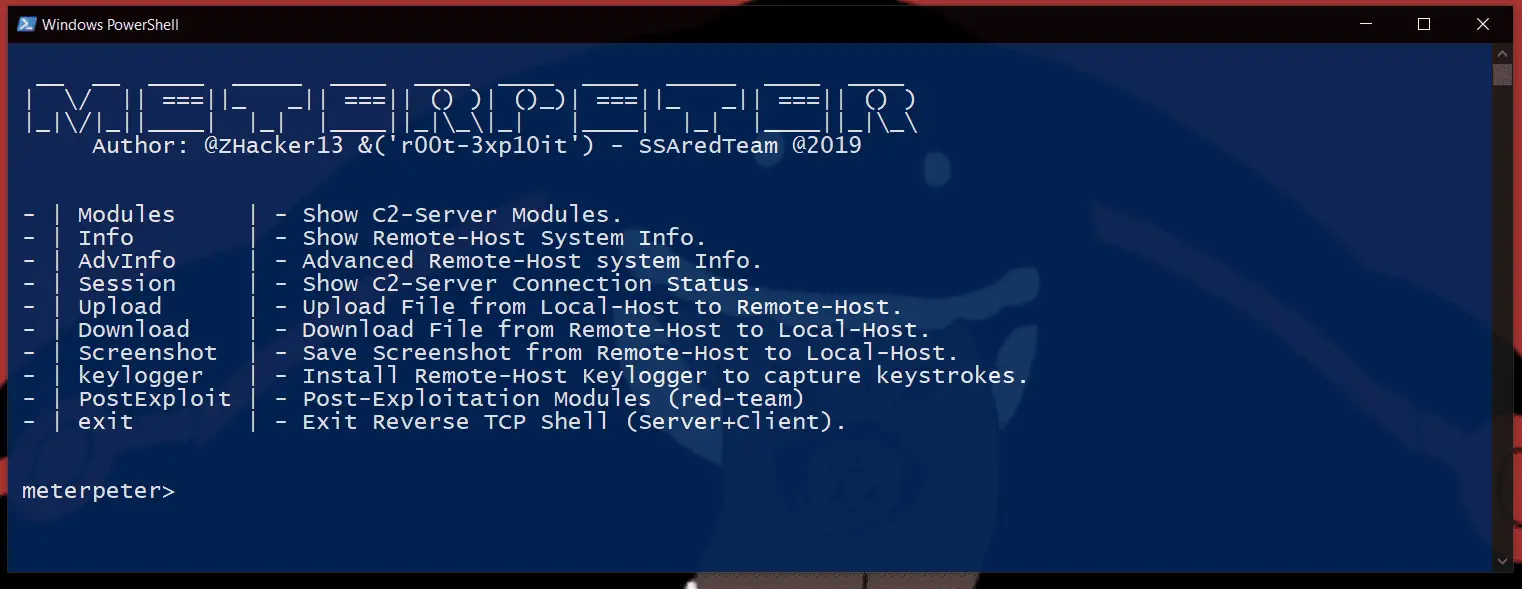
meterpeter (Server) available modules
- Info : Quick Retrieve of Target PC Information
- AdvInfo : Advanced Gather Information Modules (Sub-Menu)
- ListAdm : Retrieve Client Shell Path|Privileges
- ListAcc : Retrieve Remote-Host Accounts List
- ListSmb : Retrieve Remote-Host SMB shares List
- ListDns : Retrieve Remote-Host DNS Entrys List
- ListApp : Retrieve Remote-Host Installed Applications List
- ListTask : Remote-Host Schedule Tasks Module (Sub-Menu)
- Check : Retrieve Schedule Tasks List
- Inform : Schedule Taks Verbose Information
- Create : Create Remote-Host New Tasks
- Delete : Delete Remote-Host Tasks
- ListRece : Retrieve Remote-Host Recent Folder Contents
- ListPriv : Remote-Host Weak Service|Folders permissions (Sub-Menu)
- Check : Retrieve Folder Permissions
- WeakDir : Search for Folders weak Permissions recursive
- Service : Search for Unquoted Service Paths vulnerability
- RottenP : Search for Rotten Potato Privilege Vulnerability
- RegACL : Search for weak permissions on registry
- StartUp : Retrieve Remote-Host StartUp Folder Contents
- ListDriv : Retrieve Remote-Host Drives Available List
- ListRun : Retrieve Remote-Host Startup Run Entrys
- ListProc : Remote-Host Processe(s) (Sub-Menu)
- Check : Retrieve Remote Processe(s) Running
- KillProc : Kill Remote Process By DisplayName
- ListConn : Retrieve Remote-Host Active TCP Connections List
- ListIpv4 : Retrieve Remote-Host IPv4 Network Statistics List
- ListWifi : Remote-Host Profiles/SSID/Passwords (Sub-Menu)
- ListProf : Retrieve Remote-Host wifi Profile
- ListNetw : Retrieve wifi Available networks List
- ListSSID : Retrieve Remote-Host SSID Entrys List
- SSIDPass : Retrieve Stored SSID passwords
- Session : Retrieve C2 Server Connection Status.
