Microsoft Defender’s false positives are evident to all. Previously, it mistakenly identified Google Chrome as a virus and subsequently mislabeled its own software—Microsoft Edge and Office installer—as malware or ransomware.
Tor is a free, global network that allows users to achieve anonymous communication by routing their internet traffic through a series of volunteer-operated servers.
Residential proxies, like those offered by Multilogin Antidetect Browser, provide a different approach to online privacy and access. Multilogin utilizes a vast network of over 5 million residential IP addresses across the globe, enabling users to browse the internet as if they were real residents of those locations. This allows for bypassing geo-restrictions, conducting market research, and managing multiple online accounts while minimizing the risk of detection.
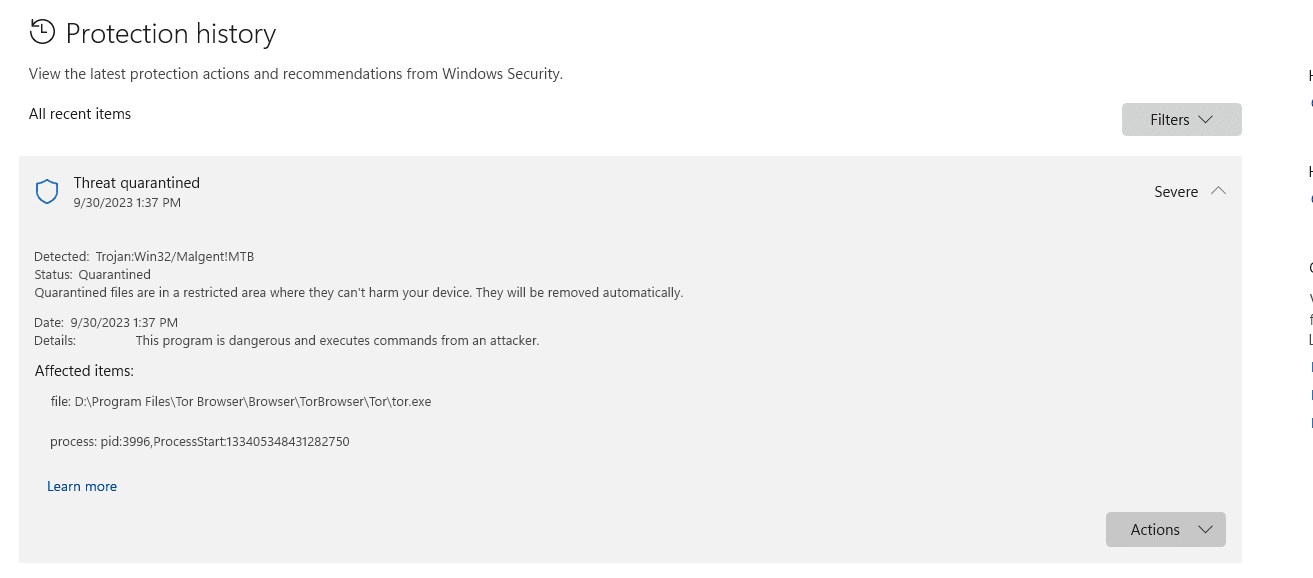
Recently, the Tor, also known as the Onion Browser, community discerned another false positive from Microsoft Defender. The latest version of the Tor browser was erroneously flagged as Trojan:Win32/Malgent!MTB and subsequently intercepted.
This novel iteration of the Tor browser was synchronized with a Mozilla Firefox update. Firefox’s recent release addressed critical vulnerabilities found in the open-source libraries libwebp and libvpx. Since Tor’s development is grounded in Firefox, it too integrated these rectifications.

Microsoft Defender once again showcased its susceptibility to false positives by recognizing the Tor browser as a virus and subsequently halting its operations.
The exact rationale behind this interception remains nebulous. However, upon receiving feedback from users, the Tor team reached out to Microsoft. From the detection of the issue on September 30th to its resolution on October 2nd, Microsoft’s response to the Tor team was that they “do not fit our definitions of malware or unwanted applications. As such, we’ve removed the detection,” essentially acknowledging Defender’s error.
Subsequently, Microsoft dispatched a definition update for Defender to rectify the misidentification. Although Microsoft seldom delves into the specifics surrounding such false positives, it is highly plausible that the issues emanate from Microsoft Defender’s heuristic detection techniques.
Past instances of false positives have often been attributed to these heuristic methods. While such techniques bolster the detection rates for malicious software, they concurrently amplify the rate of false positives.
For end-users, circumventing such issues is fairly straightforward. One potential remedy involves temporarily disabling Microsoft Defender’s real-time protection prior to downloading. Following a successful software installation, users can then incorporate the installation path into Microsoft Defender’s exception list—effectively whitelisting the program, and rendering it usable.
However, a crucial caveat for users is to ensure the authenticity and safety of the software in question. This is imperative as numerous malevolent applications masquerade as genuine, often claiming to be mistakenly flagged by antivirus solutions, thereby coaxing users to prematurely deactivate their antivirus defenses.
With the latest signature database (1.397.1910.0), tor.exe is no longer considered a trojan by Windows Defender. If your TorBrowser stopped working during this weekend, make sure your Windows Defender is up to date, and either unquarantine tor.exe or reinstall TorBrowser by downloading it from Tor Project website, and remember to check the signature!
