Malicious remote connection | Image: Microsoft
Microsoft Threat Intelligence has issued a warning about a new spear-phishing campaign orchestrated by the Russian state-sponsored threat actor Midnight Blizzard (also known as APT29, UNC2452, and Cozy Bear). This campaign, active since October 22, 2024, targets individuals in government, academia, defense, non-governmental organizations, and other sectors across over 100 organizations.
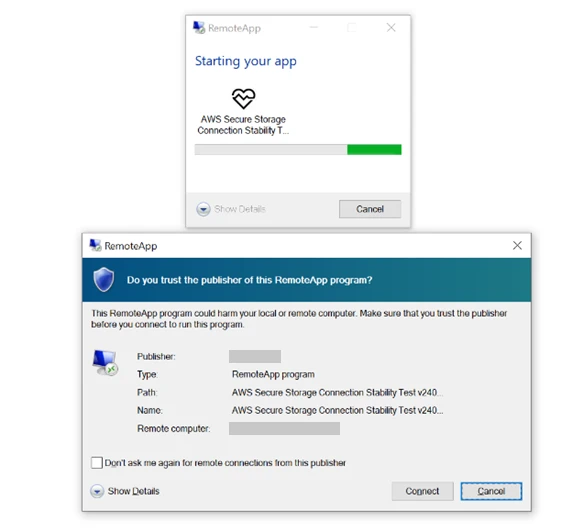
“Based on our investigation of previous Midnight Blizzard spear-phishing campaigns, we assess that the goal of this operation is likely intelligence collection,” Microsoft stated in their report. This latest campaign employs a novel tactic for the group: using signed RDP (Remote Desktop Protocol) configuration files to gain access to victims’ devices.
The spear-phishing emails are highly targeted, leveraging social engineering lures related to Microsoft, Amazon Web Services (AWS), and the concept of Zero Trust. In some instances, “the actor attempted to add credibility to their malicious messages by impersonating Microsoft employees,” according to the report.
The malicious .RDP file attachments contain settings that enable extensive information exposure. “Once the target system was compromised, it connected to the actor-controlled server and bidirectionally mapped the targeted user’s local device’s resources to the server,” Microsoft explained. This access grants the attackers the ability to:
- Access files and directories
- View connected network drives
- Control connected peripherals, including smart cards and printers
- Capture web authentication data
- Steal clipboard data
The campaign primarily targets organizations in the United Kingdom, Europe, Australia, and Japan, aligning with Midnight Blizzard’s historical focus on governments, diplomatic entities, NGOs, and IT service providers.
Microsoft emphasizes that these attacks “do not represent any new compromise of Microsoft” and are utilizing email addresses “belonging to legitimate organizations that were gathered during previous compromises.”
The tech giant is actively notifying affected customers and providing guidance on securing their accounts. “Strong anti-phishing measures will help to mitigate this threat,” Microsoft advises. They are also releasing indicators of compromise (IOCs), hunting queries, and detection details to aid in defense against this campaign.
Organizations and individuals must remain vigilant, employing robust security measures and educating themselves about evolving attack techniques.
Related Posts:
- Midnight Blizzard Accesses Microsoft Internal Systems and Source Code
- Russian Hackers Midnight Blizzard Compromise Microsoft’s Email Data
- Patch Now: Forest Blizzard Targets Exchange Servers with Outlook Zero-Day Exploit
- Blizzard Games exisits critical flaw that conduct DNS Rebinding attack
- From Spear-Phishing to Zero-Day: Lazarus Group’s Latest Cyber Strategies