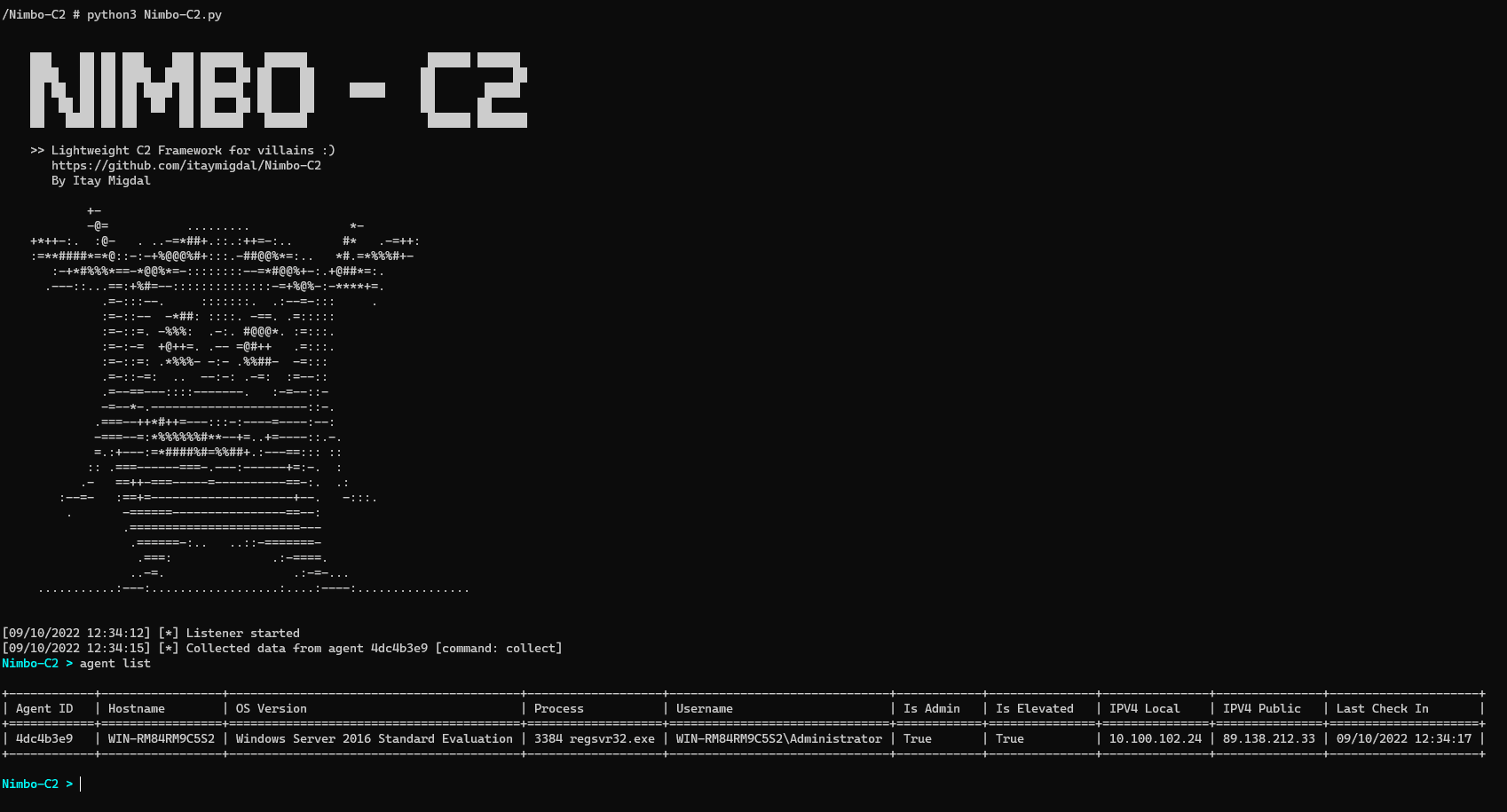
Nimbo-C2
Nimbo-C2 is yet another (simple and lightweight) C2 framework.

Nimbo-C2 agent currently supports Windows x64 only. It’s written in Nim, with some usage of .NET (by dynamically loading the CLR to the process). Nim is powerful, but interacting with Windows is much easier and robust using Powershell, hence this combination is made.
All server components are written in Python:
- HTTP listener that manages the agents.
- Builder that generates the agent payloads.
- Nimbo-C2 is the interactive C2 component that rule’em all!
Features
- Build EXE, and DLL payloads.
- Packing payloads using UPX and obfuscate the PE section names (UPX0, UPX1) to make detection and unpacking harder.
- Encrypted HTTP communication (AES in CBC mode, key hardcoded in the agent and configurable by the config.jsonc).
- Auto-completion in the C2 Console for convenient interaction.
- In-memory Powershell commands execution.
- File download and upload commands.
- Built-in discovery commands.
- Screenshot taking and clipboard stealing.
- Memory evasion techniques like NTDLL unhooking, ETW & AMSI patching.
- LSASS and SAM hives dumping.
- Shellcode injection.
- Persistence capabilities.
- UAC bypass methods.
- And more!
TODO
Modules
- Improve Unhooking and patching by using syscalls.
- Run .NET assemblies.
- Migrate to another process (Meterpreter-like).
- Getsystem.
- Collect installed software.
- Zip & exfiltrate folder.
- Find sensitive files by keywords / regex search.
Misc
- Develop Proxy awareness for the agent.
- Add option to sign PE agent with digital signature. Some very nice Github projects do that to lower detection.
- Support shellcode payload type.
- Support more packers.
Install & Use
Copyright (c) 2022 Itay Migdal