Project Neto is a Python 3 package conceived to analyze and unravel hidden features of browser plugins and extensions for well-known browsers such as Firefox and Chrome. It automates the process of unzipping the packaged files to extract these features from relevant resources in an extension like manifest.json, localization folders or Javascript and HTML source files.
Features
The following is a non-exhaustive list of the features included in this package are the following:
- Manifest analysis.
- Internal file hashing.
- Entities extraction using regular expressions: IPv4, email, cryptocurrency addresses, URL, etc.
- Comments extraction from HTML, CSS and JS files.
- Cryptojacking detection engine based on known mining domains and expressions.
- Suspicious Javascript code detection such as
eval(). - Certificate analysis if provided.
- Batch analysis of previously downloaded extensions.
Changelog v0.6.2
Several issues addressed:
- Add more suspicious categories to detect pattern recognition code, external connections and possible payments.
- Add suspicious strings to standard output
- Beautify outputs when the program is unable to process an extension because of incorrect extensions
- Fix an error in the storage of the data extracted from entities
Installation
Quick Start
To perform the analysis of an extension, the analyst can type the following:
neto analysis -u https://yoururl.com/extension-name.xpi
The extension will be automatically downloaded and unzipped by default in the system’s temporal folder.
However, the analyst can also launch de analysis towards a locally stored extension:
neto analysis -e ./my-extension-name.xpi
After the static analysis is performed, it will generate a Json file that is stored by default in a newly created folder named output.
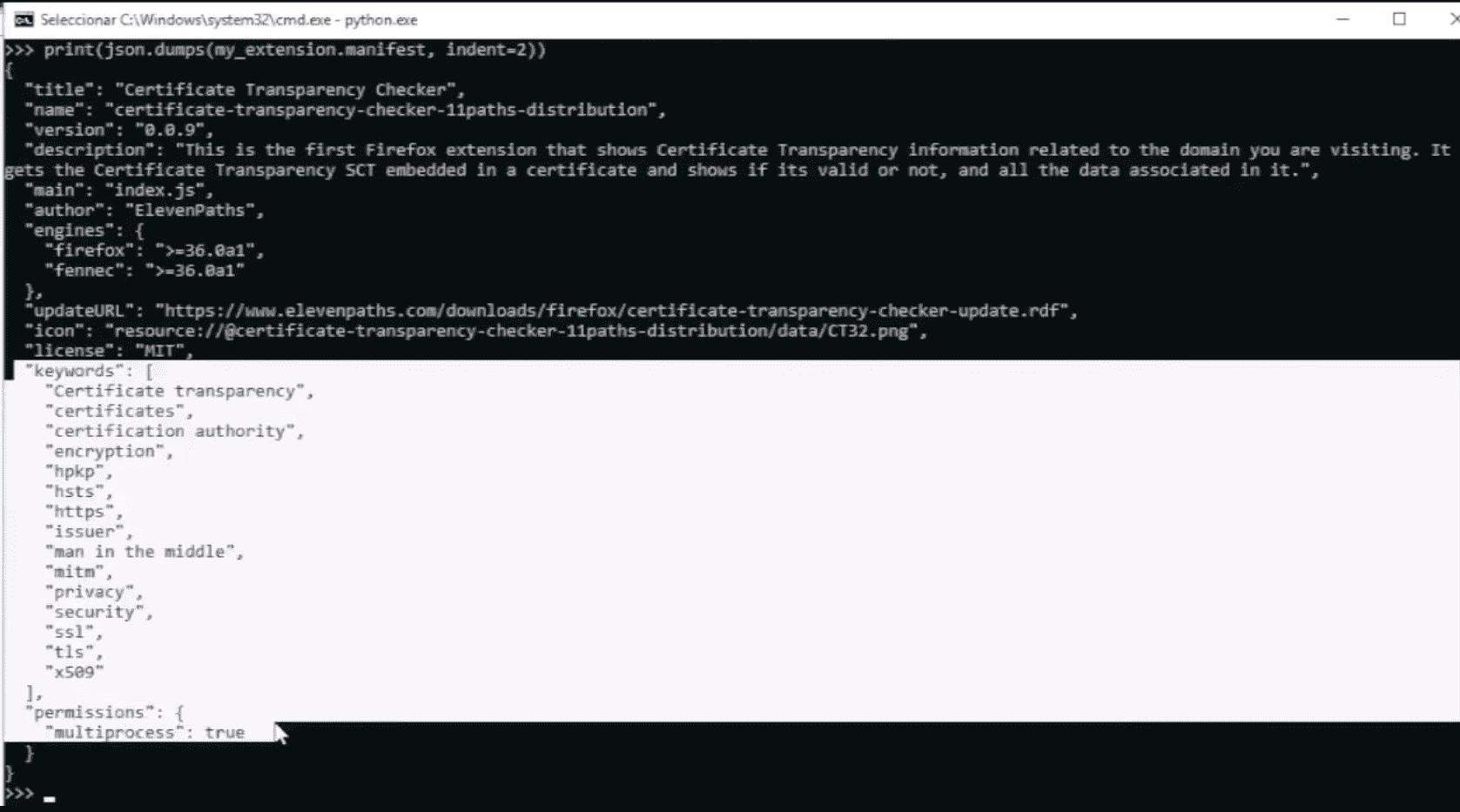
If you use Python, you can also import the package as a library in your own Python modules:
Apart from access to the elements found in the extension using properties, the analyst can always have access to it as a dictionary:
If you are not using Python, you can use the JSON RPC daemon:
You can then run commands using your preferred JSON RPC library to write a client
Demo
Copyright (C) Félix Brezo felix.brezo@11paths.com
Source: https://github.com/ElevenPaths/