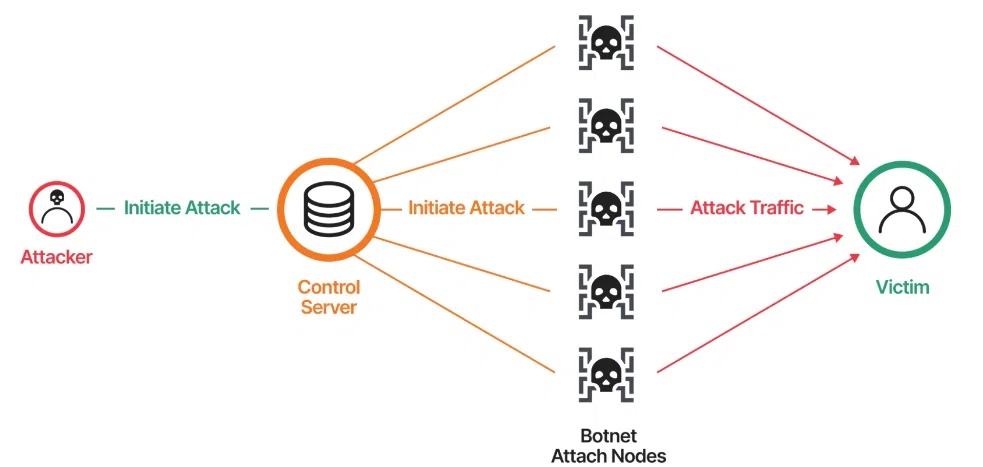
A new report from Imperva Threat Research reveals a concerning resurgence of the Mirai botnet, a notorious malware known for its history of large-scale distributed denial-of-service (DDoS) attacks. The research indicates that Mirai has evolved, incorporating artificial intelligence (AI) and machine learning to generate more sophisticated and evasive attacks, targeting over 1,200 websites in recent campaigns.
The team collected over 230 distinct malicious samples, including bash scripts and ELF binaries. Typically, the malware is delivered by exploiting known web vulnerabilities, which are used to execute shell commands like wget or curl. These commands download a stage 1 bash script, which then retrieves and executes a second-stage binary tailored to the architecture of the target server.

This surge in malicious URL delivery coincides with attackers increasingly leveraging AI and machine learning to generate sophisticated DDoS attacks. AI has significantly lowered the bar for launching such attacks, broadening the threat landscape. Polymorphic malware, if AI-generated, could evade detection and infect systems on a massive scale. The combination of AI-enhanced DDoS attacks and the resurgence of Mirai botnets presents a dual threat that organizations must be prepared to counter.
Mirai operates by scanning the internet for vulnerable devices, infecting them with malware, and then incorporating these compromised devices into a botnet. The botnet is subsequently used to launch DDoS attacks, overwhelming target websites and disrupting their services.
Mirai employs several strategies to evade detection and competition:
- Self-Deletion: Deleting itself from the file system after execution.
- Process Concealment: Removing itself from the process list and altering its name.
- Competition Blocking: Killing processes associated with competing botnets and taking over the system.
The resurgence of Mirai botnet variants, coupled with AI-enhanced DDoS attacks, underscores the critical need for robust cybersecurity measures. Organizations must stay vigilant, continuously updating their defenses to counter these evolving threats.