Microsoft Acts Against Malware: MSIX ms-appinstaller Handler Disabled
In a digital landscape where cyber threats are constantly evolving, Microsoft’s latest Threat Intelligence report, covering activity since mid-November 2023, sheds light on the sophisticated strategies employed by cybercriminals. The report reveals a disturbing trend: the exploitation of the ms-appinstaller URI scheme (App Installer) by threat actors, including financially motivated groups like Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674, to distribute malware.
These actors have been utilizing the ms-appinstaller protocol handler as a vector for malware, potentially leading to ransomware distribution. This tactic allows these malicious entities to bypass security mechanisms like Microsoft Defender SmartScreen and browser warnings for executable file downloads.
1. Storm-0569: Observed in early December 2023, Storm-0569 has been distributing BATLOADER via SEO poisoning, creating fake sites for legitimate software like Zoom and AnyDesk. This sophisticated approach involves using PowerShell and batch scripts, leading to malware like Black Basta ransomware deployment.
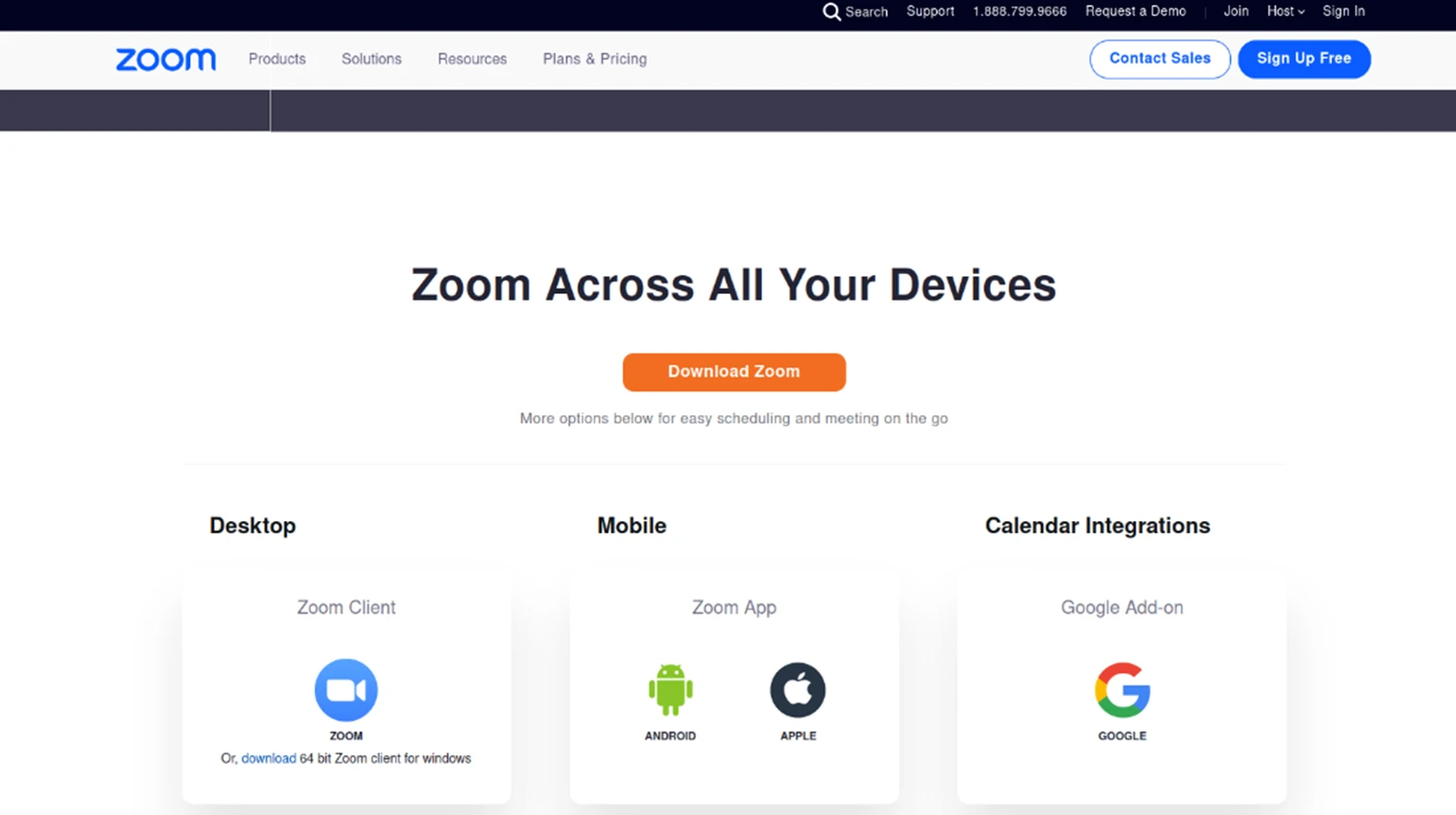
A malicious landing page spoofing Zoom accessed via malicious search engine advertisement for Zoom downloads

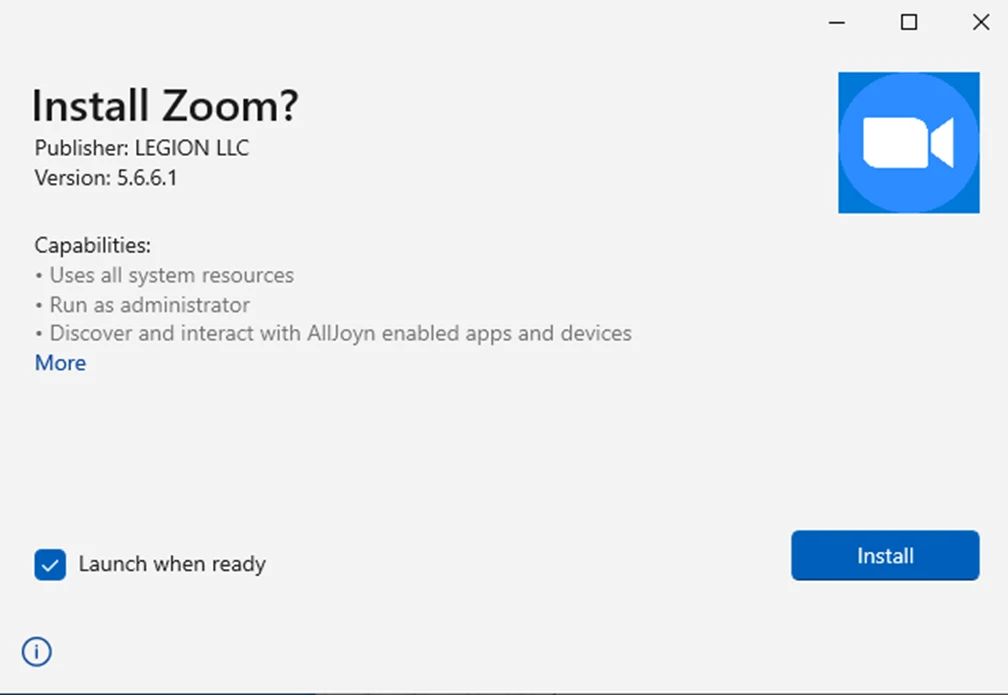
Sample malicious App Installer experience. Note the Publisher is not who a user should expect to be publishing this software.
