Attack flow of PG_MEM | Image: Aqua Nautilus
A new and insidious threat has emerged, targeting the widely used PostgreSQL database management system. Aqua Nautilus researchers have identified a novel malware strain, named “PG_MEM,” which employs a sophisticated blend of brute-force attacks, payload obfuscation, and resource exploitation to achieve its ultimate goal: cryptocurrency mining at the expense of unsuspecting victims.
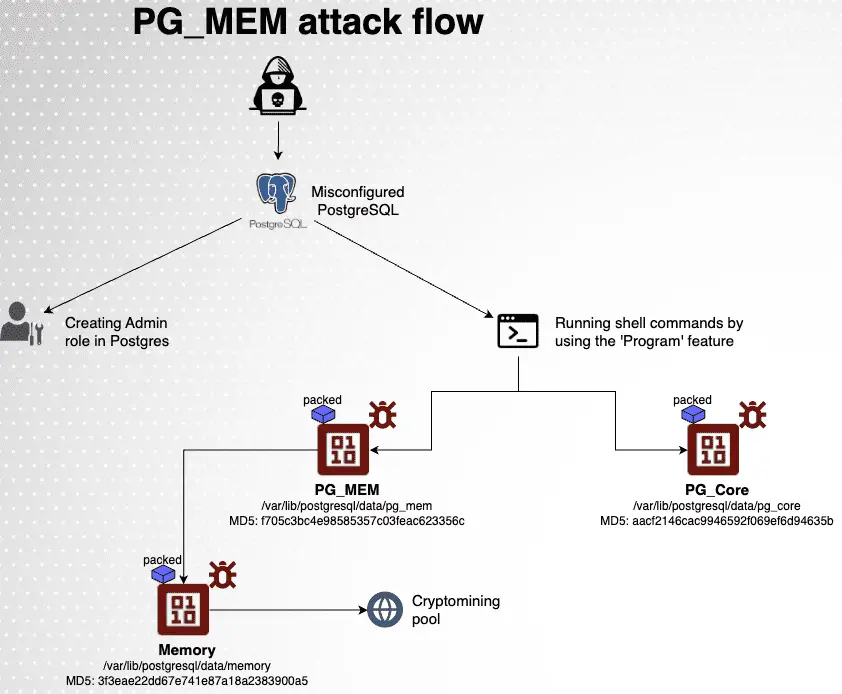
The attack begins with a relentless brute force assault, relentlessly attempting to guess database passwords until it breaches the defenses. Once inside, PG_MEM deploys a series of malicious payloads designed to entrench itself within the system. It manipulates user roles, eliminates potential competition, and deftly covers its tracks to avoid detection.
- Privilege Escalation: After gaining access, the attacker creates a new superuser role, effectively locking out other potential intruders by stripping the original user of their superuser privileges.
- System Discovery: The attacker then gathers critical system information, including configuration details and PostgreSQL version data. This reconnaissance is crucial for the next steps of the attack.
- Payload Delivery: Using PostgreSQL’s “COPY … FROM PROGRAM” command, the attacker executes shell commands on the host system. Two files, named
pg_coreandpg_mem, are downloaded and executed. These files are carefully designed to eliminate competition, evade detection, and optimize the attacker’s crypto-mining operations. - Crypto-Mining Operations: The
pg_memfile acts as a dropper for an XMRIG cryptocurrency miner, further embedding the attacker’s presence within the system. This miner is set up to run persistently, ensuring ongoing illicit profit for the attackers.
PG_MEM’s creators have employed several tactics to ensure their malware remains undetected:
- Temporary Tables: The attacker frequently uses temporary tables to store and execute commands, clearing them immediately after use with the
TRUNCATEcommand. This minimizes the digital footprint left behind. - Process and File Management: The malware actively stops competing processes, such as other miners or security tools, and deletes logs and binaries associated with the attack, making it difficult for defenders to trace the malicious activity.
- Persistence Mechanisms: PG_MEM ensures its continued operation by creating cron jobs that restart the crypto-mining process even after system reboots.
The final stage of the PG_MEM attack involves deploying the XMRIG cryptocurrency miner. This malicious software silently operates in the background, consuming CPU and GPU resources to generate cryptocurrency for the attackers. The victim may experience sluggish performance, increased power consumption, and potentially even system instability, all while unknowingly contributing to the cybercriminals’ profits.
The Aqua Nautilus team leveraged Shodan, a search engine for Internet-connected devices, to assess the scale of the threat. They identified over 800,000 publicly accessible PostgreSQL databases, underscoring the critical need for securing these systems against brute force attacks and potential exploitation.
The emergence of PG_MEM underscores the importance of proactive database security. Organizations should prioritize strong password policies, enforce multi-factor authentication, and conduct regular security audits to identify and address potential vulnerabilities. Additionally, deploying robust intrusion detection and prevention systems can help to identify and thwart malicious activity before it can cause significant damage.
For more detailed information on detecting and mitigating the PG_MEM threat, visit Aqua Nautilus’s full report on their website.
Related Posts:
- 86% of the compromised Google Cloud instances were used to perform cryptocurrency mining
- Security Flaw in PostgreSQL: CVE-2024-7348 Allows Arbitrary SQL Execution
- Unpatched PostgreSQL Servers at Risk of Arbitrary Code Execution Attacks