- Upload : Upload File from Local-Host to Remote-Host.
- Download : Download File from Remote-Host to Local-Host.
- Screenshot : Save Screenshot from Remote-Host to Local-Host.
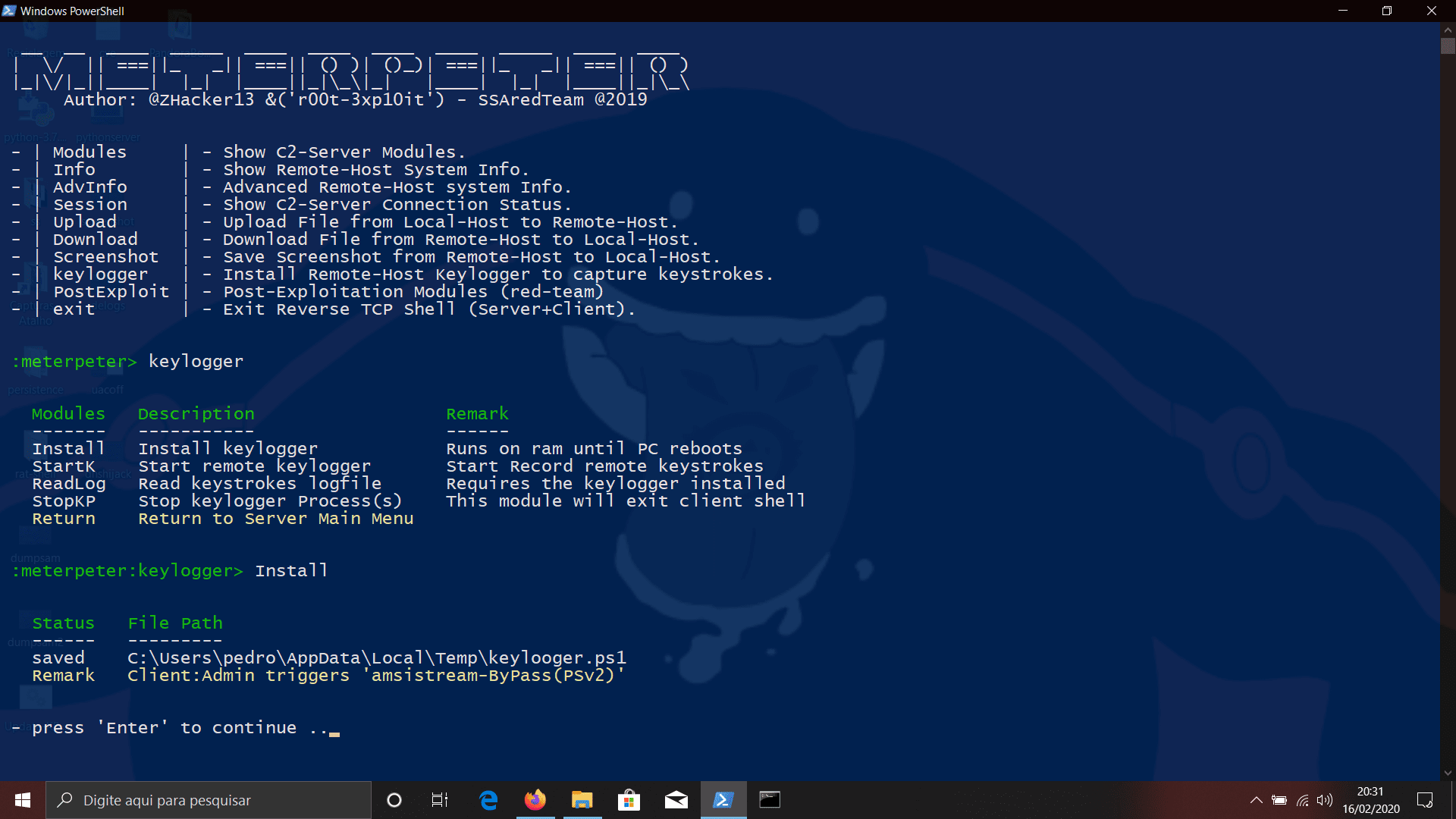
- keylogger : Remote-Host Keylogger (Sub-Menu)
- Install : Install Remote keylogger
- StartK : Start remote keylogger
- ReadLog : Read keystrokes logfile
- StopKP : Stop keylogger Process(s)
- PostExploit: Post-Exploitation Modules (Sub-Menu)
- Escalate : WSReset.exe Privilege Escalation (Sub-Menu)
- SluiEOP : Execute one command with admin privs (SYSTEM)
- Getsystem : Escalate Client Privileges (UserLand -> SYSTEM)
- Delete : Delete Old Priv Escalation Configurations
- CamSnap : Manipulate remote webcam (sub-menu)
- Device : List Remote-Host webcams available
- Snap : Take Remote-Host screenshot (Default webcam)
- Manual : Manual sellect webcam device to use (device name)
- Persist : Remote Persist Client (Sub-Menu)
- Beacon : Persiste Client Using startup Folder (beacon home from xx to xx sec)
- RUNONCE : Persiste Client using REGISTRY:RunOnce Key
- REGRUN : Persiste Client using REGISTRY:Run Key
- Schtasks : Make Client Beacon Home with xx minuts of Interval
- WinLogon : Persiste Client using WinLogon REGISTRY:Userinit Key
- Restart : Restart in xx seconds
- ListLog : List/Delete EventLogs Module (Sub-Menu)
- Check : Retrieve Remote-Host EventLogs List
- DelLogs : Delete Remote-Host EventLogs (eventvwr)
- DelFull : Delete Remote-Host LogFiles from Disk
- SetMace : Change files date/time TimeStomp
- ListPas : Search for passwords in txt Files
- ListDir : Search for hidden folders recursive
- GoogleX : Open Remote Browser in google sphere (prank)
- LockPC : Lock Remote workstation (prank|refresh explorer)
- SpeakPC : Make Remote-Host Speak your sentence (prank)
