myBFF: a Brute Force Framework
myBFF is a web application brute force framework.
Point the framework at a file containing usernames, a host, and give it a password. The framework will determine what type of web application is in use, then attempt to brute force accounts. After brute forcing accounts, myBFF will then do a little more, like enumerating apps available and reading in important data. Each module is different so try them out!
Current modules:
- HP SiteScope (will attempt to give you a Meterpreter Shell!)
- Citrix Gateway (also enumerates authorized applications)
- Juniper Portal (Will look for 2FA bypass and list what is accessible)
- MobileIron (Unknown. Have to find out what is accessible first!)
- Outlook/Office365 (will parse email, contacts, and other data from email)
- WordPress (Will be adding “SomethingCool” soon)
- CiscoVPN (Enumerate User accounts (May does not work on all configurations))
- Okta (Enumerate Applications and check if 2FA is set up for the account)
- Jenkins (Will be adding “Something Cool” soon)
- SMB (Check if a user is an administrator) (must use –domain with this module. for the host, use smb://)
- FTP (List root dir contents)
Installing
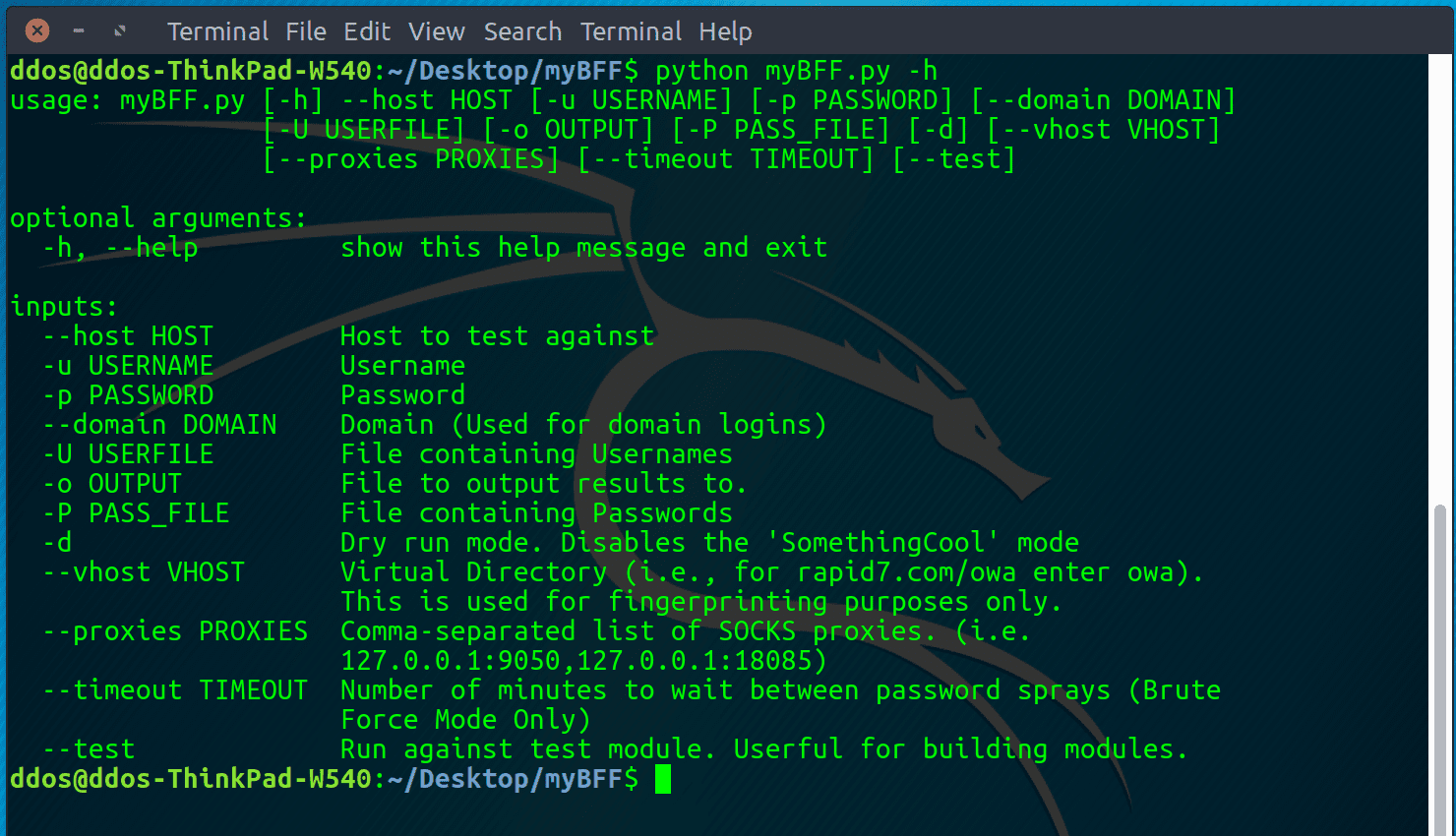
Usage
Copyright (c) 2016 Kirk Hayes
Source: https://github.com/MooseDojo/





