nmapAutomator: automate all of the process of recon/enumeration
nmapAutomator
A script that you can run in the background!
Summary
The main goal for the nmapAutomator script is to automate all of the processes of recon/enumeration that are run every time and instead focus our attention on real pen-testing.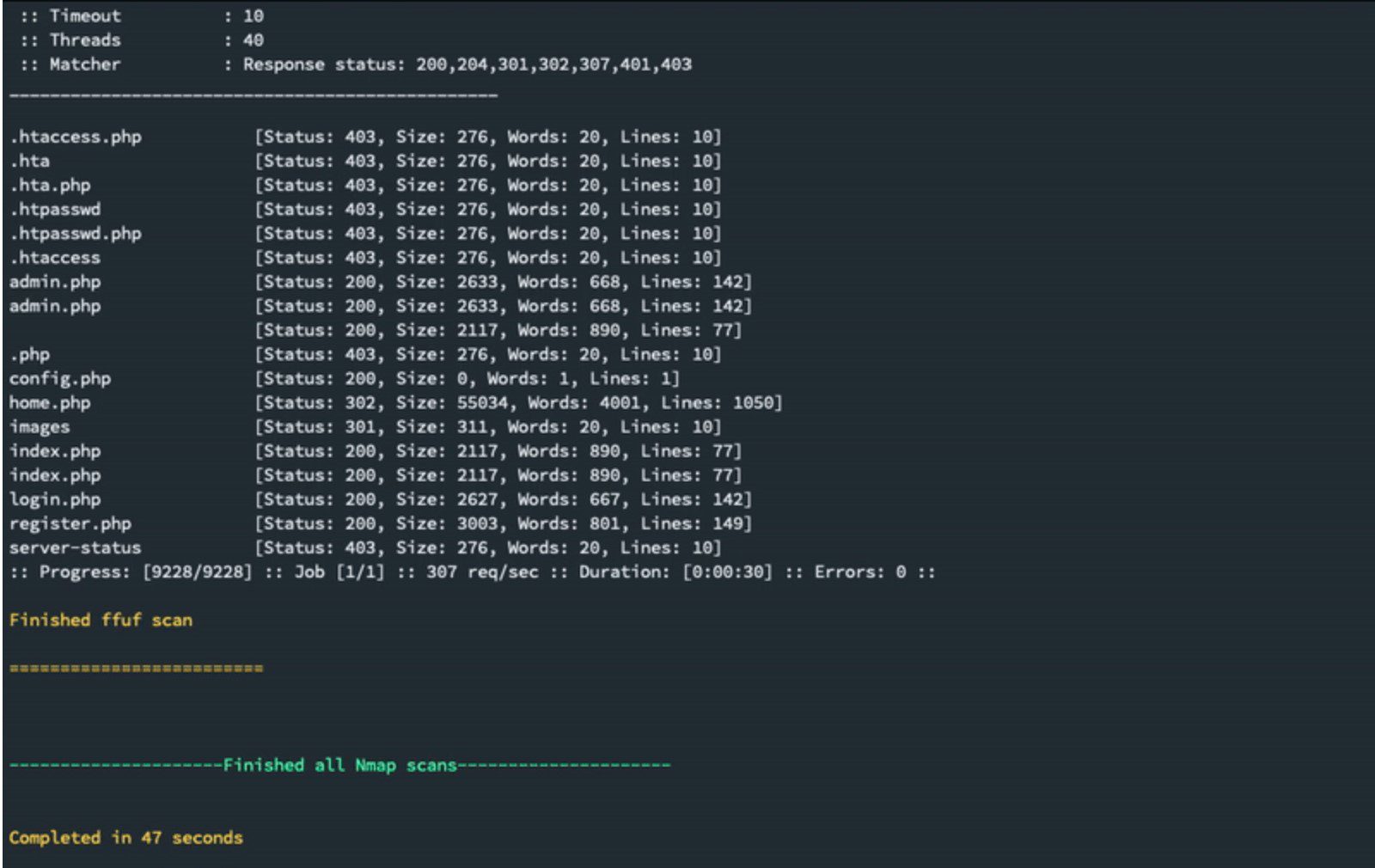
This will ensure two things:
1) Automate nmap scans. 2) Always have some recon running in the background.
Once initial ports are found ‘in around 10 seconds‘, we can start manually looking into those ports, and let the rest run in the background with no interaction from our side whatsoever.
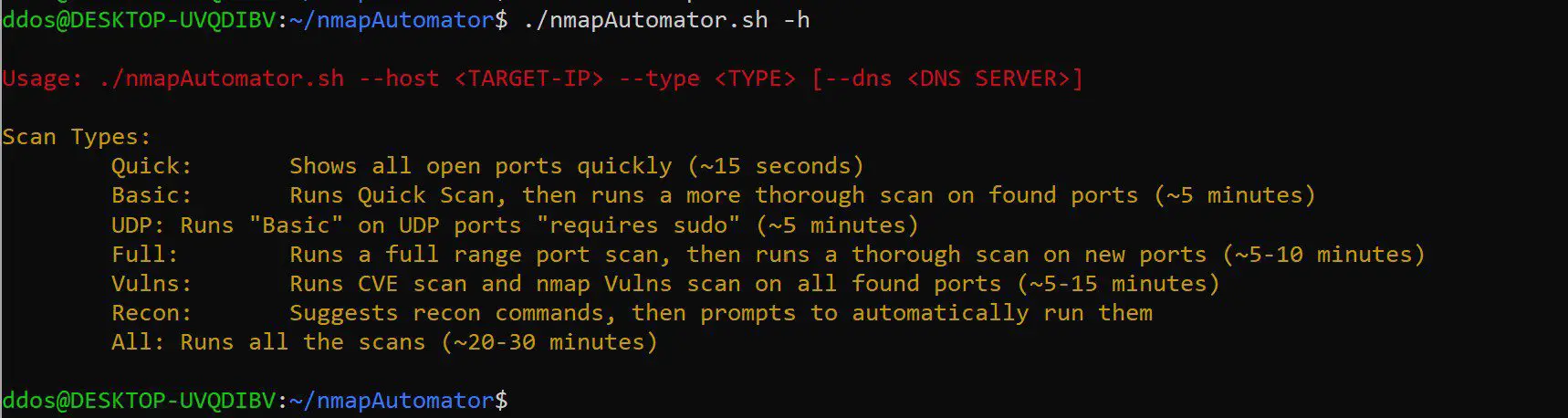
Features:
- Quick: Shows all open ports quickly (~15 seconds)
- Basic: Runs Quick Scan, then runs a more thorough scan on found ports (~5 minutes)
- UDP: Runs “Basic” on UDP ports (~5 minutes)
- Full: Runs a full range port scan, then runs a thorough scan on new ports (~5-10 minutes)
- Vulns: Runs CVE scan and nmap Vulns scan on all found ports (~5-15 minutes)
- Recon: Runs “Basic” scan “if not yet run”, then suggests recon commands “i.e. gobuster, nikto, smbmap” based on the found ports, then prompts to automatically run them
- All: Runs all the scans consecutively (~20-30 minutes)
Installation
Requirement
Gobuster v3.0 or higher, which we can install with:
sudo apt update
sudo apt install gobuster
or ffuf, which we can install with:
sudo apt update
sudo apt install ffuf
Other Recon tools used within the script include:
Install
git clone https://github.com/21y4d/nmapAutomator.git
sudo ln -s $(pwd)/nmapAutomator/nmapAutomator.sh /usr/local/bin/
Use
Example
Copyright (c) 2021 21y4d
Source: https://github.com/21y4d/





