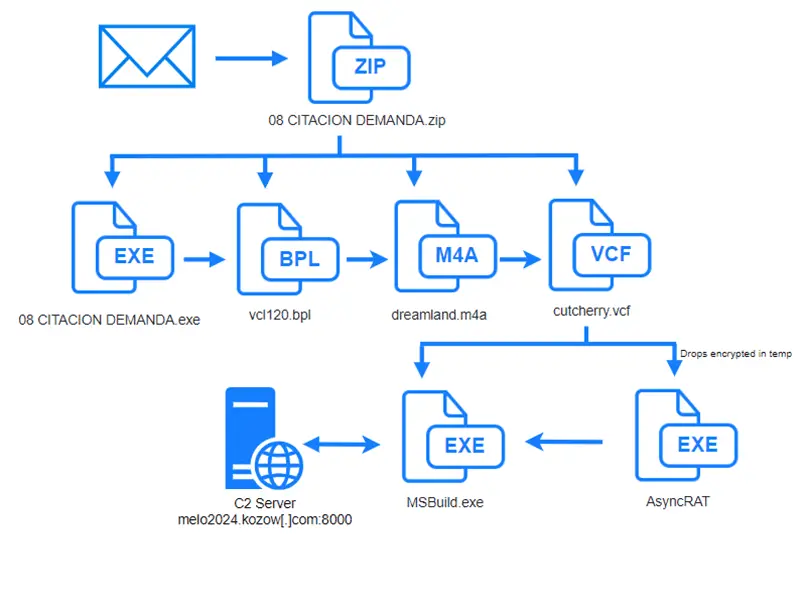
Current infection chain
Recently, S2 Grupo’s intelligence unit, Lab52, identified a sophisticated phishing campaign targeting Colombia. The attackers, masquerading as the Colombian Attorney General’s Office, aim to infect victims’ systems with the AsyncRAT malware. The campaign utilizes a complex DLL side-loading technique involving legitimate files from the IObit anti-malware solution to execute malicious payloads.

The attack begins with a phishing email containing a ZIP file named “08 CITACION DEMANDA.zip,” which includes:
- A legitimate IObit antivirus executable:
08 CITACION DEMANDA.exe - A malicious DLL file:
vcl120.bpl - A BPL file:
Register.dll - An Apple audio file:
dreamland.m4a - A VCF text format file:
cutcherry.vcf
When the executable 08 CITACION DEMANDA.exe is run, it triggers a chain of events where the malicious files are copied to the user’s AppData directory (C:\Users\XXXX\AppData\Roaming\WUKApp). The legitimate IObit file is used to load the malicious DLL vcl120.bpl through DLL side-loading, which in turn creates a cmd.exe process that initiates a suspended MSBuild process.
The attack chain commences with a seemingly legitimate IObit antivirus executable. However, this executable has been manipulated to exploit DLL side-loading, a technique that enables the loading of malicious code disguised as a legitimate library. This approach bypasses traditional security measures, allowing the attacker to gain a foothold on the victim’s system.
Following the initial compromise, the HijackLoader malware takes over, orchestrating the subsequent stages of the attack. It deploys additional malicious payloads disguised as innocuous audio (M4A) and text (VCF) files.
The final stage involves the injection of AsyncRAT into a legitimate process, establishing a covert communication channel with the attacker’s command-and-control server. This grants the attacker extensive control over the compromised system, enabling data exfiltration, surveillance, and further malware deployment.
While the use of AsyncRAT aligns with known tactics employed by the advanced persistent threat group APT-C-36, the specific infection chain observed in this campaign deviates from recent patterns. This suggests a potential evolution in the group’s tactics, techniques, and procedures (TTPs), underscoring the need for heightened vigilance and proactive threat detection.