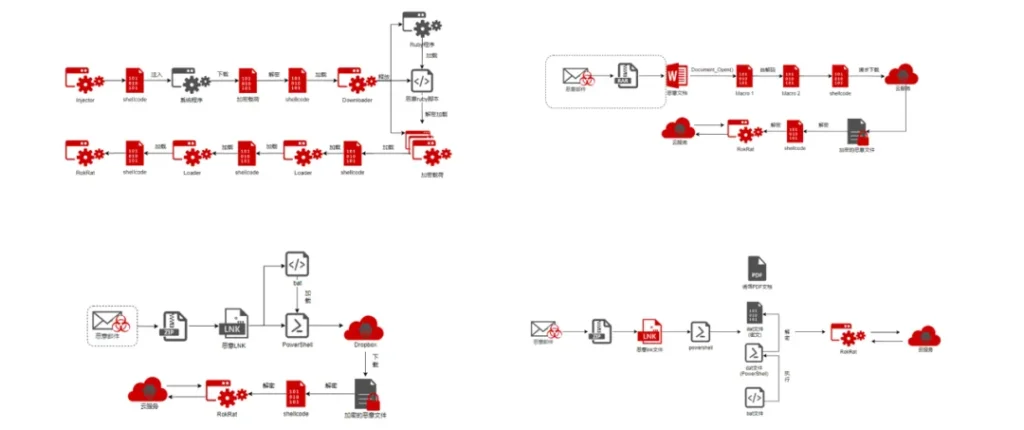
RokRat attack process | Image: 360 Threat Intelligence Center
A recent report from 360 Threat Intelligence Center has detailed the persistent cyber espionage activities of APT-C-28 (ScarCruft), also known as APT37 (Reaper) or Group123. Active since at least 2012, this North Korea-linked advanced persistent threat (APT) group continues to target South Korea and other Asian countries, focusing on strategic industries such as chemicals, electronics, aerospace, automotive, and healthcare.
ScarCruft’s attack campaigns have heavily relied on RokRat, a cloud-based remote access Trojan (RAT) that has been in use since 2016. RokRat enables the group to exfiltrate sensitive data, monitor victims, and maintain long-term access to compromised networks.
ScarCruft employs a stealthy, multi-stage infection strategy, leveraging LNK shortcut files to deliver fileless malware payloads:
- Spearphishing Campaigns: The group crafts highly customized phishing emails based on data collected from legitimate websites, ensuring higher victim engagement.
- LNK-Based Payload Delivery: Victims unknowingly execute an LNK file embedded in a compressed attachment, triggering a PowerShell script that extracts additional malicious components.
- RokRat Deployment: The payload includes encrypted shellcode that, once decrypted and executed, installs RokRat into the system memory to avoid detection.
ScarCruft continues to evolve its tactics by adopting new evasion techniques:
- Fileless execution: Malicious payloads reside only in memory, making them difficult to detect.
- Use of encrypted shellcode: Payloads are decrypted at runtime, bypassing static signature-based security solutions.
- Abuse of legitimate services: RokRat disguises its network communications by masquerading as Googlebot traffic.
ScarCruft maintains a resilient C2 infrastructure, utilizing multiple command sequences for system reconnaissance and data exfiltration. RokRat’s command set includes:
- Screen capture and keylogging
- Process enumeration and termination
- File exfiltration and deletion
- Downloading and executing secondary payloads
A notable shift in ScarCruft’s recent campaigns is the move away from cloud-based C2 servers toward embedding payloads directly into LNK files. This adaptation is likely in response to cloud security providers blocking malicious accounts.
Related Posts:
- ScarCruft Strikes: North Korea’s Cyber Espionage Against Media and Experts Unveiled
- Kaspersky Report: Energy Industry becomes the largest area affected by vulnerabilities in industrial automation systems
- New Android Banking Trojan Targets Indian Users Through Fake Apps