2. Storm-1113: Since mid-November 2023, Storm-1113 has been deploying EugenLoader through search ads impersonating popular software. This malware leads to the download of various payloads, including IcedID and Lumma stealer, marking Storm-1113 as a significant threat.
3. Sangria Tempest: Using Storm-1113’s infrastructure, Sangria Tempest has been observed deploying Carbanak and Gracewire malware through malicious MSIX package installations. This group, known for data theft and ransomware deployment, has a long history of cybercrime dating back to 2014.
4. Storm-1674: This group has been exploiting Microsoft Teams to deliver fake landing pages, and spoofing services like OneDrive and SharePoint. Storm-1674 is an access broker known for distributing DarkGate malware and has been linked to Black Basta ransomware deployment.
In response to these threats, Microsoft has disabled the ms-appinstaller protocol handler by default in App Installer build 1.21.3421.0. They have also provided a series of recommendations to mitigate the impact of these threats, emphasizing the importance of phishing-resistant authentication methods, educating users on verifying external communications in Teams, and encouraging the use of secure browsers like Microsoft Edge supported by Defender SmartScreen.
Microsoft’s report is a stark reminder of the ever-evolving nature of cyber threats. By understanding the strategies of these threat actors, we can better prepare and protect against them. The report underlines the importance of staying vigilant, continuously updating security measures, and educating users about potential risks.