- AMSIset : Enable/Disable AMSI Module (Sub-Menu)
- Disable : Disable AMSI in REGISTRY:hklm|hkcu
- Enable : Enable AMSI in REGISTRY:hklm|hkcu
- ListCred : Retrieve Remote-Host cmdkey stored Creds
- UACSet : Enable/Disable remote UAC Module (Sub-Menu)
- Disable : Disable UAC in REGISTRY:hklm
- Enable : Enable UAC in REGISTRY:hklm
- ASLRSet : Enable/Disable ASLR Module (Sub-Menu)
- Disable : Disable ASLR in REGISTRY:hklm
- Enable : Enable ASLR in REGISTRY:hklm
- TaskMan : Enable/Disable TaskManager Module (Sub-Menu)
- Disable : Disable TaskManager in REGISTRY:hklm
- Enable : Enable TaskManager in REGISTRY:hklm
- Firewall : Enable/Disable Remote Firewall Module (Sub-Menu)
- Check : Review Remote-Host Firewall Settings
- Disable : Disable Remote-Host Firewall
- Enable : Enable Remote-Host Firewall
- Defender : Enable/Disable Windows Defender Module (Sub-Menu)
- Disable : Disable Remote-Host Windows Defender
- Enable : Enable Remote-Host Windows Defender
- DumpSAM : Dump SAM/SYSTEM Credentials to a remote location
- Dnspoof : Hijack Entrys in hosts file Module (Sub-Menu)
- Check : Review Remote-Host hosts File
- Spoof : Add Entrys to Remote-Host hosts File
- Default : Defaults Remote-Host hosts File
- NoDrive : Hide Drives from Explorer Module (Sub-Menu)
- Disable : Hide Drives from explorer in REGISTRY:hklm
- Enable : Enable Drives from explorer in REGISTRY:hklm
- CredPhi : Phishing for remote logon credentials
- OldBox : Trigger Remote Phishing PS Script (Windows 7 or less)
- NewBox : Trigger Remote Phishing PS Script (Windows 7 or above)
- ReadLog : Read Remote Phishing LogFile
- Browser : Enumerate Installed Browsers (IE,FIREFOX,CHROME)
- Escalate : WSReset.exe Privilege Escalation (Sub-Menu)
- exit : Exit Reverse TCP Shell (Server + Client).