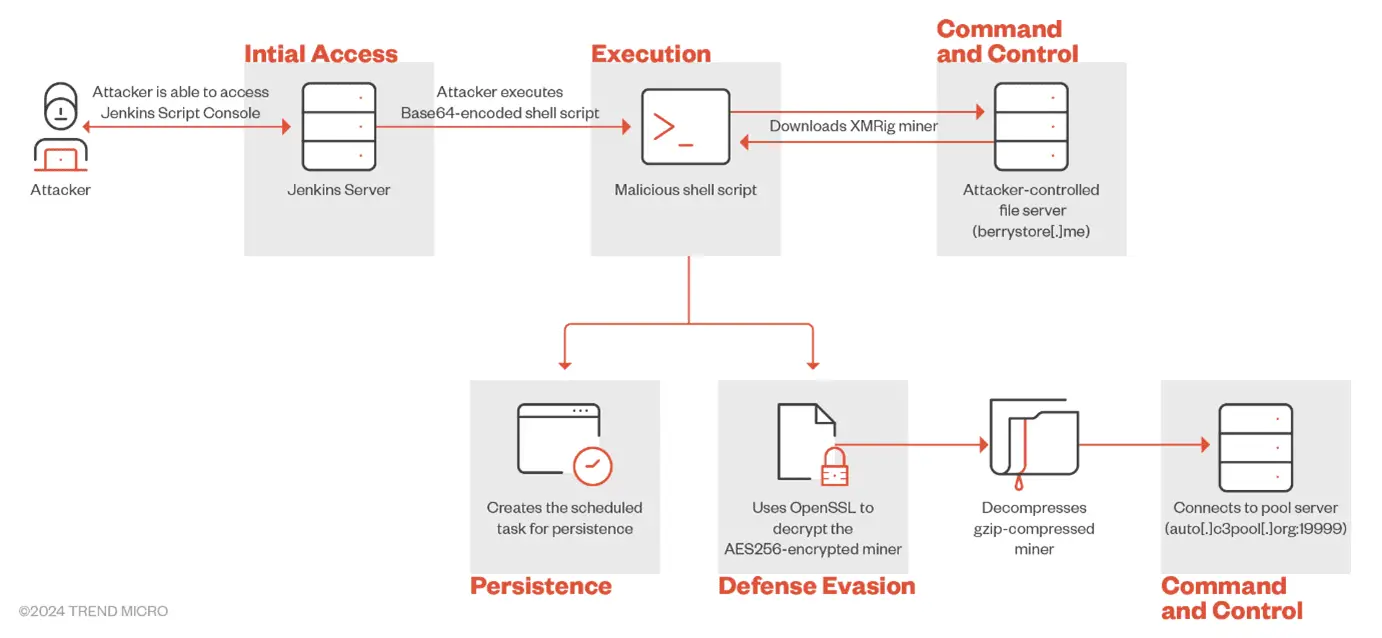
Infection chain
Trend Micro, a global leader in cybersecurity, has issued a warning about a recent wave of attacks targeting misconfigured Jenkins servers. Cybercriminals are exploiting vulnerabilities in the Jenkins Script Console to illicitly install and operate cryptocurrency mining software, siphoning computational resources from unsuspecting organizations.
The Jenkins Script Console, a tool allowing administrators and authorized users to execute Groovy scripts directly on the Jenkins server, is at the heart of this issue. By default, this console is restricted to authenticated users with administrative permissions. However, misconfigurations—such as improperly set authentication mechanisms or enabled “Sign Up” or “Registration” options—can expose Jenkins to unauthorized access and remote code execution (RCE).
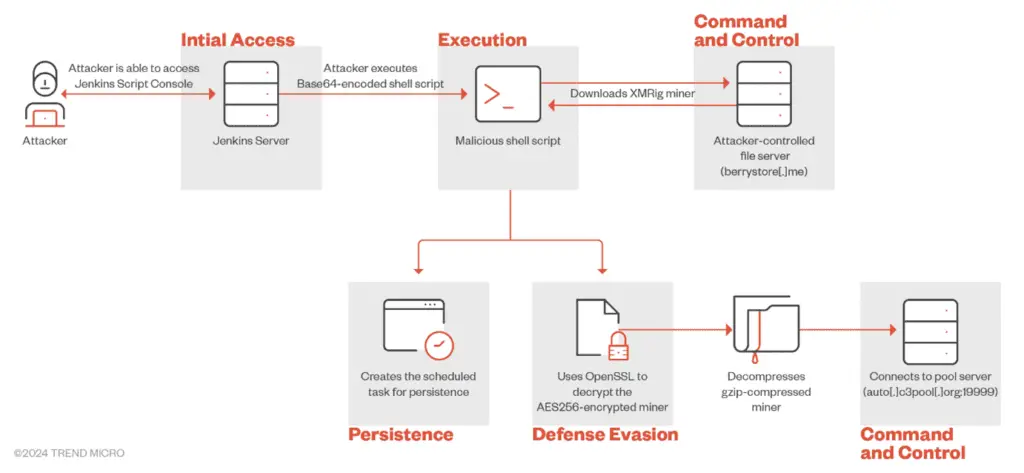
Attack Methodology
- Initial Access and Script Execution: Malicious actors search for exposed Jenkins servers using tools like Shodan. Upon gaining access, they exploit misconfigurations in the Groovy plug-in to execute Base64-encoded malicious scripts via the Script Console.
- Resource Management and Persistence: The script checks system resources, terminating processes consuming over 90% of CPU resources to ensure efficient mining. It then searches writable directories to store the cryptominer, defaulting to /tmp if necessary and downloads the mining binary from a compromised website.
- Encryption and Decryption: The downloaded binary is an AES-256 encrypted tar file. Using OpenSSL, the script decrypts and extracts the file, assigning executable permissions and ensuring persistence through cron jobs and systemd-run commands.
- Execution and Evasion: The script uses various methods to ensure the miner runs persistently and evades detection. It sets traps to ignore termination signals, schedules execution using systemd-run and employs cron jobs to maintain the miner’s activity.
To safeguard Jenkins servers against this emerging threat, Trend Micro strongly recommends implementing the following security measures:
- Script Approval: Utilize the Script Approval feature to mandate manual review and authorization before executing any scripts on the server.
- Robust Authentication and Authorization: Enforce stringent access controls, including strong passwords, two-factor authentication, and role-based permissions, to limit access to the script console.
- Comprehensive Audit Logging: Regularly monitor audit logs for anomalies or unauthorized script execution, which may indicate a compromise.
- Network Segmentation: Isolate Jenkins servers from the public internet, minimizing exposure to potential attackers. Employ secure channels like VPNs for remote access if necessary.
- Timely Updates and Patching: Ensure Jenkins and all associated plugins are consistently updated with the latest security patches to address known vulnerabilities.