mx-takeover
mx-takeover focuses on DNS MX records and detects misconfigured MX records. It currently supports three-technique. These are,
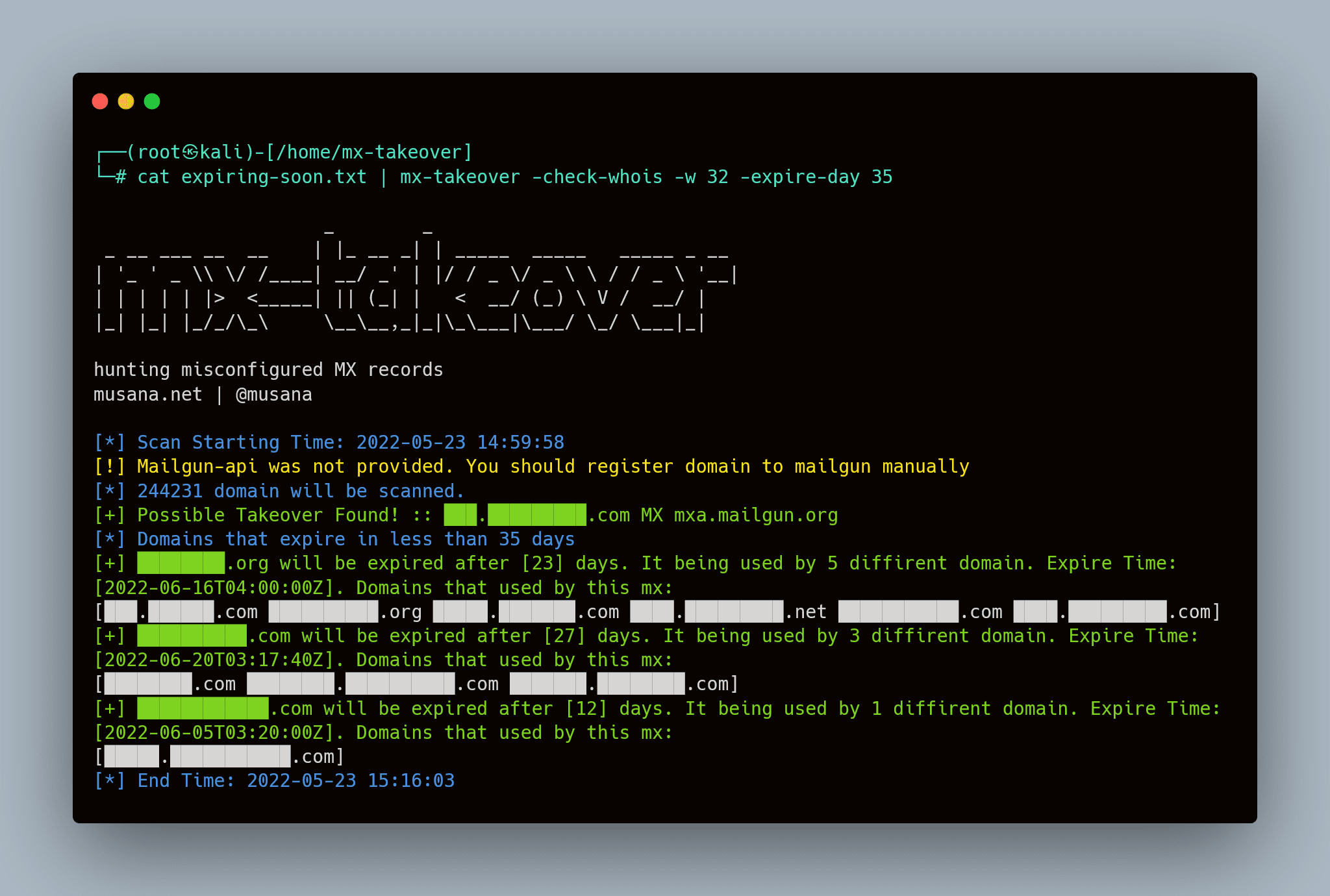
- MX domains that will expire soon
- Unregistered MX domains
- Domains that point to not currently in use by mailgun.
How to works
Attack Scenario for Mailgun
- Your company starts using a new service for emails.
- Your company’s mx record points to mailgun. (eg: sub.domain.com MX mxa.mailgun.com)
- Your company stops using mailgun but does not remove the mx record from DNS
- Attacker signs up for the mailgun and claims the domain as theirs. No verification is done by the mailgun, and the DNS setup is already correctly set up.
- An attacker can now read mail that is sent associated with the domain. (<something>@sub.domain.com)
Limitation
Mailgun uses MX records for mail receiving, TXT records for mail sending, and CNAME records for tracking. Of these records, only the DKIM record is unique and generated randomly.
Therefore, can not be sent mails on behalf of someone else, but can be read(receive) mails sent by someone else to the associated domain.
Features
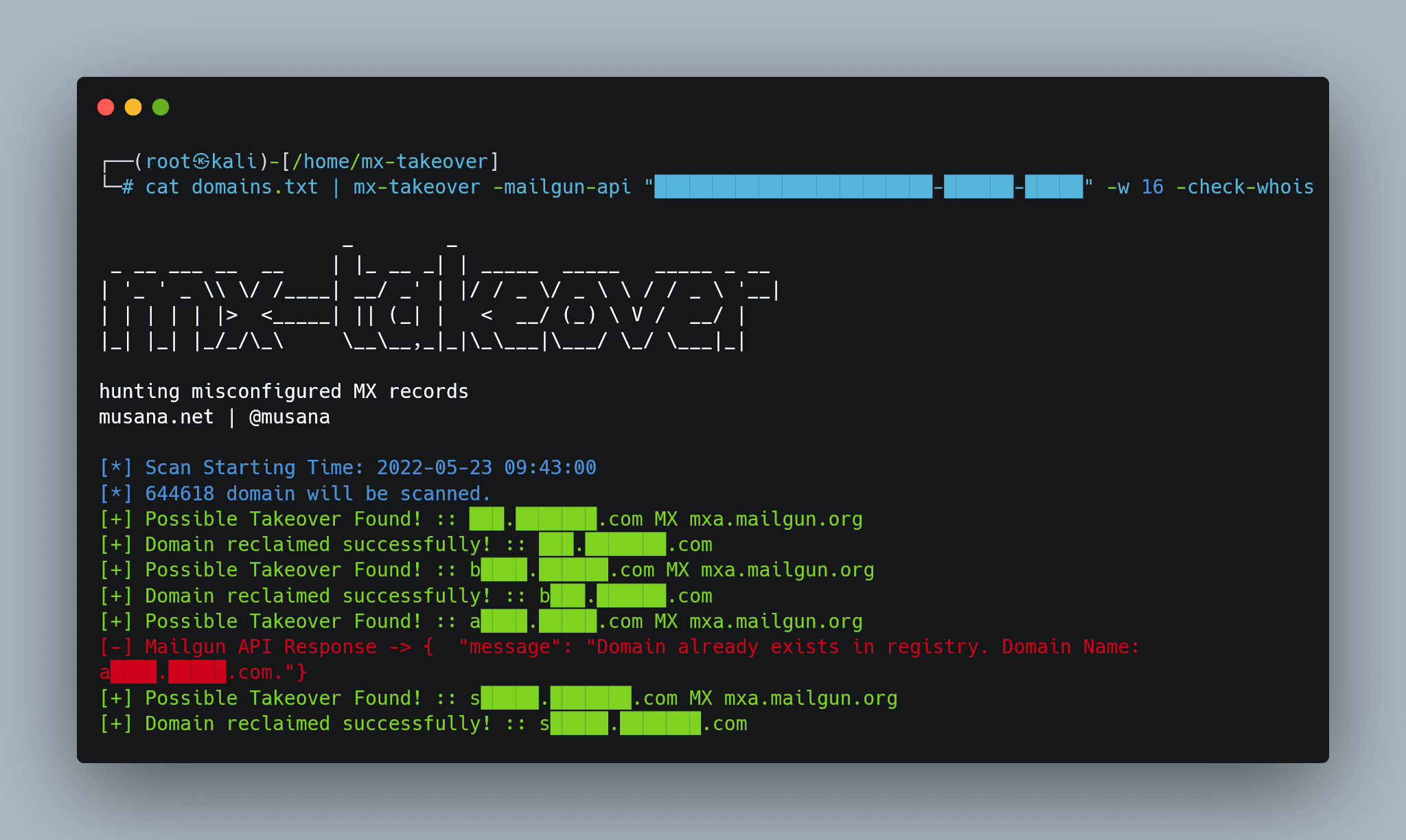
- Domains deleted in mailgun but MX records held
- Reclaiming domain automatically
- Unregistered/expired MX domain
- MX Domain that will expire soon
- Domains that used the same MX records
- Saving scan results as json format
- Support for concurrency
Install & Use
Copyright (c) 2022 musana